👩💻0701[IaC,terraform]
📌Cloudformation
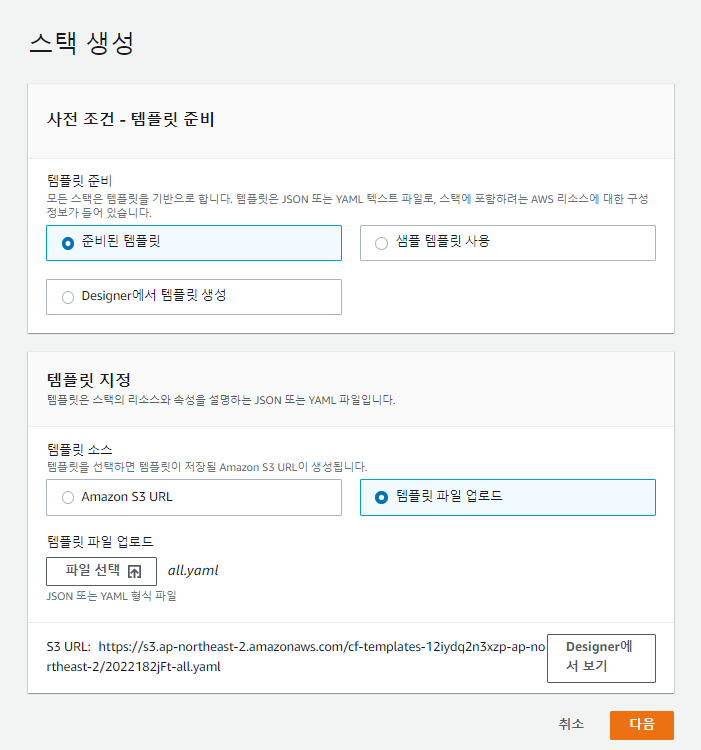
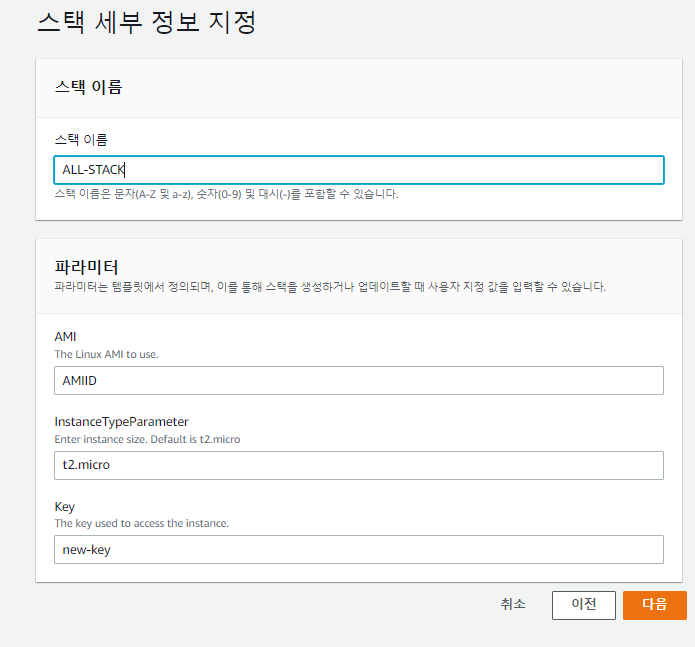
✔️ all.yaml 생성
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-2:
AMIID: ami-0fd0765afb77bcca7
ap-northeast-1:
AMIID: ami-0b7546e839d7ace12
Parameters:
InstanceType:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
# VPC:
# Type: String
# Default: vpc-01a276b266db7833b
# Description: VPC ID.
# Subnet:
# Type: String
# Default: subnet-01132b9dddcf71d3d
# Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: new-key
Description: The key used to access the instance.
