Defense in Depth - strategy of using many layers of varying security mechanisms to frustrate attackers.
Cryptography - "Secret writing"
Cipher - an algorithm that converts plain text to into ciphertext.
Encryption - process of making text secret
Decryption - reverse process
Substitution ciphers
Replace every letter in a message with somthing else according to a translation.
- Caesar cipher - shift the letters in a message forward by three places.
Permutation ciphers
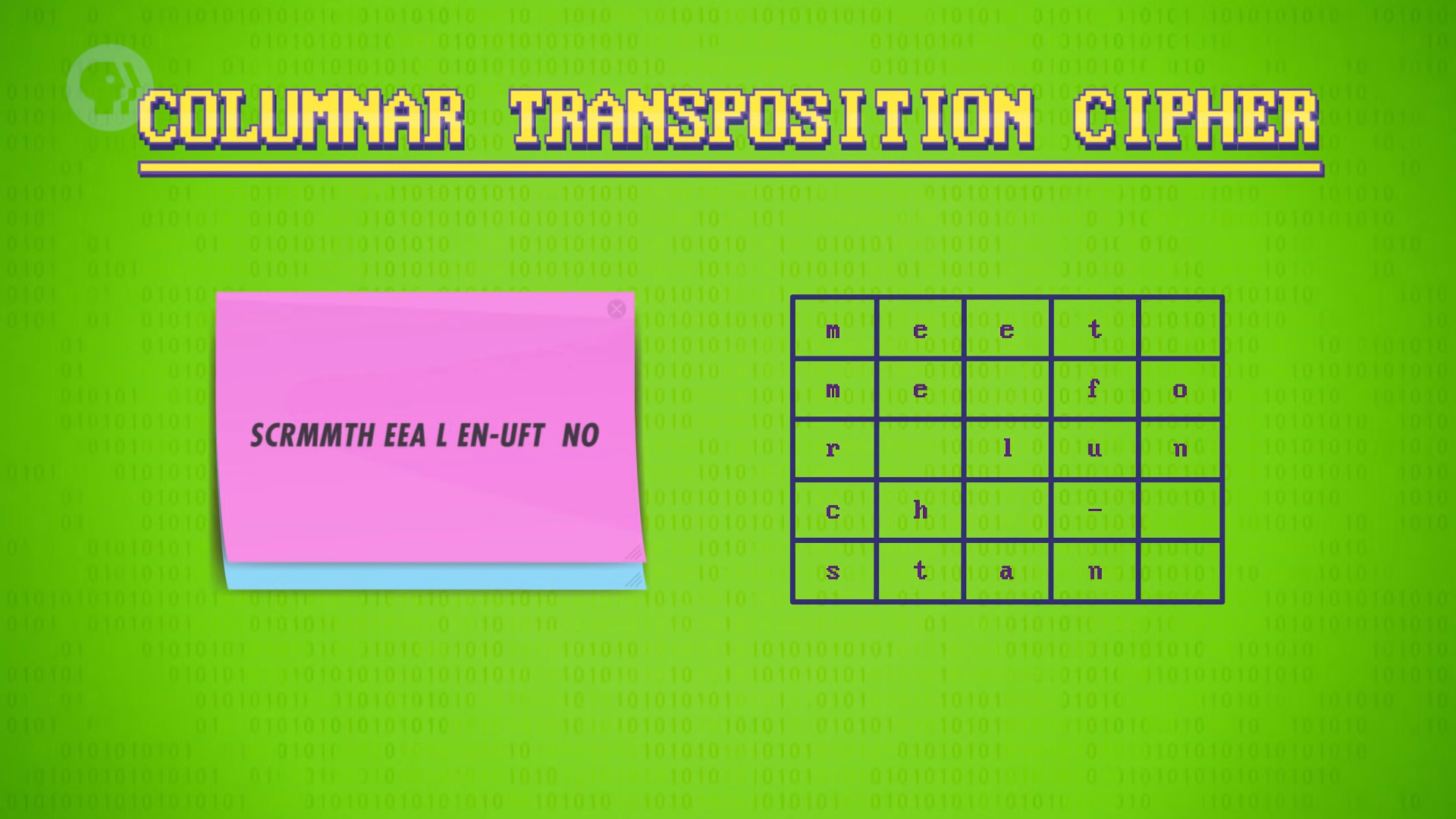
- Columnar transposition cipher
By the 1990's, cryptography was mechanized in the form of encryption machines
- The most famous - Germna Enigma
With the advent of computers, cryptography moved from hardware into software.
Data Encryption Standard - developed by IBM and the NSA in 1977.
- Used binary keys that were 56 bits long.
In 2001, the Advanced Encryption Standard was finalized and published.
- Uses 128, 192, or 256 bits
- AES chops data up into 16-byte blocks, and then applies a series of substitutions and permutations, based on the key value, plus some other operations to obscure the message, and this process is repeated ten or more times for each block.
- AES is used everywhere from encrypting files, transmitting data over WiFi with WPA2, accessing websites using HTTPS, etc.
Key exchange
An algorithm that lets computers agree on a key without ever sending one.
