IT Security
1.[IT-Security] Chapter 1. IT Security Context

IT 보안에 대한 배경지식에 대해 알아보자
2023년 2월 9일
2.[IT-Security] Chapter 2. Cryptography and Cryptosystems, part I
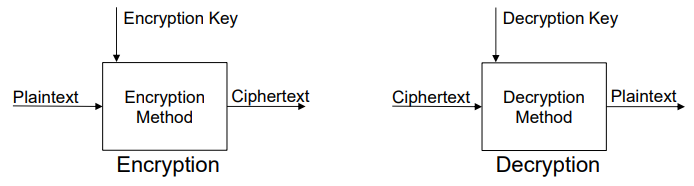
Cryptography and Cryptosystems, part I
2023년 2월 9일
3.[IT-Security] Chapter 3. Cryptography and Cryptosystems, part II
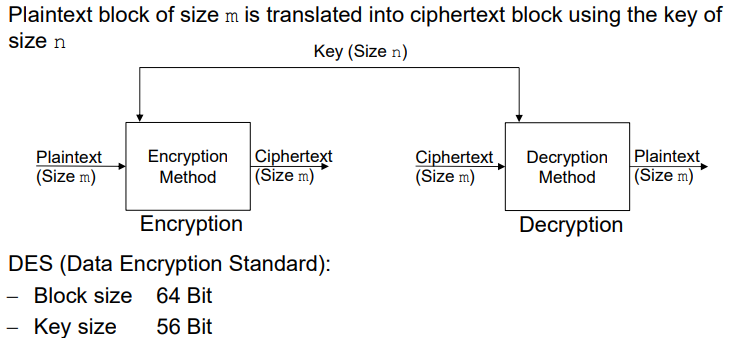
Cryptography and Cryptosystems, part II
2023년 2월 9일
4.[IT-Security] Chapter 4. Blockchain Technology
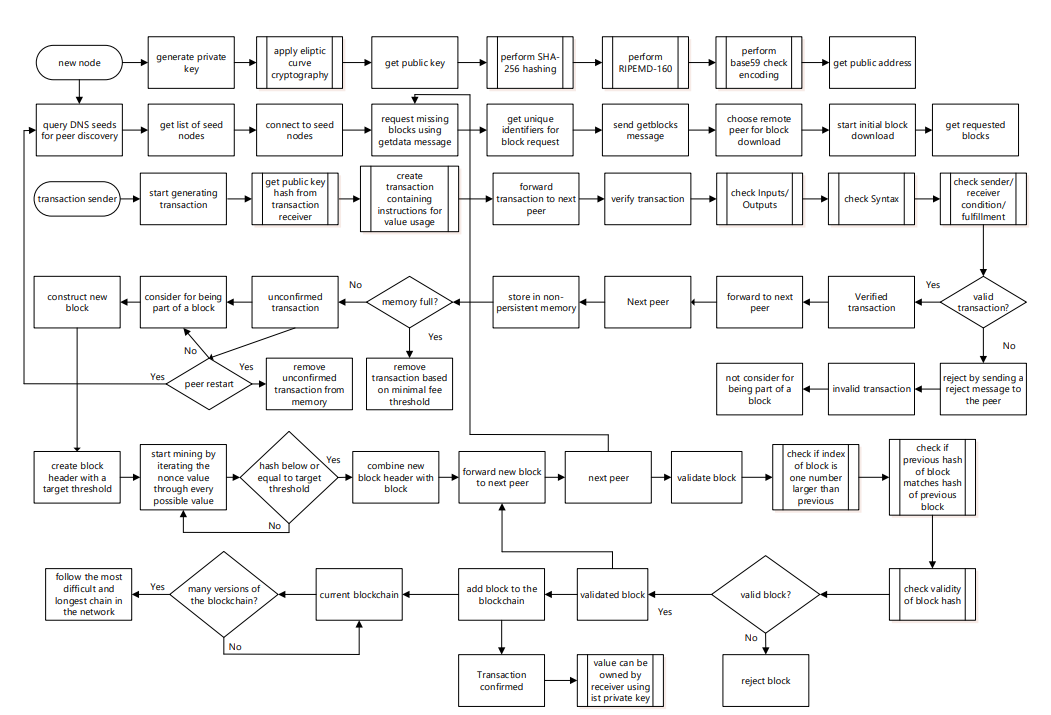
Blockchain Technology
