The post is personal notes I have taken while reading Computer Networking (James F. Kurose, Keith W. Ross) - 5th edition.
1. The Internet
Internet: a type of computer network
Internet in terms of basic hardware/software
- Host/End systems: equipment used to access at a remote site via network
- (ex) TV, laptop, console, phone, etc.
- connected by a network of communication links & packet switches
- Communication link: communication channel connecting devices for data transmission
- made of various physical media (ex) copper wire, fiber optics, etc.
- different links transmit at different rates
- Transmission rate
- measured in bits/second
- Process
- One end system has data to send to another end system
- The sending system segments data & adds header bytes to each segment
- Resulting packets (package of information) are sent through network to the destination end system
- In the destination end system, the packets are reassembled into original data
- Packet switch: takes a packet arriving on one of its incoming communication links & forwards that packet on one of its outgoing communication links
- Router: a type of packet switch
- typically used in network core
- Link-layer switches: a type of packet switch
- typically used in access networks
- Routers & link-layer switches both forward packets toward ultimate destinations
- Router: a type of packet switch
- Route/Path: the sequence of communicationl inks & packet switches traversed by a packet from sending to receiving end system
- Internet Service Provider (ISP): providers through which end systems access the Internet
- (ex) residential ISP (local cable, telephone company), corporate/university ISP, etc.
- each ISP is a network of packet switches & communication links
- provides a variety of types of network access to the end systemes
- provides Internet access to contect providers
- connects websites directly to the Internet
- Since Internet connects end systems to each other, ISPs (provideing access to end systems) must also be interconnected
- tiers
- lower-tier ISP: interconnected thru national/international upper-tier ISPs
- upper-tier ISP: high-speed routers interconnected w/ high-speed fiber-optic links
- each and every ISP network:
- is managed independently
- runs the IP protocol
- conforms to naming/address conventions
- Protocol: controls sending/receiving of information w/i the Internet
- Transmission Control Protocol (TCP)
Internet Protocol (IP): specifies format of packets that are sent/received among routers & end systems
- Transmission Control Protocol (TCP)
- Internet standards
- developed by the Internet Engineering Task Force (IETF)
- Requests for Comments (RFC): IETF standards documents
- started as general requests for comments
- to solve network/protocol design problems
- started as general requests for comments
A services description
Internet as an infrastructure that provides services to applications
- Distributed applications: involve multiple end systems that exchange data w/ each other
- Application Programming Interface (API): specifies how a software piece running on one end system asks the Internet infrastructure to deliver data to a specific destination software piece running on another
- Internet API: a set of rules that the sending software must follow so that the Internet can deliver the data to the destination software
Protocol
- Network protocol: defines the format & order of messages exchanged b/w communicating entities and the actions taken on the transmission and/or receipt of a message/event
- all activity in the Internet that involves communiating remote entities is governed by a protocol
- (ex) the URL of web pages
2. The Network Edge
- End systems sit at the edge of the Internet
- (ex) desktop computers, servers, mobile computers, etc.
- aka hosts: they host application programs
- 2 categories: clients and servers
- Client: desktop, mobile PCs
- Server: store & distribute web pages, stream video, relay e-mail, etc.
- Client-server model: client program running on one end system that requests & receives a service from a server program running on another end system
- (ex) web, e-mail, file transfer, remote login, etc.
