👩💻0630[IaC,terraform]
📌 AWS CloudFormation(Azure Resource Manager,GCP Deployment Manager)
📙 주요 섹션 설명
✔️ 1. Resources(생성) : AWS 인프라의 실질적인 섹션입니다. EC2 인스턴스, S3 버킷, ELB등과 같은 클라우드 포메이션을 이용해 AWS 웹 콘솔에서 실행하는 것으로 거의 모든 리소스 유형을 생성할 수 있습니다. 하지만 신규 또는 최첨단의 AWS 리소스는 즉시 제공되지 않는 경우가 종종 있습니다. 리소스에는 기본 반환값이 있습니다. Ref를 이용해 이 반환값을 얻어올 수 있고 템플릿의 다른 위치에 사용할 수 있습니다. 예를 들어 AWS::EC2::VPC 리소스 유형은 기본 반환값을 갖고 있고 이 값은 VPC의 ID 입니다.
✔️ 2. Parameters(입력) : 명령줄 도구에 입력하는 매개변수와 동일하게 스택을 만들거나 업데이트할 때 정의하는 입력값입니다. 파라미터는 템플릿의 변경 없이도 스택을 커스터마이즈할 수 있게 해줍니다. AMI ID, VPC ID, Subnet ID등과 같은 매개변수를 사용할 수 있습니다.
✔️ 3. Output(출력) : 스택이 완료된 후에 결과물을 출력하려고 할때 유용합니다. 예를 들어 ELB의 퍼블릭 URL이나 EC2의 퍼블릭 IP를 출력할 수 있습니다.
✔️ 4. Mapping(지정) : 리전의 특화된 템플릿에서 어떠한 요소를 참조할 때 필요합니다. 예를 들어 템플릿에 EC2 AMI ID에 대한 매핑을 지정하는 것입니다. AMI ID가 리전에 특화된 리소스이기 때문에 유효한 AMI ID를 리전별로 지정하려고 할때 사용합니다.
📙 Resources 파일 생성(VPC)
# vi new-vpc.yaml
AWSTemplateFormatVersion: 2010-09-09
Resources:
VPC: ## 논리적 이름. 내가 정하기 나름.
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: NEW-VPC
SubnetA:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2A
