산업공학원 대학원의 꽃은 이상 탐지 아닐까 싶다. 기존에 공부하던 것들을 기반으로 이상탐지라(Anomaly Detection)이라는 새로운 분야를 공부하고 있다. 전반적인 기반을 다지고자 이 유튜브 영상와 영상에서 소개한 논문을 가져와서 하나하나 보려고 한다.

0. Abstract
- outlier detection 또는 novelty detection라고도 불리는 Anomaly detection는 수십 년 동안 다양한 연구 커뮤니티에서 지속적이고 활발한 연구 분야였음
- 여전히 고급 접근 방식이 필요한 몇 가지 독특한 문제 복잡성과 과제가 있음
- 최근 몇 년 동안 딥러닝을 통한 이상 탐지가 중요한 방향으로 떠오름.
- 3 가지 상위 수준 범주와 11가지 세분화된 방법 범주의 발전을 다루는 포괄적인 분류법을 사용하여 deep anomaly detection 연구를 조사함
- key intuitions, objective functions(목적 함수), underlying assumptions(기본 가정), advantages and disadvantages(장단점)을 검토하고 앞서 언급한 과제를 해결하는 방법에 대해 논의함
1. Introduction
이 review 논문은 아래 5가지를 집중적으로 다룬다.
-
Problem nature and challenges
: 우리는 이상 탐지의 기본이 되는 몇 가지 고유한 문제 복잡성과 그로 인해 발생하는 대부분의 미해결 과제에 대해 논의함 -
Categorization and formulation (분류 및 공식화)
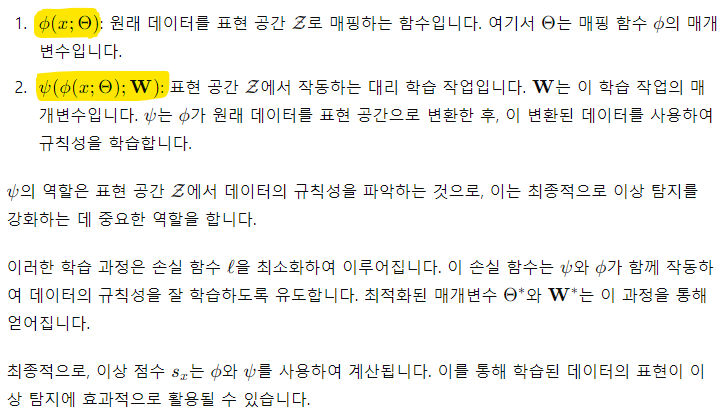
: 우리는 current deep anomaly detection methods을 3가지 principled frameworks(원칙)에 의해서 공식화했다.
2-1. deep learning for generic feature extraction (일반적인 특징 추출을 위한 딥 러닝)
2-2. learning representations of normality (정상성 표현의 학습)
2-3. end-to-end anomaly score learning (엔드투엔드 이상 점수 학습)
또한 11가지 모델링 관점에 따라 방법을 분류하기 위해 계층적 분류를 제시함.
🤔 end-to-end란?
딥러닝에서 end-to-end의 의미는 입력에서 출력까지 파이프라인 네트워크 없이 신경망으로 한 번에 처리하는 것을 의미합니다. 즉, 복잡한 파이프라인 없이 하나의 신경망으로 입력받은 것을 출력할 수 있다는 것입니다.
- end-to-end 장점
1) 신경망 모델로 입력 받은 값에 대한 출력 값을 찾아낼 수 있습니다.
2) 직접 파이프라인 설계할 필요가 없어집니다.- end-to-end 단점
1) 라벨링 된 데이터가 많이 필요합니다.
2) 메모리가 부족할 경우 사용할 수 없습니다.
3) 복잡한 문제를 해결하기에는 효율적이지 않습니다.
-
Comprehensive literature review
: 우리는 기계 학습, 데이터 마이닝, 컴퓨터 비전 및 인공 지능을 포함하여 여러 관련 커뮤니티의 주요 컨퍼런스 및 저널에서 다수의 관련 연구를 검토하여 연구 진행 상황에 대한 포괄적인 문헌 검토를 제시함. 심층적인 소개를 제공하기 위해 우리는 방법의 모든 범주에서 앞서 언급한 과제 중 일부를 해결하는 기본 가정, 목적 함수, 주요 직관 및 기능을 설명함. -
Future opportunities
: 우리는 가능한 미래의 기회와 그 기회가 관련 과제를 해결하는 데 미치는 영향에 대해 더 자세히 논의함. -
Source codes and datasets
: 우리는 경험적 비교 벤치마크를 제공하기 위해 거의 모든 범주의 방법에 대해 공개적으로 액세스할 수 있는 소스 코드 모음과 실제 예외 사항이 포함된 수많은 실제 데이터 세트를 요청함.