- a type of distributed applications b/c client runs on one computer and server runs on another
- Peer-to-Peer (P2P): end systems interact & run programs that perform both client & server functions
Access networks
- Access networks: physical links that connect an end system to the first router (= edge router) on a path from the end system to another distant end system
Dial up
- Dial up: the user's software dials an ISP's phone number & makes a traditional phone connection w/ the ISP
- At the other end of the connection, a modem in the ISP converts analog sign back into digital form for input to the ISP's router
- Drawbacks
- very slow - max rate of 56 kbps
- ties up a user's ordinary phone line: while a phone call is being made, other family members can't receive/make phone calls
- DSL, cable dominate the broadband residential access methods
DSL
- When DSL is used, a customer's local telephone provider is also its ISP
- Each customer's DSL modem uses the existing telephone line to exchange data w/ a digital subscriber line access multiplexer (DSLAM)
- telephone line carries both data & telephone signals simulatenously
- (Customer) a splitter separates arriving data & telephone signals & forwards data signal to the DSL modem & (Telco) DSLAM separates data & phone signals and sends the data into the Internet
- Advantages
- transmit & receive data at much higer rates
- asymmetric access: a typical DSL customer has different transmission rate ranges for upstream/downstream
- simulatenously talk on phone & access the Internet
- transmit & receive data at much higer rates
Cable
- Cable head end: broadcasts television channels thru a distribution network of coaxial cable & amplifiers to residences
- Cable Internet access uses the cable television company's existing cable television infrastructure
- different from using telco's existing local telephone infrastructure (DSL/dial-up)
- each neighbor junction supports 500~5000 homes
- aka Hybrid Fiber Coax (HFC): both fiber & coaial cable are employed in this system
- Cable modems: special modems required for cable Internet
- an external device connecting to the home PC thru an Ethernet port
- devides the HFC network into 2 channels (downstream/upstream)
- downstream channel typically allocated at a higher transmssion rate than upstream (asymmetric)
- Shared broadcast medium
- every packet sent by the head end travels downstream on every link to every home
- every packet sent by a home travels on the upstream channel to the head end
- (ex) If many users download a video file on the downstream, the actual speed of download will be slower than aggregate cable downstream rate
- A distributed multiple-access protocol is necessary to coordinate transmissions & avoid collisions
- A reasonably dimensioned HFC network may provide higher transmission rates than DSL
Fiber-To-The-Home (FTTH)
- fiber optics offer higher transmission rates than twisted-pair copper wire/coaxial cable
- Direct fiber: the simplest optical distribution network
- one fiber leaving the CO (Central Office) for each home
- high bandwith: each customer gets its own dedicated fiber all the way to the CO
- Non-direct fiber: each fiber goes through single path until they near homes & split into individual customer-specific fibers
- Active optical networks (AONs)
- = switched Ethernet
- Passive optical networks (PONs)
- each home has optical network terminator (ONT), connected by dedicated optical fiber to a neighborhood splitter
- splitter combines a number of homes (~100) onto a single, shared optical fiber
- shared fiber connects to an optical line terminator (OLT) in the telco's CO
- OLT provides conversion b/w optical & electrical signals and connects to the Internet via a teclo router
- At home, users connect a home router to the ONT & access the Internet via this router
- all packets sent from OLT to the splitter are replicated at the splitter
- Active optical networks (AONs)
- can provide Internet access rates in the gigabits per second rage
- BUT most FTTH ISPs provide different rate offerings
- higher rates > more expensive
- BUT most FTTH ISPs provide different rate offerings
- optical fibers carry broadcast television services & traditional phone services
Ethernet
- In corporate/universities, a local area network (LAN) is typically used to connect an end system to the edge router
- Ethernet: most prevalent access LAN technology in corporate/university networks
Wifi
- Wireless LAN: wireless users transmit/receive packets to/from an access point that in turn is connected to wired Internet
- Wide-area wireless access networks: packets are transmitted to a base station over same wireless infrastructure used for cellular telephony
- base station managed by cellular network provider
- Wide-area wireless access networks: packets are transmitted to a base station over same wireless infrastructure used for cellular telephony
Wide-Area Wireless Access
- For wide-area access, users use the cellular phone infrastructure, accessing base stations
- Third generation (3G) wireless: provides packet-swithced wide-area wireless Internet
WiMAX
- operates independently of cellular network
Physical media
- Physical medium: through which electromagnetic waves/optical pulses move to send bits
- does not have to be same type for each transmitter-receiver pairs
- (ex) twisted-pair copper wire, coaxial cable, etc.
- Two categories: guided media, unguided media
- Guided media: waves are guided along a solid medium (ex) fiber-optic cable, twisted-pair copper wire, coaxial cable
- Unguided media: waves propagate in the atmosphere & in outerspace (ex) wireless LAN, digital satellite channel
- costs of physical media are minor compared w/ other networking costs
Twisted-Pair Copper Wire
- least expensive
- most commonly used guided transmission medium
- wires are twisted together to reduce the elctrical interference from near similar pairs
- wire pair is a single communication link
- Unshiled twisted pair (UTP)
- common for computer networks within building, residential Internet access
- data rates depend on thickness of wire & distance b/w transmitter/receiver
Coaxial Cable
- consists of 2 concentric copper conductors
- common in cable television systems
- can be guided shared medium
Fiber Optics
- optical fiber: thin/fexible medium that conducts pulses of lights
- each pulse representing a bit
- each fiber can support big bit rates
- immune to electromagnetic interference
- preferred long-haul guided transmission media
- overseas link, backbone of the Internet, etc.