SubnetB:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2b
VpcId: !Ref VPC
CidrBlock: 192.168.16.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2B
SubnetC:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2c
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2C
SubnetD:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2d
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2D
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: NEW-IGW
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
RouteTableA:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: NEW-PUBLIC-RTB
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref RouteTableA
SubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetA
SubnetBRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetB
SubnetCRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetC
SubnetDRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetD
✔️EnableDnsSupport;
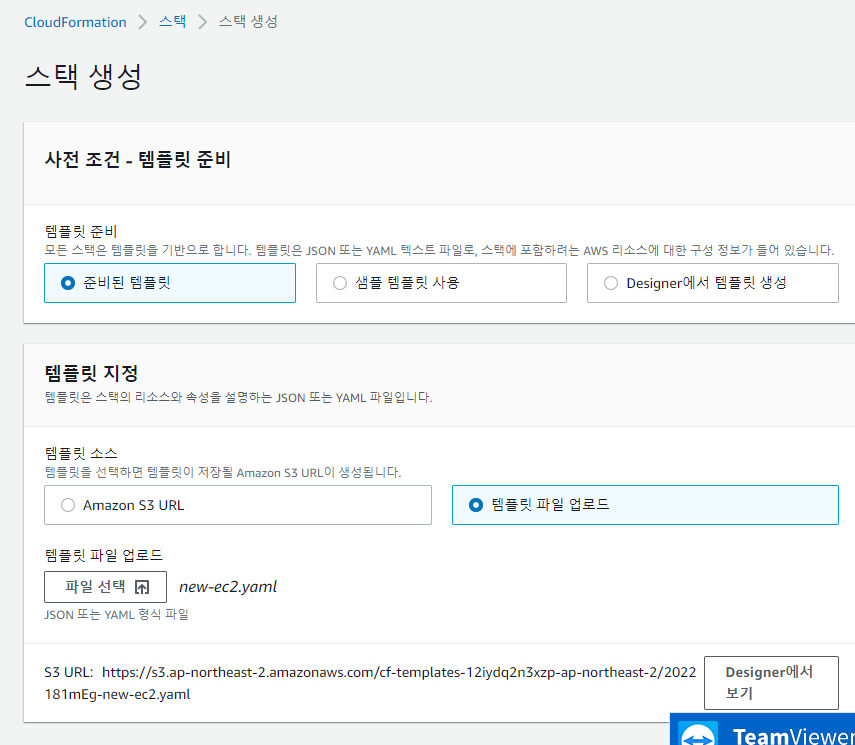
📙 AWS - 웹 / cloudformation에서 스택 생성
✔️ 리전 - 서울에서 진행