2. Anomaly Detection: Problem Complexities and Challenges
2.1. Major Problem Complexities
- Unknownness : Anomalies are associated with many unknowns.(이상 현상은 기존에 알려져 있지 않은 갑작스러운 행동, 데이터 구조, 분포 등 많은 알려지지 않은 요소와 연관되어 있다.)
- Heterogeneous anomaly classes : Anomalies(변칙)은 irregular(불규칙적)이므로 한 변칙 클래스는 다른 변칙 클래스와 완전히 다른 비정상적인 특성을 나타낼 수 있다.
- Rarity and class imbalance : 이상 현상은 일반적으로 데이터의 압도적인 비율을 차지하는 일반적인 인스턴스와 달리 드문 데이터 인스턴스다.
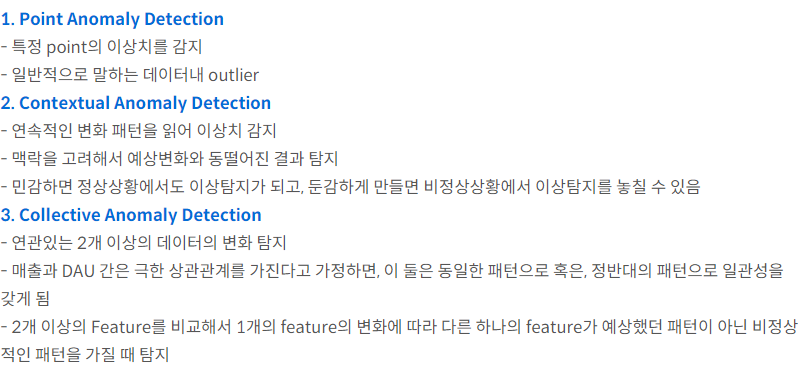
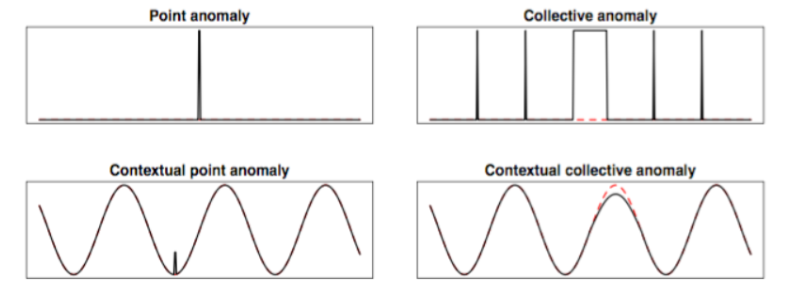
- Diverse types of anomaly : 완전히 다른 3 가지 유형의 anomaly 현상이 조사되었다.
(a) Point anomalies
: 부분의 다른 개별 인스턴스에 비해 변칙적인 개별 인스턴스
(b) Conditional anomalies(Contextual anomalies)
: 맥락을 보았을 때, 특정 상황에서 비정상 현상을 보이는 경우
(c) Group anomalies(Collective anomalies)
: 다른 데이터 인스턴스에 비해 전체적으로 비정상적인 데이터 인스턴스의 하위 집합, 집단의 개별 point는 이상값이 아닐 수도 있음.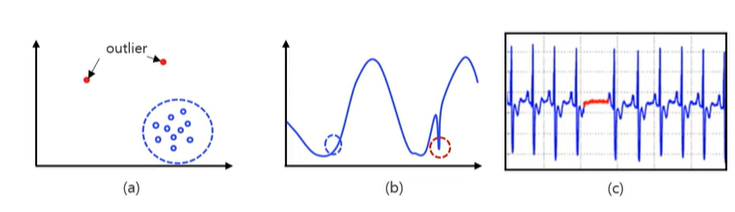
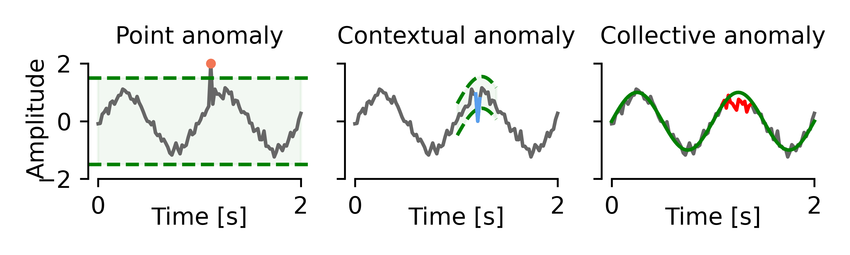
❗outlier 종류
2.2. Main Challenges Tackled by Deep Anomaly Detection
Deep Anomaly Detection가 몇 가지 중요한 역할을 할 수 있는 다음 문제들은 대부분 해결되지 않았습니다.
