- Inspect the environment and identify the authorization modes configured on the cluster.
Check the kube-apiserver settings
k get po -n kube-system
k describe po -n kube-system kube-apiserver-controlplane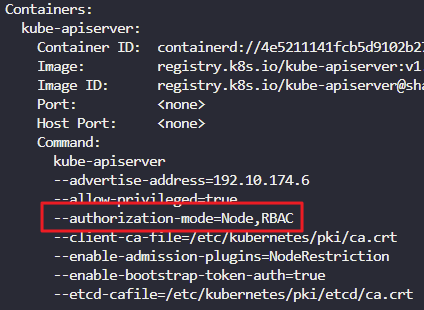
2. How many roles exist in the default namespace?
k get roles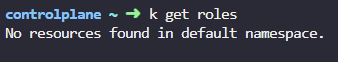
3. How many roles exist in all namespaces together?
k get roles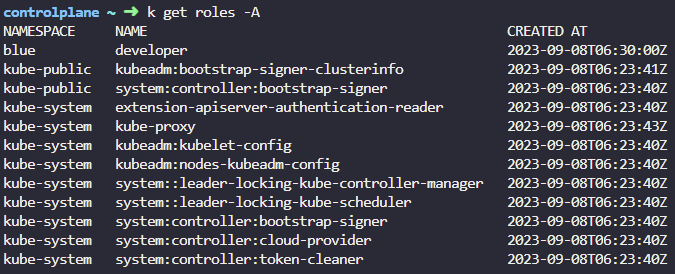
4. What are the resources the kube-proxy role in the kube-system namespace is given access to?
k describe role kube-proxy -n kube-system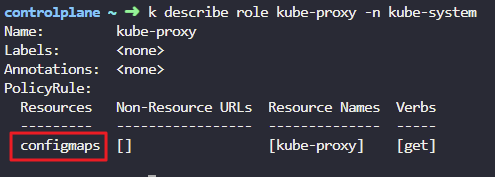
5. What actions can the kube-proxy role perform on configmaps?
k describe role kube-proxy -n kube-system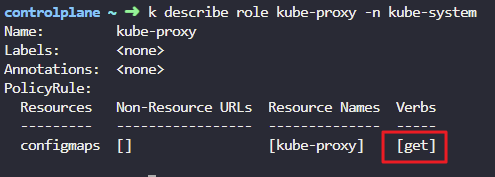
6. Which of the following statements are true?
kube-proxy role can get details of configmap object by the name kube-proxy only- Which account is the kube-proxy role assigned to?
k describe rolebinding kube-proxy -n kube-system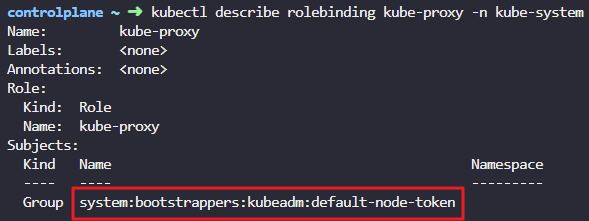
8. A user dev-user is created. User's details have been added to the kubeconfig file. Inspect the permissions granted to the user. Check if the user can list pods in the default namespace.
Use the --as dev-user option with kubectl to run commands as the dev-user.
kubectl get pods --as dev-user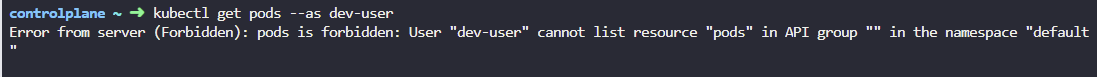
9. Create the necessary roles and role bindings required for the dev-user to create, list and delete pods in the default namespace.
Use the given spec:
- Role: developer
- Role Resources: pods
- Role Actions: list
- Role Actions: create
- Role Actions: delete
- RoleBinding: dev-user-binding
- RoleBinding: Bound to dev-user
k create role developer --namespace=default --verb=list,create,delete --resource=pods
k create rolebinding dev-user0binding --namespace=default --role=developer --user=dev-user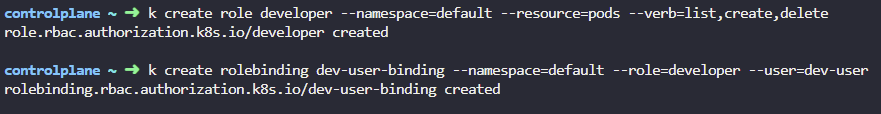
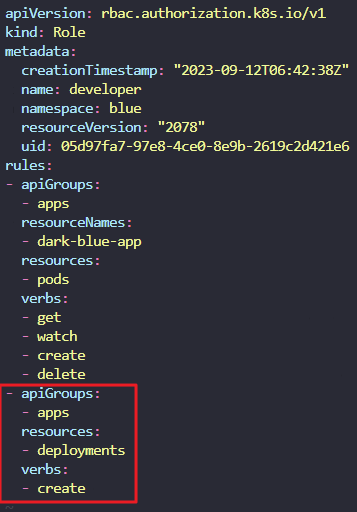
- A set of new roles and role-bindings are created in the blue namespace for the dev-user. However, the dev-user is unable to get details of the dark-blue-app pod in the blue namespace. Investigate and fix the issue.
We have created the required roles and rolebindings, but something seems to be wrong.
k get role -n blue
k edit roles developer -n blue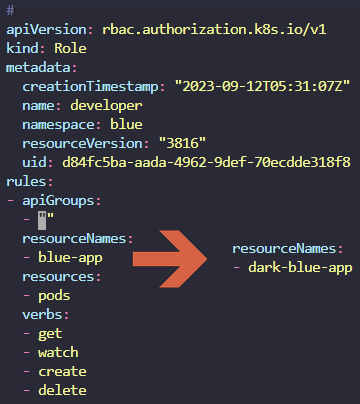
11. Add a new rule in the existing role developer to grant the dev-user permissions to create deployments in the blue namespace.
Remember to add api group "apps".
permissions added to create deployments?
k edit role developer -n blue
- apiGroups:
- apps
resources:
- deployments
verbs:
- create