- high cost
Terrestrial Radio Channels
- radio channels carry signals in the electromagnetic spectrum
- require no physical wire to be installed
- can penetrate walls
- provide connectivity to a mobile user
- can carry a signal for longer distances
- depends on the propagation environment & distnace of signal movement
Satellite Radio Channels
- communication satellite: links Earth-based microwave tarnsmitter/receivers (aka ground stations)
- the satellite receives transmissions on one frequency band & regenerates the signal using a repeater & transmits the signal on another frequency
- 2 types: geostationary satellites, low-earth orbiting satellites
- Geostationary satellites
- permanently remain above the same spot on Earth
- satellite placed in orbit at 36K km above Earth
- big propagation delay
- often used in areas w/o access to DSL/cable-based Internet access
- Low-earth orbiting (LEO) satellites
- placed much closer to Earth
- do not remain on one spot - rotate Earth
- can communicate w/ each other or ground stations
- Geostationary satellites
3. The Network Core
Circuit switching & Packet switching
Circuit-switched networks
- resources needed (buffers, link transmission rate) to provide for communication b/w the end systems are reserved for the duration of communication session b/w end-systems
- (ex) ubiquitous telephone networks: network must establish a connection b/w sender & receiver before sender can send the info
- Circuit: when the network establishes the circuit, it reserves a constant transmission rate in the network's links for the duration of connection
- the sender transfers the data to the receiver at the guaranteed constant rate
Packet-switched networks
- the sender transfers the data to the receiver at the guaranteed constant rate
- session's messages use the resources on demand
- may have to wait for access to a communication link
- (ex) Internet - packet is sent to network w/o reserving any bandwith > if one link is congested b/c other packets need to be transmitted over the link simultaneously, then packet will have to wait
Not all telecommunication networks can be neatly classifed as either
Circuit Switching
- each link has n circuits > each link can support n simultaneous connections
- End-to-end connection: when two hosts want to communicate, the network establishes an end-to-end connection
- for a host to send messages to another, the network must first reserve one circuit on each of two linnks
- b/c each link has n circuits, for each link used by the connection, the connection gets a fraction 1/n of the link's bandwith for the duration of the connection
- Multiplexing in circuit-switched networks
- a circuit in a link is implemented w/ either frequency-division multiplexing (FDM) or time-division multiplexing (TDM)
- FDM: frequency spectrum of link is divide dup among connections established across the lnik
- the link dedicates a frequency band to each connection for the duration of the connection
- bandwith: the width of frequency bands
- TDM:
- time is divided into frames of fixed duration
- each frame is divided into a fixed number of time slots
- when network establishes a connection across alink, network dedicates one time slot in every frame to this connection
- slots are dedicated for the sole use of that connection
- Circuit switching can be wasteful b/c the dedicated circuits are idle during silent periods & cannot be used by other ongoing connections
- establishing end-to-end circuits & reserving end-to-end bandwith is complicated & requires complex signaling software
Packet Switching
- Packet: smaller chunks of data that long messages are broken into by the source
- each travles through communication links & packet switches b/w source & destination
- transmitted over each communication link at a rate equal to full transmission rate of the lnk
- Store-and-forward transmission: the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link
- used by most packet switches at inputs to the links
- a store-and-forward delay at the input to each link along packet's route
- Each packet link has multiple links attached
- Output buffer: stores packets that the router is about to send into that link
- packet switch has one output buffer for each attached link
- plays a key role in packet switching
- if an arriving packet needs to be transmitted across a link but finds the link busy with another transmission, the arriving packet must wait in the output buffer
- resulting query delays: variable & depend on the level of congestion in the network
- buffer space is finite > may be full > packet loss
- either arriving packet or one of the already-queued packets will be dropped
- Output buffer: stores packets that the router is about to send into that link
Packet switching vs. Circuit switching: Statiscal Multiplexing
Packet switching
- strength
- better sharing of bandwith than circuit switching
- simpler/more efficient/less costly to implement
- allocates link use on demand > link transmission capacity shared on a packet-by-packet basis only among users who have packets that need to bransmitted over the link > Statistical multiplexing of resources
- drawbacks
- is not suitable for real-time services b/c of its variable/unpredictable end-to-end delays
How do packes make their way through packet-switched networks
A router takes a packet arriving on one of its attached coummunication links & forwards that packet onto another of its attached communication links
- How does the router determine the link to forward to?