- CH1: Low anomaly detection recall rate
수년에 걸쳐 수많은 이상 탐지 방법이 도입되었지만 현재의 최첨단 방법(비지도 방법)또한 실제 데이터 세트에서는 여전히 높은 오탐률이 발생하는 경우가 많다. 오탐을 줄이고 검색 재현율을 높이는 방법은 가장 중요하면서도 어려운 과제 중 하나이다. 특히 이상 징후를 발견하지 못하는 데 드는 막대한 비용이 발생한다.
- CH2: Anomaly detection in high-dimensional and/or not-independent data.
- Anomalies(변칙 현상)은 저차원 공간에서는 명백히 비정상적인 특성을 나타내지만, 고차원 공간에서는 숨겨져 눈에 띄지 않게 된다. → High-dimensional anomaly detection has been a long-standing problem.
- 시간적, 공간적, 그래프 기반 및 기타 상호 의존 관계와 같이 서로 의존할 수 있는 인스턴스에서 이상 현상을 탐지하는 것도 어려움이 있음.
- CH3: Data-efficient learning of normality/abnormality
- 대규모의 레이블이 지정된 이상 데이터를 수집하는 데 따른 어려움과 비용으로 인해 fully supervised anomaly detection는 정상 및 이상 클래스 모두에 레이블이 지정된 훈련 데이터의 가용성을 가정하기 때문에 종종 비실용적
- 그래서, 지난 10년간 unsupervised anomaly detection 연구가 집중됨. → 그러나,unsupervised anomaly detection은 실제 이상 현상에 대한 사전 지식이 없고, distribution of anomalies에 대한 가정에 크게 의존함.
- 반면, 레이블이 지정된 정상 데이터와 일부 레이블이 지정된 이상 데이터를 수집하는 것은 어렵지 않은 경우가 많음. → 실제로는 쉽게 접근할 수 있는 레이블이 지정된 데이터를 최대한 활용하는 것이 종종 제안됨.
- [Sol.1] Semi-supervised anomaly detection
: 레이블이 지정된 정상 훈련 데이터 세트를 가정함 - [Sol.2] Weakly-supervised anomaly detection
: anomaly label을 불완전하게 가지고 있다고 가정(anomalies에 대해서 부분적/불완전, 부정확한 레이블을 가진다고 가정)
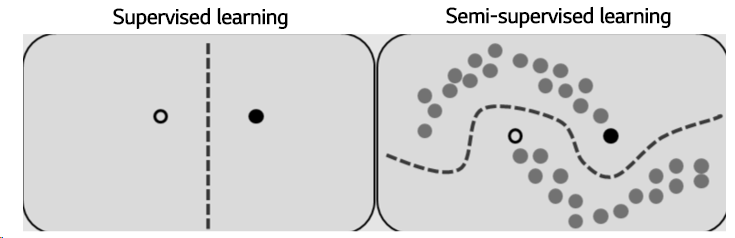
🤔 Semi-supervised learning 이란?
적은 labeled data가 있으면서 추가로 활용할 수 있는 대용량의 unlabeled data가 있다면 semi-supervised learning을 고려할 수 있다. Semi-supervised learning (준지도학습)은 소량의 labeled data에는 supervised learning을 적용하고 대용량 unlabeled data에는 unsupervised learning을 적용해 추가적인 성능향상을 목표로 하는 방법론이다. 이런 방법론에 내재되는 믿음은 label을 맞추는 모델에서 벗어나 데이터 자체의 본질적인 특성이 모델링 된다면 소량의 labeled data를 통한 약간의 가이드로 일반화 성능을 끌어올릴 수 있다는 것이다. (아래의 그림에서도 확인할 수 있듯이 왼쪽에 supervised learning과 오른쪽 semi-supervised learning을 비교해보면 supervised learning의 decision boundary는 사실상 optimal하지 않다. unlabeled data를 활용하여 데이터 자체의 분포를 잘 모델링하면 오른쪽 semi-supervised learning 그림처럼 더 좋은 decision boundary를 얻을 수 있다.)