2023년 2월 10일
5.[IT-Security] Chapter 5. Malicious Software

아휴 무셔어
2023년 2월 10일
6.[IT-Security] Chapter 6. Authentication
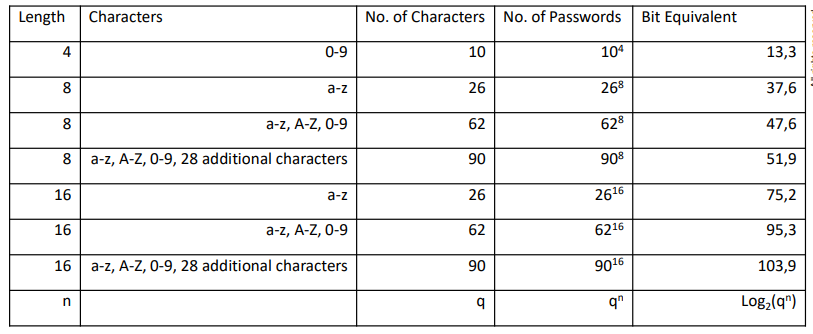
Authentication
2023년 2월 13일
7.[IT-Security] Chapter 7. Network Security
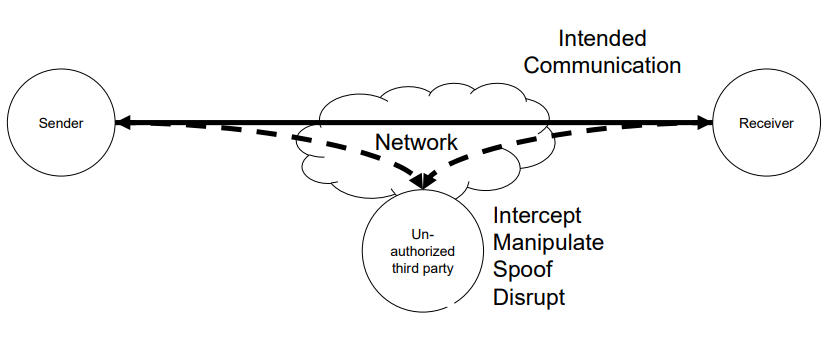
Network Security
2023년 2월 13일
8.[IT-Security] Chapter 8. Firewall
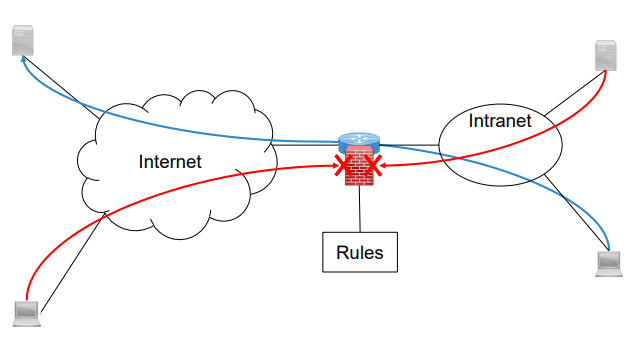
Firewall
2023년 2월 15일
9.[IT-Security] Chapter 9. Security Protocol
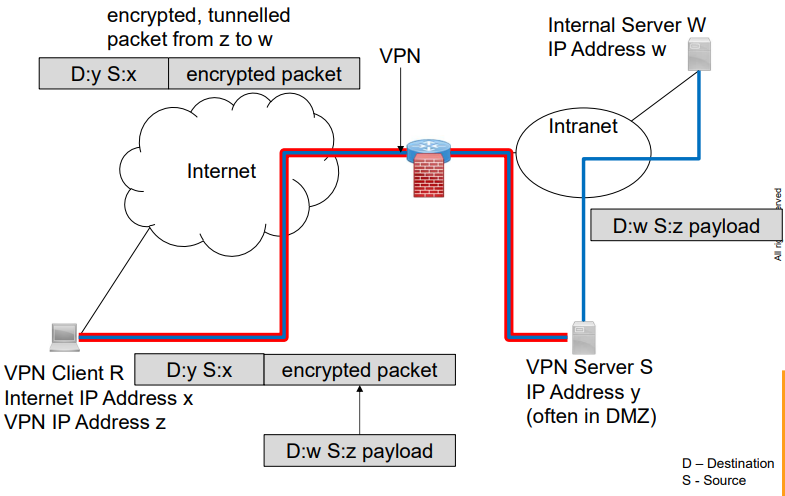
VPN, Site-to-Site VPN, IPSec
2023년 2월 17일