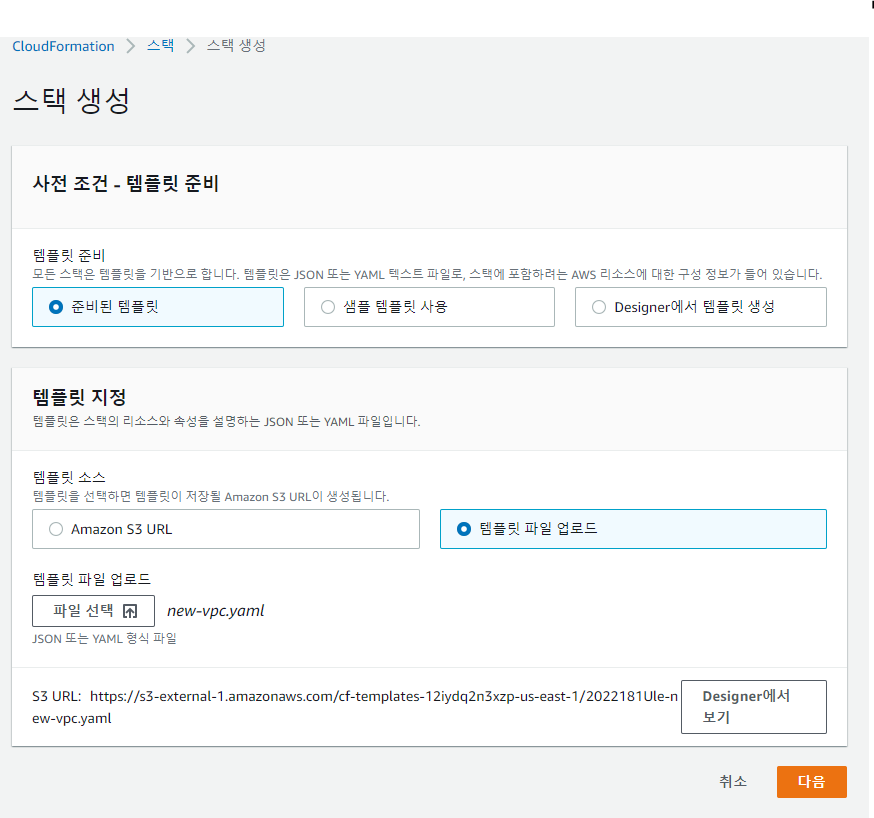
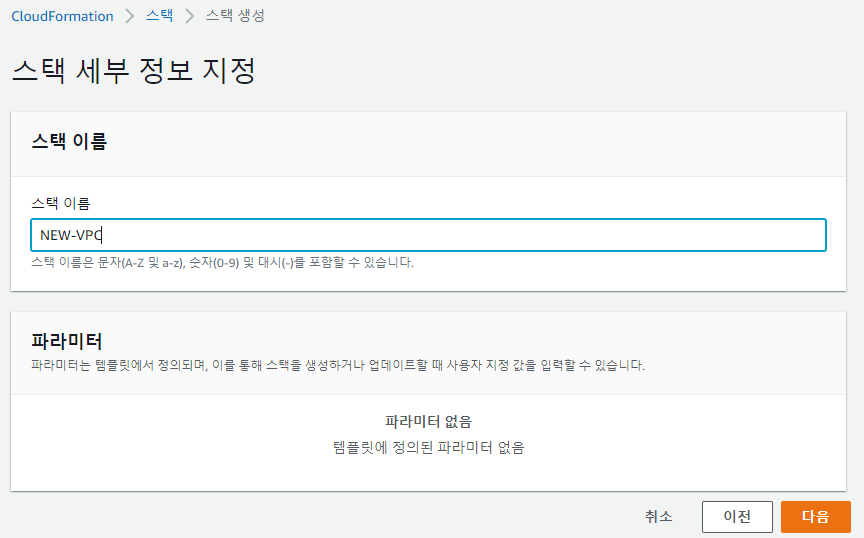
✔️ 스택옵션구성 생략 - 스택 생성 버튼 클릭
📙 parameter, mapping, resours ( 인스턴스 생성 )
VPC ID, 서브넷 ID 위에서 생성된 것으로 입력해주기
# vi new-ec2.yaml
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-2:
AMIID: ami-0fd0765afb77bcca7
ap-northeast-1:
AMIID: ami-0b7546e839d7ace12
Parameters:
InstanceTypeParameter:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
VPC:
Type: String
Default: vpc-01a276b266db7833b
Description: VPC ID.
Subnet:
Type: String
Default: subnet-01132b9dddcf71d3d
Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: new-key
Description: The key used to access the instance.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "NEW-SG-WEB"
GroupDescription: "SSH and web traffic in, all traffic out."
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 123.142.252.25/32
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
Linux:
Type: 'AWS::EC2::Instance'
Properties:
SubnetId: !Ref Subnet
# ImageId: !Ref AMI
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceTypeParameter
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: NEW-EC2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello World!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
Value: {"Fn::GetAtt": ["Linux","PublicIp"]}✔️ 리전 - 서울에서 진행
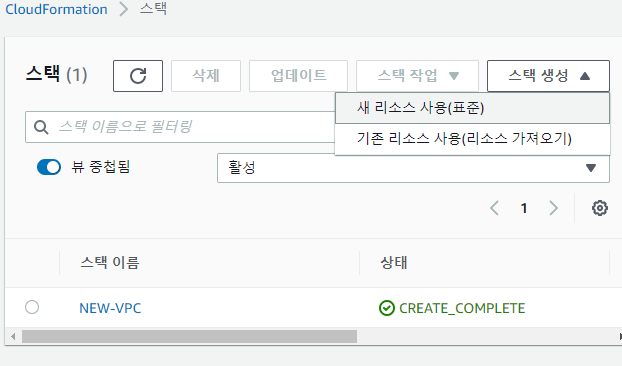
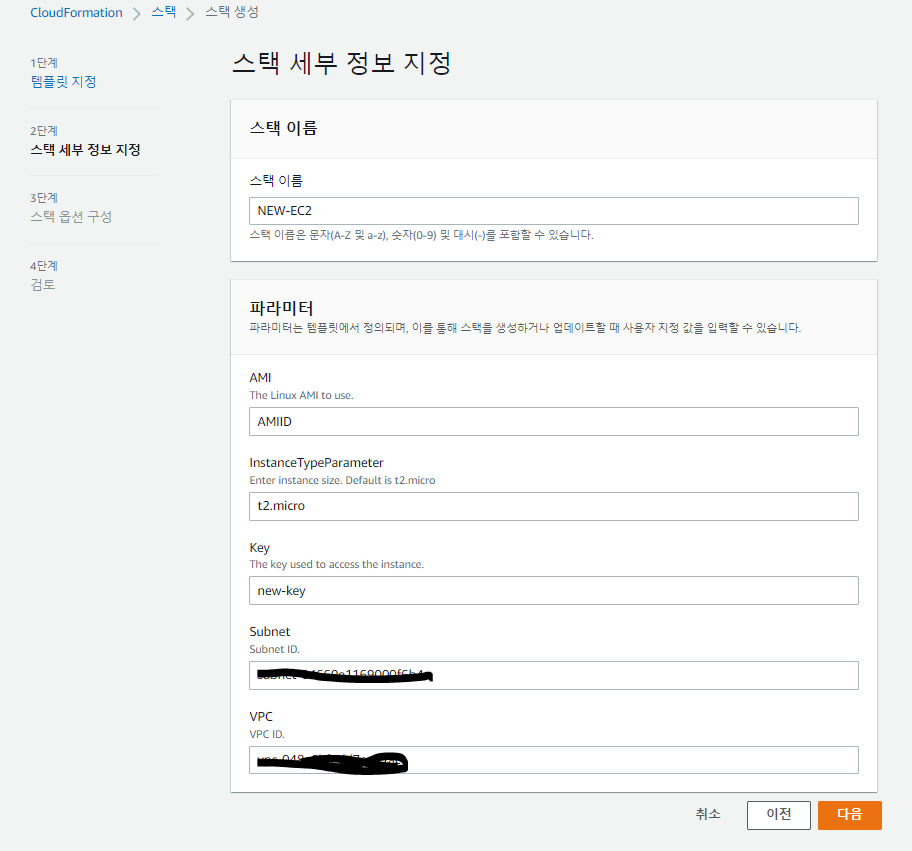
✔️ 스택옵션구성 생략 - 스택 생성 버튼 클릭
📙정리 (삭제하기)
✔️ 삭제 순서 ; ec2 - vpc
✔️ 스택을 삭제하면 내부 리소스들도 한꺼번에 삭제 됨.
✔️ s3버킷은 따로 삭제해주어야 함.
📌 실무 특화 이론
실무 특화 pdf 파일 7.p~ 확인
✔️오케스트레이션도구
쿠버네티스는 곧 클러스터,
AZURE AKS, EKS, GCP GKE => 쿠버네티스
구성관리 ; ansible(on-prem)
서버 템플릿 ; 도커
오케스트레이션 ; 쿠버네티스
프로비전 ; 테라폼
->엔서블과 테라폼은 퍼블릭 클라우드 시대에 접어들면서 그 차이가 점점 줄어듦. 하지만 테라폼이 ec2생성하기가 더 쉬움.
📌 Terraform
📙 Terraform 작동 방식
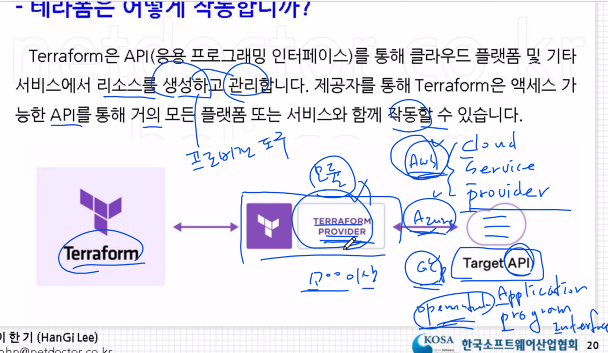
테라폼은 해시코프사에서 Go언어로 개발한 오픈소스도구입니다. 운영체제마다 바이너리 파일이 존재하는데 Go 코드는 하나의 바이너리 파일로 컴파일되며 Terraform이라는 명령어로 실행할 수 있습니다. 이 Terraform 명령어를 사용하여 노트북, 데스크탑, 빌드 서버 또는 다른 컴퓨터에서든 인프라를 배포할 수 있으며 이를 위해 추가 인프라(마스터, 에이전트)를 생성할 필요가 없습니다. 즉 Terraform 명령어가 AWS, Azure, GCP, Openstack 등의 Provider를 대신해 API를 호출하여 리소스를 생성합니다.