- CH4: Noise-resilient anomaly detection.
Many weakly/semi-supervised anomaly detection method은 레이블이 지정된 훈련 데이터가 깨끗하다고 가정 -> 실수로 반대 클래스 레이블로 레이블이 지정된 noisy한 인스턴스에 취약할 수 있음. -> 이러한 경우 비지도 방법을 대신 사용할 수 있지만 이는 실제 레이블이 지정된 데이터를 활용하지 못함.
Noise-resilient model은 보다 정확한 감지를 위해 레이블이 지정되지 않은 데이터를 활용할 수 있습니다.
(여기의 노이즈는 레이블이 잘못 지정된 데이터이거나 레이블이 지정되지 않은 경우을 말함)
- CH5: Detection of complex anomalies.
기존 방법의 대부분은 point anomalies에 대한 것이며 conditional anomaly and group anomaly에는 점 이상과 전혀 다른 행위를 나타내기 때문에 사용할 수 없다.
-> conditional/group anomalies 개념을 이상 측정/모델에 통합하는 것입니다.
또한 현재 방법은 주로 단일 데이터 소스에서 이상을 감지하는 데 중점을 두는 반면, 많은 애플리케이션에서는 -> 다차원 데이터, 그래프, 이미지, 텍스트 및 오디오 데이터와 같은 multiple heterogeneous data sources를 사용하여 이상을 감지해야 한다.
- CH6: Anomaly explanation
Anomalies로 보고된 rare data 인스턴스는 사기 탐지 및 범죄 탐지 시스템에서 과소대표된 그룹과 같이 데이터에 표시된 소수 그룹에 대한 알고리즘 편향 가능성(possible algorithmic bias)을 초래할 수 있습니다.
->특정 데이터 인스턴스가 anomaly로 식별되는 이유에 대한 직접적인 단서를 제공하는 anomaly explanation algorithm을 갖추는 것입니다.
(대부분의 이상 탐지 연구는 탐지 정확도에만 초점을 맞추고 식별된 이상에 대한 설명을 제공하는 기능을 무시합니다. 특정 탐지 방법에서 anomaly explanation 을 도출하는 것은 특히 복잡한 모델의 경우 아직 해결되지 않은 문제입니다. 본질적으로 해석 가능한 이상 탐지 모델을 개발하는 것도 중요하지만, 모델의 해석 가능성과 효율성의 균형을 잘 맞추는 것이 주요 과제로 남아 있습니다.)
Deep Learning Methods vs. Traditional Methods in Anomaly Detection.
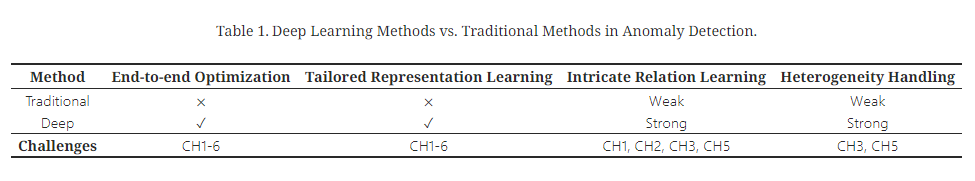
3.Addressing the Challenges with Deep Anomaly Detection
3.1. Preliminaries


3.2. Categorization of Deep Anomaly Detection
해당 영역에 대한 철저한 이해를 위해 모델링 관점에서 Deep Anomaly Detection을 3 가지 주요 범주와 11개의 세분화된 범주로 분류하는 계층적 분류법을 도입합니다.