- Forwarding table: maps (portions of) destination addresses to outbound links
- When a packet arrives at a router, the router examines the address & searches its table & directs the packet
- Forwarding table: maps (portions of) destination addresses to outbound links
- How do forwarding tables get set?
- Internet has a number of special routing protocols that are used to set forwading tables
ISPs & Internet Backbones
ISP can provide wired/wireless connectivity using array access technologies (ex) DSL, cable, FTTH, Wifi, etc.
- The Internet is a network of networks
- Tierred hierarchy of ISPs
- access ISPs - bottom
- tier-2 ISP
- regional/national coverage
- connects to few tier-1 ISP
- customer of tier-1 ISP
- tier-1 ISPs - top
- aka Internet backbone networks- provider of tier-2 ISP: charges its customer ISP a fee (depends on transission rate)
- can be tier-2 providers: sell Internet access directly to end users/lower-tier ISP
- high link speeds
- able to forward packets at high rates
- directly connected to each of the other tier-1 ISPs
- connected to many tier-2 ISPs & customer networks
- international in coverage
- Peer ISP: two ISPs are directly connected to aech other at same tier
- Points of Presence (POPs): the points at which the ISP connects to other ISPs within an ISP's network
- a group of one or more routers in the ISP's network at which routers in other ISPs can connect
4. Delay, Loss, and Throughput in Packet-Switched Networks
Overview of delay in Packet-switched networks
Packet starts in a host (source), passes through a series of routers, and ends at another host (destination).
- In this journey, packet suffers several types of delays
- Total node delay: includes nodal processing delay, queuing delay, transmission delay, propagation delay
- Processing delay:
- time required to examine packet's header & determine where to direct packet
- time required to check for bit-level errors in the packet that occurred in transmitting the packet's bits from the upstream node to router A
- Queuing delay:
- as the packet waits to be transmitted onto the link
- length of queuing delay depends on: # of earlier-arriving packets that are queued, waiting for transmission across link
- = 0: empty queue & no other packet being transmitted
- = long: heavy traffic & many other packets wiating
- Transmission delay
- aka store-and-forward delay
- = (length of packet in bits)/(transmission rate of the link b/w routers in bits/sec)
- amount of time required to push (=transmit) all of the packet's bits into thel ink
- Propagation delay: time required to propagate from the begining of the link to router B
- once a bit is pushed into the link, it needs to propagate to router B
- the bit propagates at the propagation speed of link
- depends on the physical medium of the link - = (distance b/w routers) / (propagation speed)
Transmission vs. Propagation delay
- Transmission delay: amount of time required for the router to push out the packet
- function of the packet's length & transmission rate of the link
- irrelevant to distance b/w routers
- time required to get to your turn
- Propagation delay: the time it takes a bit to propagate from one router to next
- function of distance b/w 2 routers
- irrelevant to packet's length or transmission rate of link
- time required to move to next
Queuing delay Packet loss
- Queuing delay depends on:
- rate at which traffic arrives at the queue
- transmission rate of the link
- nature of the arriving traffic: whether traffic arrives periodically or in bursts
- Traffic intensity
- a - average rate at which packets arrive at the queue (packets/sec)
- R - transmission rate: rate at which bits are pushed out of queue (bits/sec)
- L - all packets consists of L bits
- La - average rate at which bits arrive at the queue
- Traffic intensity = La / R
- traffic intensity > 1: average rate of bits arriving at queue > rate of bits transmitting from queue
- queue will increase w/o bound
- as traffic intensity approaches 1, average queuing delay increases rapidly
- Your system must have traffic intensity no grater than 1
- queue will increase w/o bound
- traffic ntensity <= 1
- periodic arrival of packets: packet arrives every L/R seconds
- every packet will arrive at an empty queue > no queue delay
- arrival in bursts > significant average queuing delay
- periodic arrival of packets: packet arrives every L/R seconds
- traffic intensity > 1: average rate of bits arriving at queue > rate of bits transmitting from queue
Packet loss
- When packet arrives to a full queue, a router will drop that packet > packet will be lost
- From an end-system perspective, a packet loss will look like a packet having been transmitted into network core but never emerging from network at destination
- traffic intensity increases > fraction of lost packets increases
- performance at node is measured in terms of delay & probability packet loss
End-to-End Delay
Total delay from source to destination