테라폼은 생성하려는 인프라 정보가 담겨 있는 텍스트로 이루어진 테라폼 구성 파일을 생성하여 API를 호출합니다. 이러한 구성 값들이 '코드형 인프라'를 만드는 바로 그 '코드'입니다. 팀의 누군가가 인프라를 수정하고자 할 때, 서버에 직접 접속하여 작업하거나 수작업으로 수정하는 대신 테라폼을 사용하여 구성 파일을 수정할 수 있습니다.
# vi main.tf
provider "aws" { # aws를 공급자로 사용하여
region = "ap-northeast-2" # 서울 리전에 인프라를 배포한다는 의미
}
resource "aws_instance" "example" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
}
resource "_" "" { # PROVIDER는 aws 같은 공급자의 이름이고 TYPE은 instance 같이 해당 공급자에서 생성할 리소스 유형입니다. NAME은 테라폼 코드에서 이 리소스를 참조하기 위해 사용할 수 있는 example과 같은 '식별자'입니다. CONFIG는 특정 리소스에 대한 하나 이상의 인수(argument)로 구성됩니다.
[CONFIG ...]
}
📙 Terraform 주요 명령어
✔️ *.tf 스크립트 작성
✔️ terraform init : terraform 명령어에는 테라폼의 기본 기능이 포함되어 있지만 모든 공급자(AWS, Azure, GCP 등)에 대한 코드가 포함되어 있지 않습니다. 그렇게 때문에 terraform init 명령어를 실행하여 테라폼에 코드를 스캔하도록 지시하고 어느 공급자인지 확인하고, 필요한 코드를 다운로드하도록 해야 합니다. 기본적으로 공급자 코드는 테라폼의 .terraform 폴더에 다운로드됩니다.
✔️ terraform plan : 테라폼이 구성 파일을 사용하여 작업을 수행하기 전에 코드의 온전성을 검사할 수 있습니다. plan 명령어는 리눅스에서 쓰이는 diff 명령의 결괏값과 유사합니다. + 가 있는 항목은 추가되고, - 가 있는 항목은 삭제된다는 뜻입니다. ~ 가 있는 항목은 수정됩니다.
✔️ terraform apply : 테라폼의 구성 파일을 실행하려면 terraform apply 명령어를 실행합니다.
📙 Terraform 설치
# wget https://releases.hashicorp.com/terraform/1.2.3/terraform_1.2.3_linux_amd64.zip
# unzip terraform_1.2.3_linux_amd64.zip
# mv terraform /usr/local/bin/
# terraform -version📙 AWS Terraform ec2 인스턴스 생성
# mkdir aws && cd $_
# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_instance" "example" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
}
# terraform init
# terraform plan
# terraform apply📙 ec2 인스턴스 정보 추가 및 삭제 (destroy)
# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_instance" "example" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
tags = {
Name = "terraform-example"
}
}
# terraform init
# terraform plan
# terraform apply
# terraform destroy📙 ec2 인스턴스 웹서버 배포
# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_instance" "example" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
vpc_security_group_ids = [aws_security_group.instance.id]
key_name = "new-key"
user_data = <<-EOF
#! /bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello, Terraform" > /var/www/html/index.html
EOF
tags = {
Name = "terraform-example"
}
}
resource "aws_security_group" "instance" {
name = var.security_group_name
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["123.142.252.25/32"]
}
ingress {
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "terraform-sg"
}
}
variable "security_group_name" {
description = "The name of the security group"
type = string
default = "terraform-example-instance"
}
output "public_ip" {
value = aws_instance.example.public_ip
description = "The public IP of the Instance"
}
output "public_dns" {
value = aws_instance.example.public_dns
description = "The Public dns of the Instance"
}
output "private_ip" {
value = aws_instance.example.private_ip
description = "The Private_ip of the Instance"
}
# terraform init
# terraform plan
# terraform apply
# terraform output public_ip
# terraform destroy📙✔️✏️📢⭐️📌