(각 방법 범주에서 해결할 수 있는 감지 문제도 Challenge로 제시됩니다)
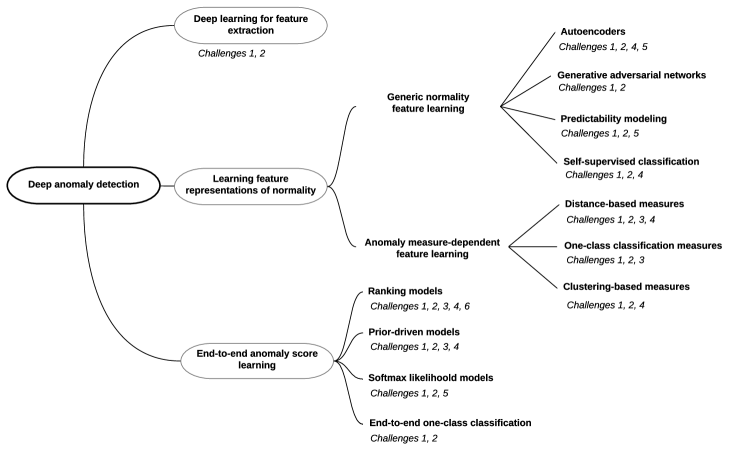
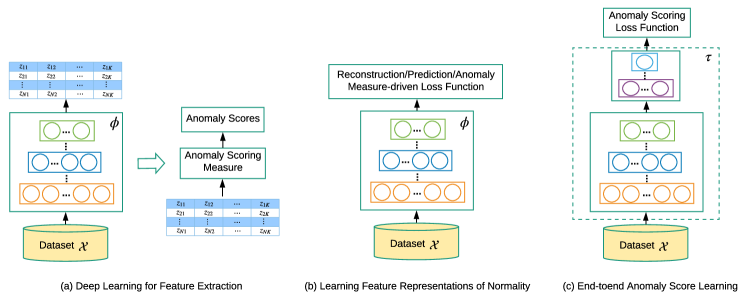
4. Deep Learning for Feature Extraction
- 목표 : 고차원 및/또는 비선형 분리 가능한 데이터에서 저차원 특징 표현(feature representations)을 추출하는 것
- 특징 추출(Feature Extraction)과 이상치 점수 매기기(anomaly scoring)는 서로 완전히 분리되고 독립적
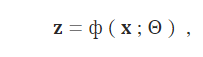
(normally 𝐷 ≫ 𝐾)
-
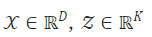
-
차원축소(PCA, random projection) 같은 방법론과 비교했을 때, 딥러닝 기술은 의미가 풍부한 특징과 비선형 특징 관계를 추출하는 데 훨씬 더 나은 능력을 보여주었다.
-
assumption : 딥러닝 모델에 의해 추출된 feature representation은 변칙적인 상황과 정상적인 상황을 구분하는 데 도움이 되는 식별 정보(discriminative information)를 보존합니다.
-
AlexNet, VGG 및 ResNet 등을 통해 저차원 특징을 추출한다. 이미지 데이터, 비디오 데이터와 같은 복잡한 고차원 데이터의 이상 탐지에서 탐색된 방법론이다.
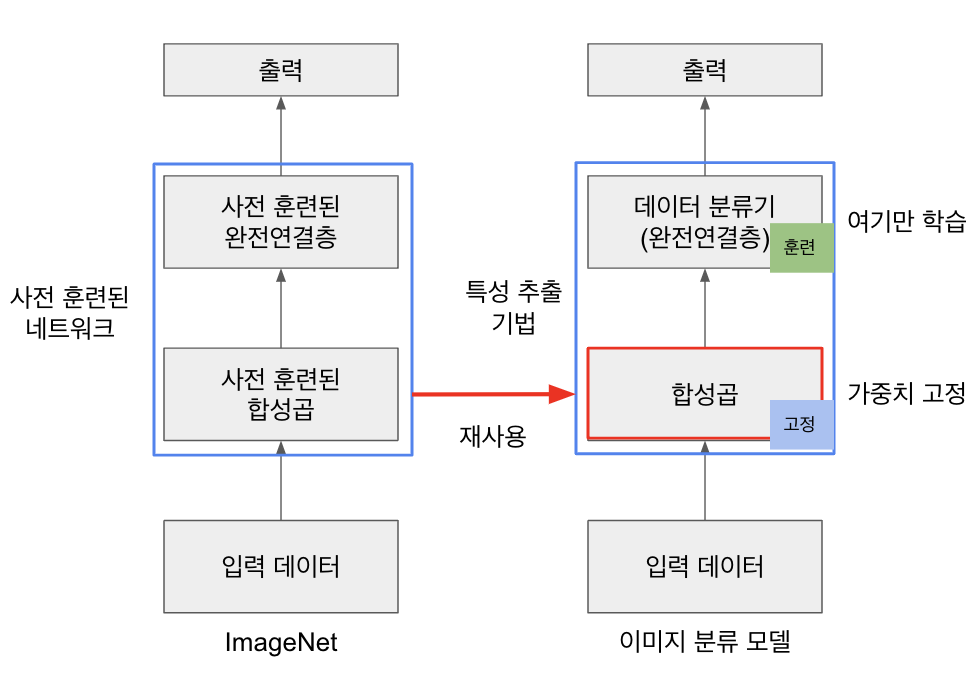
특성 추출 기법
- 사전 학습된 모델을 사용하여 새로운 데이터셋에서 특성을 추출하는 기법입니다.