When there are (N-1) routers b/w source & destination and the network is uncongested
(end-to-end delay) = N((processing delay) + (transmission delay) + (propagation delay))
- transmission delay = L/R (L: packet size, R: transmission rate out of each router/source host)
Traceroute
- Traceroute: program that can run in any Internet host
- user specifies destination hostname
- program in the source host sends multiple special packets toward the destination
- packets pass through routers on their way to destination
- when router receives one of these special packets, it sends back to the source a short message containing the name & address of router
- Traceroute helps the source reconstruct the route taken by packets & determine the round-trip delays to routers
Throughput in Computer Networks
End-to-end throughput: critical performance measure
- Instantaneous throughput: rate at which Host B is receiving the file (bits/sec)
- Average throughput
- constraining factor for throughput of Internet: access network
5. Protocol layers & Their service models
Layered architecture
Each layer provides its service by (1) performing certain actions within that layer and by (2) using the services of the layer directly below it
- As long as the layer provides the same service to the layer above it & uses the same services from the layer below it, the remainder of the systems remains unchanged
- the ability change implementation of service w/o affecting other components of the system
Protocol layering
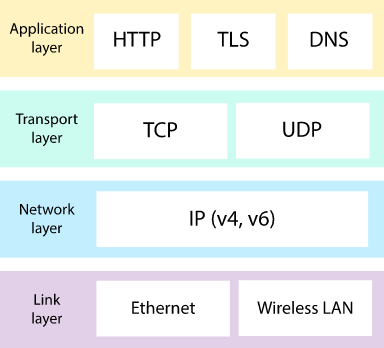
- protocols organized in layers
- Physical/Data link layers: responsible for handling communication over a specific link
- typically implemented in a network interface card assocated w/ a given link
- Network layer: mixed implementation of hardware & software
- a layer protocol can be distributed among end systems, packet switches, other components
- Physical/Data link layers: responsible for handling communication over a specific link
- Advantages of protocol layering
- provides a structured way to discuss system components
- modularity facilitates updating system components
- provides a structured way to discuss system components
- Drawbacks of protocol layering
- one layer may duplicate lower-layer functionality
- functionality at one layer may need info that is present only in one layer > violates goal of separation of layers
- Protocol stack: the protocols of various layers
Internet protocol stack: includes physical, link, network, transport, and application layers
- Application layer: network applications & their application-layer protocols are here
- includes many protocols (ex) HTTP protocol (provides for Web document request/transfer), SMTP (provides for the transfer of emails), FTP (provides for the trasnfer of files b/w two end systems)
- distributed over multiple end systems
- the application in one end system using the protocol to exchange packets of info (=message) w/ the application in another end system
- Transport layer: transports application-layer messages b/w application endpoints
- Segment: a transport-layer packet
- 2 transport protocols in the Internet: TCP & UDP
- TCP: provides a connection-oriented service to its applications
- includes guaranteed delivery of application-layer messages to destination & flow control
- breaks long messages into shorter segments
- provides a congestion-control mechanism so that a source throttles its transmission rate when network is congested
- UDP: provides a connectionless service to its applications
- no reliability, no flow control, no congestion control
- TCP: provides a connection-oriented service to its applications
- Network layer: responsible for moving network-layer packets from one host to another
- Datagram: network-layer packets
- Transport-layer protocol in a source host passes a transport-layer segment & a destination address to the network layer
- Network layer provides the service of delivering the segment to the transport layer in the destination host
- includes IP Protocol (defines the fields in the datagram & how the end systems/routers act on these fields)
- all Internet components that have a network layer must run the IP protocol (there's only one)
- contains routing protocols that determine routes that datagrams take b/w sources & destinations
- there are many routing protocols
- Link layer: moves entire frames from one one network element to an adjacent network element
- At each note, the network layer passes the datagram down to the link layer, which delivers the datagram to the next node along the route
- At the next route, the link layer passes datagram up to the network layer
- service depends on the specific link-layer protocol employed over the link
- (ex) Ethernet, Wifi, Point-to-Point Protocol (PPP)
- Frame: link-layer packets
- At each note, the network layer passes the datagram down to the link layer, which delivers the datagram to the next node along the route