- Done in one-way functions - mathmatical operations that are very easy to do in one direction, but hard to reverse.
- Diffie-Hellman Key Exchange - use modular exponentiation for the one-way function.

- These keys that can be used by both sender and receiver, to encrypt and decrypt messages, are called symmetric keys because the key is the same on both sides.
Asymmetric encryption
There are two different keys - often public and private key.
- Knowing the public key only lets you encrypt, but not decrypt.
- A digital public key can encrypt something that can only be decrypted with a private key.
- Reverse is possible too: encrypting something with a private key that can be decrypted with public key
- This is used for signing, where a server encrypts data using their private key. Anyone can decrpyt it using the server's public key.
- This acts like an unforgeable signature, as only the owner, using their private key, can encrypt.
- The most popular asymmetric encryption technique used today is RSA
Vocabuary
- Cipher - 암호
- Analogy - 비유
- unforgeable - 위조 불가능한
- imposter - 사칭하는 사람, 사기꾼
31개의 댓글
Frequent goes to here i will discuss the obvious way to appreciate it on your attempt, which often is why Now i am viewing the internet site day-to-day, in search of completely new, useful facts. Quite a few, many thanks! fototapety dla dzieci
Fabulous post, you have denoted out some fantastic points, I likewise think this s a very wonderful website. I will visit again for more quality contents and also, recommend this site to all. Thanks.slot dana
What a fantabulous post this has been. Never seen this kind of useful post. I am grateful to you and expect more number of posts like these. Thank you very much.olxtoto login
Bless you designed for presenting modern up-dates concerning the anxiety, As i watch for browse alot more. https://1winregindonesia.com
Really I enjoy your site with effective and useful information. It is included very nice post with a lot of our resources.thanks for share. i enjoy this post. judi slot
Awesome article, it was exceptionally helpful! I simply began in this and I'm becoming more acquainted with it better! Cheers, keep doing awesome! Slot Terbaru
Great article with excellent idea!Thank you for such a valuable article. I really appreciate for this great information..bandar toto online
Positive site, where did u come up with the information on this posting? I'm pleased I discovered it though, ill be checking back soon to find out what additional posts you include. bandar mawartoto
Thanks for posting this info. I just want to let you know that I just check out your site and I find it very interesting and informative. I can't wait to read lots of your posts.Chikiiapk.com
I am happy to find this post very useful for me, as it contains lot of information. I always prefer to read the quality content and this thing I found in you post. Thanks for sharing.koitotog
It is truly a well-researched content and excellent wording. I got so engaged in this material that I couldn’t wait reading. I am impressed with your work and skill. Thanks.toto togel 4D
It’s appropriate time to make some plans for the future and it is time to be happy. I have read this post and if I could I wish to suggest you few interesting things or advice. Perhaps you could write next articles referring to this article. I desire to read even more things about it!link gacor
I haven’t any word to appreciate this post.....Really i am impressed from this post....the person who create this post it was a great human..thanks for shared this with us.koitoto login
This is just the information I am finding everywhere. Thanks for your blog, I just subscribe your blog. This is a nice blog..miototo
I havent any word to appreciate this post.....Really i am impressed from this post....the person who create this post it was a great human..thanks for shared this with us.keytoto daftar
I admit, I have not been on this web page in a long time... however it was another joy to see It is such an important topic and ignored by so many, even professionals. I thank you to help making people more aware of possible issues.togel 4d
I admire this article for the well-researched content and excellent wording. I got so involved in this material that I couldn’t stop reading. I am impressed with your work and skill. Thank you so much.토렌트 사이트 순위
A very awesome blog post. We are really grateful for your blog post. You will find a lot of approaches after visiting your post.timur188
I found so many interesting stuff in your blog especially its discussion. From the tons of comments on your articles, I guess I am not the only one having all the enjoyment here! keep up the good work...slot 4d
You completed a few fine points there. I did a search on the subject and found nearly all persons will go along with with your blog.Automated crypto trader
This particular is usually apparently essential and moreover outstanding truth along with for sure fair-minded and moreover admittedly useful My business is looking to find in advance designed for this specific useful stuffs…신용카드 현금화
Excellent article. Very interesting to read. I really love to read such a nice article. Thanks! keep rocking.소액결제 현금화
You have a real talent for writing unique content. I like how you think and the way you express your views in this article. I am impressed by your writing style a lot. Thanks for making my experience more beautiful.bandar toto
You have a real talent for writing unique content. I like how you think and the way you express your views in this article. I am impressed by your writing style a lot. Thanks for making my experience more beautiful.olxtoto
Admiring the time and effort you put into your blog and detailed information you offer!..hptoto situs
I wanted to thank you for this excellent read!! I definitely loved every little bit of it. I have you bookmarked your site to check out the new stuff you post.prediksi togel china
This is my first time visit to your blog and I am very interested in the articles that you serve. Provide enough knowledge for me. Thank you for sharing useful and don't forget, keep sharing useful info:slot online






Frequent goes to here i will discuss the obvious way to appreciate it on your attempt, which often is why Now i am viewing the internet site day-to-day, in search of completely new, useful facts. Quite a few, many thanks