- 특성 추출 기법은 사전 학습된 모델에서 이미지 데이터를 입력으로 받아서 합성곱층(convolutional layer)을 통해 이미지의 특성을 추출합니다. 이렇게 추출된 특성은 최종적으로 완전 연결층(fully connected layer)을 통해 분류됩니다.
- 새로운 데이터셋에서 특성 추출을 위해서는, 먼저 사전 학습된 모델의 합성곱층을 고정(freeze)시키고, 완전 연결층 부분만 새로운 데이터셋에 맞게 변경하여 학습합니다.
- 따라서, 새로운 데이터셋에서는 이미지의 카테고리를 결정하는 부분인 마지막 완전 연결층만 학습하고, 나머지 합성곱층 계층들은 사전 훈련된 가중치를 그대로 사용하여 학습되지 않도록 고정합니다.
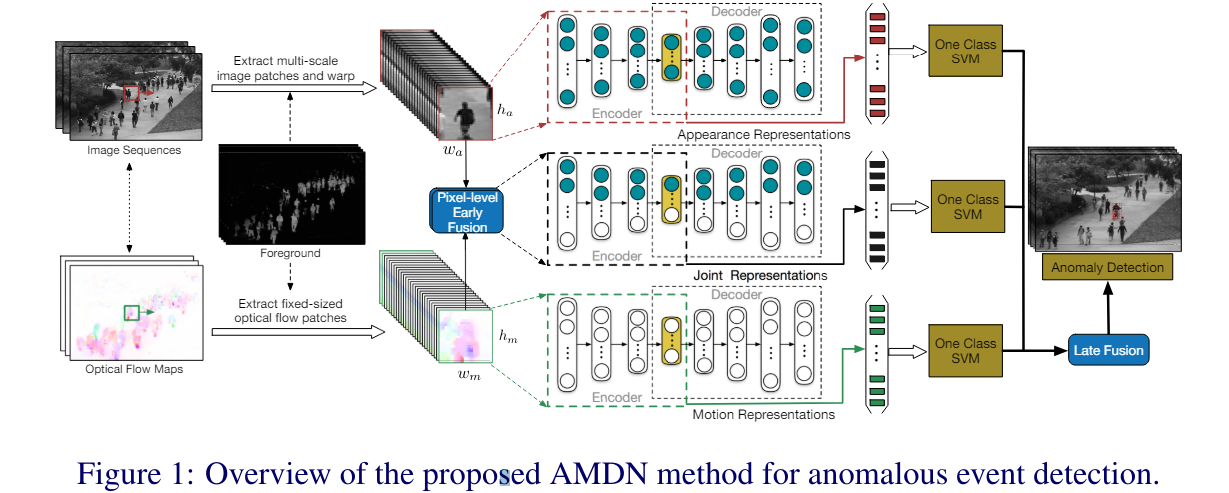
Unmasking framework for online anomaly detection
- key idea : 연속된 두 비디오 시퀀스를 구별하기 위해 이진 분류기를 반복적으로 훈련시키면서, 각 단계에서 가장 구별력 있는 특징(discriminant feature)을 점진적으로 제거하는 것입니다. => 비디오의 각 장면(Scene)이 비정상적인지 여부를 판단하는 알고리즘
(인용한 논문은 따로 벨로그에 정리하였다.)- ILSVRC 벤치마크에서 사전 훈련된 VGG 모델 (135)는 이러한 목적을 위해 표현적인 외관 특징(appearance features)을 추출하는 데 효과적
Downstream Anomaly Scoring에 pre-trained model이 아닌 deep feature extraction model을 명시적으로 훈련하는 것
- 논문에서는 특징 표현을 자동으로 학습하기 위해 딥러닝 네트워크를 활용하는 Appearance and Motion DeepNet (AMDN)을 제안
- 스택된 노이즈 제거 오토인코더(stacked denoising autoencoders)를 사용하여 외모와 동작 특징 및 결합된 표현(초기 융합)을 각각 학습
- 학습된 표현을 기반으로, 3개의 일류 SVM(one-class SVM) 모델을 사용하여 각 입력의 이상 점수를 예측하며, 이러한 점수들은 후기 융합 전략을 통해 통합되어 최종 이상 감지를 수행
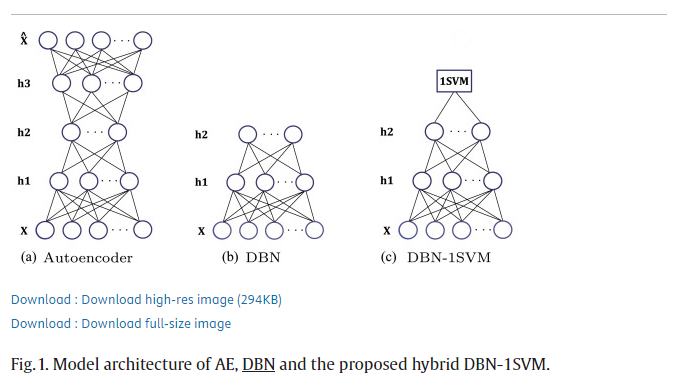
Linear one-class SVM + DBN
논문에서 One-class Support Vector Machines은 Deep Belief net(DBN)에서 생성된 고차원 테이블 형식 데이터의 저차원 표현에 대한 이상 탐지를 활성화하는 데 사용.