- Physical layer: moves individual bits within the frame from one node to the next
- protocols depend on link & actual transmission medium of link
Open Systems Interconnection (OSI) model: a protocol stack
- seven layers: application, presentation, session, transport, network, data link, physical layer
- Presentation layer: provides services that allow communcating applications to interpret the meaning of data exchanged
- data compression/encryption/description
- Session layer: delimits & synchronizes data exchange
- builds a checkpointing & recovery scheme
Messages, Segments, Datagrams, Frames
Process
- at sending host, an application-layer message is passed to the transport layer
- transport layer takes the message & appends additional information (ka transport-layer header information) that will be used by receiver-side transport layer
- transport-layer segment = application-layer message + transport-layer header information
- Thus, the transport-layer segment encapsulates the application-layer message
- the transport layer passes the segment to the network layer
- Network layer adds network-layer header information (ex) source & destination end system address > network-layer datagram
- datagram is passed to link layer
- link layer adds its own link-layer header information > link-layer frame
At each layer, a packet has two types of fields: header fields & payload field
- payload: packet from the layer above
6. Networks under attack
Malware - malwares infect devices (ex) spyware, etc.
- Botnet: compromised host may be enrolled in a network of other similarly compromised devices
- controlled & leveraged for spam, attacks, etc.
- Self-replicating: once malware infects one host, it seeks entry into other hosts over the Internet
- can spread very fast
Types of malware
- Virus: mawlare that require some form of user interaction to infect user's device
- Worm: malware that can enter a device w/o any explicit user interaction
- Trojan horse: malware that is a hidden part of some otherwise useful software
Denial-of-service (DoS) attacks
DoS attacks render a network, host, or other piece of infrastructure unusable by legitimate users
- can attack web/email/DNS servers, institutional networks
3 categories of DoS - Vulnerability attack
- sends well-crafted messages to a vulnerable application/operating system running on a targeted host
- if the right sequence of packets is sent to a vulnerable application/operating system, the service can stop or the host can crash
- Bandwidth flooding
- attacker sends a deluge of packets to the targeted host
- so many packets that the target's access link becomes clogged > prevents legitimate packets from reaching server
- attacker has to send traffic at approximately access rate of host to damage
- Connection flooding
- attacker establishes a large number of half-open/fully open TCP connections at the target host
- host become so bogged down w/ these bogus connections that it stops accepting legitimate connections
Distributed DoS (DDoS) attack
- attacker controls multiple sources & has each source blaset traffic at the target
- aggregate traffic rate across all the controlled sources need to be approximately access rate
- much harder to detect/defend against
Packet sniffer
- Wifi-connected Internet is vulnerable to receivers that can obtain a copy of every packet being transmitted
- Packet sniffer: a passive receiver that records a copy of every packet that flies
- can be depoyed in wired/wireless environments
- does not inject packets into the channel (difficult to detect)
IP spoofing
IP spoofing: ability to inject packets into the Internet w/ a false source address
- the user can masquerade as another user
- solution: end-point authentication > allows us to determine if a message originates from where we think it does
Man-in-the-middle attacks
Man-in-the-middle attacks: bad guy inserted into the communication path b/w 2 communicating entities
- bad guy can sniff/inject/modify/delete all packets that pass b/w entities
- attacks integrity of the data
7. History of Computer Networking and the Internet
Packet-switches
W/ the increasing importance of computers & advent of timeshared computers, the question of how to hook computers together so that they can be shared among physically distributed users
Interface message processors (IMPs): early packet switches
Proliferation of networks
- new standard host protocol for ARPAnet
- DNS: maps b/w human-readable Internet name and its 32-bit IP address
- changes to TCP to implement host-based congestion control
Internet explosion
emergence of the World Wide Web application > Internet to homes/businesses
- platform for enabling/deploying hundreds of applications
- key components: HTML, HTTP, web server, browser
Recent
- increasing ubiquity of high speed public Wifi networks
- increasing DoS attacks on web servers > development of intrusion detection systems
- P2P networking: exploits resources in users' computers & has significant autonomy from central servers
