1.How many ClusterRole exist on the cluster?
- How many ClusterRoles do you see defined in the cluster?
kubectl get clusterroles | wc -l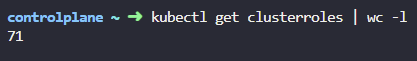
3. How many ClusterRoleBindings exist on the cluster?
kubectl get clusterrolebindings | wc -l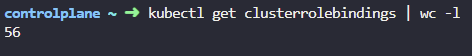
4. What namespaces is the cluster-admin clusterrole part of?
kubectl describe clusterrole cluster-admin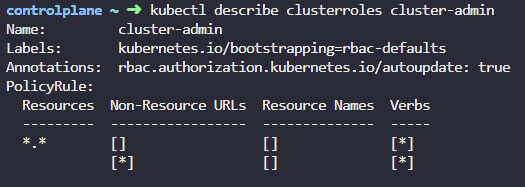
5. What user/groups are the cluster-admin role bound to?
The ClusterRoleBinding for the role is with the same name.
kubectl describe clusterrolebinding cluster-admin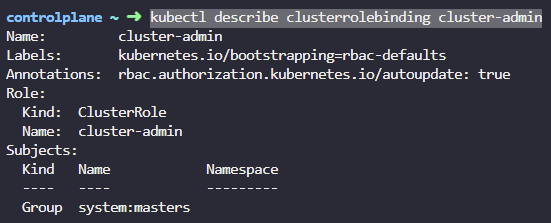
6.What level of permission does the cluster-admin role grant?
Inspect the cluster-admin role's privileges
kubectl describe clusterrole cluster-admin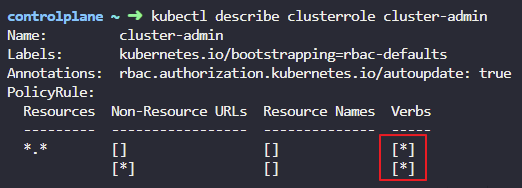
7. A new user michelle joined the team. She will be focusing on the nodes in the cluster. Create the required ClusterRoles and ClusterRoleBindings so she gets access to the nodes.
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: node-admin
rules:
- apiGroups: [""]
resources: ["nodes"]
verbs: ["get", "watch", "list", "create", "delete"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: michelle-binding
subjects:
- kind: User
name: michelle
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: node-admin
apiGroup: rbac.authorization.k8s.io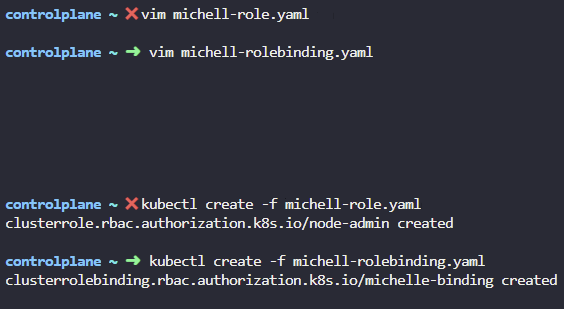
8. michelle's responsibilities are growing and now she will be responsible for storage as well. Create the required ClusterRoles and ClusterRoleBindings to allow her access to Storage.
Get the API groups and resource names from command kubectl api-resources. Use the given spec:
- ClusterRole: storage-admin
- Resource: persistentvolumes
- Resource: storageclasses
- ClusterRoleBinding: michelle-storage-admin
- ClusterRoleBinding Subject: michelle
- ClusterRoleBinding Role: storage-admin
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: storage-admin
rules:
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "watch", "list", "create", "delete"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "watch", "list", "create", "delete"]
----------------------------------------------------------
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: michelle-storage-admin
subjects:
- kind: User
name: michelle
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: storage-admin
apiGroup: rbac.authorization.k8s.io
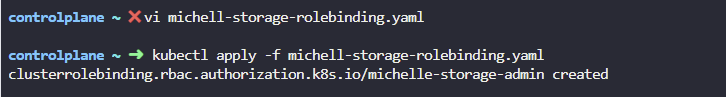
7번 문제와 비슷
https://kubernetes.io/docs/reference/access-authn-authz/rbac/