❗장단점
-
장점 :
(i) state-of-the-art(pre-trained) deep model과 기성 이상 탐지기를 쉽게 사용
(ii) Deep feature extraction은 널리 사용되는 선형 방법보다 더 강력한 차원 축소를 제공
(iii) 심층 모델 및 탐지 방법이 공개적으로 제공되므로 구현이 쉬움 -
단점 :
(i) 완전히 분리된 feature extraction 과 anomaly scoring은 종종 최적이 아닌 이상 점수(suboptimal anomaly scores)로 이어짐.
(ii) Pre-trained deep model은 일반적으로 특정 유형의 데이터로 제한
5. Learning Feature Representations of Normality
5.1.Generic Normality Feature Learning

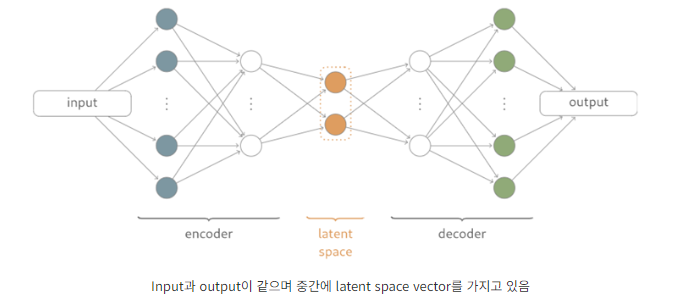
5.1.1.Autoencoders
[오토인코더 목표] : 데이터 인스턴스를 잘 재구성할 수 있는 저차원 특징 표현 공간을 학습하는 것
- 데이터 압축이나 차원 축소를 위해 널리 사용됨
- 이 기술을 이상 탐지에 사용하는 이유는 학습된 특징 표현(feature representation)이 재구성 오류를 최소화하기 위해(minimize reconstruction errors) 데이터의 중요한 규칙성(important regularities of the data)을 학습하도록 강제되기 때문
- 이상치는 재구성하기 어려워 => 큰 재구성 오류를 가지게 됨
[오토인코더 가정] : 정상 인스턴스(Normal instance)는 압축된 공간(compressed space)에서 이상치보다 더 잘 재구성될 수 있습니다
(오토인코더에 대한 설명은 여기 블로그을 들어가서 한 번 보고오는게 좋다.)
5.2.Anomaly Measure-dependent Feature Learning
🔖 Reference
본 논문
딥러닝에서의 end-to-end
semi-supervised learning
[pytorch] 전이 학습 - 특성 추출 기법 (Feature Extraction)
[Paper Review] Unmasking the abnormal events in video
[논문리뷰] Restricted Boltzmann Machine(RBM)와 Deep Belief Network(DBN