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: NEW-VPC
SubnetA:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2A
SubnetB:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2b
VpcId: !Ref VPC
CidrBlock: 192.168.16.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2B
SubnetC:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2c
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2C
SubnetD:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2d
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: NEW-PUBLIC-SUBNET-2D
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: NEW-IGW
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
RouteTableA:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: NEW-PUBLIC-RTB
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref RouteTableA
SubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetA
SubnetBRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetB
SubnetCRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetC
SubnetDRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref RouteTableA
SubnetId: !Ref SubnetD
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "NEW-SG-WEB"
GroupDescription: "NEW-SG-WEB"
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 123.142.252.25/32
- IpProtocol: icmp
FromPort: '-1'
ToPort: '-1'
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
EC2Insteance:
Type: AWS::EC2::Instance
Properties:
SubnetId: !Ref SubnetA
# ImageId: !Ref AMI
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceType
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: NEW-EC2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello World!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
Value: {"Fn::GetAtt": ["EC2Insteance","PublicIp"]}
📌 Terraform
📙 VPC 만들기
[root@localhost ~]# cd aws
[root@localhost aws]# ls
main.tf terraform.tfstate terraform.tfstate.backup
[root@localhost aws]# rm -rf *
[root@localhost aws]# ls# vi new-vpc.tf
provider "aws" {
region = "ap-northeast-2"
}
data "aws_availability_zones" "available" {
state = "available"
}
resource "aws_vpc" "new_vpc" {
cidr_block = "192.168.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
instance_tenancy = "default"
tags = {
Name = "NEW-VPC"
}
}
resource "aws_subnet" "new_public_subnet_2a" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.0.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "NEW-PUBLIC-SUBNET-2A"
}
}
resource "aws_subnet" "new_public_subnet_2b" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.16.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "NEW-PUBLIC-SUBNET-2B"
}
}
resource "aws_subnet" "new_public_subnet_2c" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.32.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "NEW-PUBLIC-SUBNET-2C"
}
}
resource "aws_subnet" "new_public_subnet_2d" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.48.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "NEW-PUBLIC-SUBNET-2D"
}
}
resource "aws_internet_gateway" "new_igw" {
vpc_id = aws_vpc.new_vpc.id
tags = {
Name = "NEW-IGW"
}
}
resource "aws_route_table" "new_public_rtb" {
vpc_id = aws_vpc.new_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.new_igw.id
}
tags = {
Name = "NEW-PUBLIC-RTB"
}
}
resource "aws_route_table_association" "new_public_subnet_2a_association" {
subnet_id = aws_subnet.new_public_subnet_2a.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2b_association" {
subnet_id = aws_subnet.new_public_subnet_2b.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2c_association" {
subnet_id = aws_subnet.new_public_subnet_2c.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2d_association" {
subnet_id = aws_subnet.new_public_subnet_2d.id
route_table_id = aws_route_table.new_public_rtb.id
}[root@localhost aws]# vi new-vpc.tf
[root@localhost aws]# terraform init
[root@localhost aws]# terraform plan
[root@localhost aws]# terraform apply
📙 인스턴스 만들기
# vi new-ec2.tf
data "aws_vpc" "new_vpc" {
tags = {
Name = "NEW-VPC"
}
}
data "aws_subnet" "apne2_az1" {
tags = {
Name = "NEW-PUBLIC-SUBNET-2A"
}
}
resource "aws_instance" "example" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
subnet_id = aws_subnet.new_public_subnet_2a.id
vpc_security_group_ids = [aws_security_group.instance.id]
key_name = "new-key"
user_data = <<-EOF
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello, Terraform" > /var/www/html/index.html
EOF
tags = {
Name = "terraform-example"
}
}
resource "aws_security_group" "instance" {
vpc_id = data.aws_vpc.new_vpc.id
name = var.security_group_name
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["123.142.252.25/32"]
}
ingress {
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "terraform-sg"
}
}
variable "security_group_name" {
description = "The name of the security group"
type = string
default = "terraform-example-instance"
}
output "public_ip" {
value = aws_instance.example.public_ip
description = "The public IP of the Instance"
}
output "public_dns" {
value = aws_instance.example.public_dns
description = "The Public dns of the Instance"
}
output "private_ip" {
value = aws_instance.example.private_ip
description = "The Private_ip of the Instance"
}
[root@localhost aws]# terraform init
[root@localhost aws]# terraform plan
[root@localhost aws]# terraform apply
[root@localhost aws]# terraform destroy
📙 VPC만들기 + 로드밸런서 생성
# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
data "aws_availability_zones" "available" {
state = "available"
}
resource "aws_vpc" "new_vpc" {
cidr_block = "192.168.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
instance_tenancy = "default"
tags = {
Name = "NEW-VPC"
}
}
resource "aws_subnet" "new_public_subnet_2a" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.0.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "NEW-PUBLIC-SUBNET-2A"
}
}
resource "aws_subnet" "new_public_subnet_2b" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.16.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "NEW-PUBLIC-SUBNET-2B"
}
}
resource "aws_subnet" "new_public_subnet_2c" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.32.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "NEW-PUBLIC-SUBNET-2C"
}
}
resource "aws_subnet" "new_public_subnet_2d" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.48.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "NEW-PUBLIC-SUBNET-2D"
}
}
resource "aws_internet_gateway" "new_igw" {
vpc_id = aws_vpc.new_vpc.id
tags = {
Name = "NEW-IGW"
}
}
resource "aws_route_table" "new_public_rtb" {
vpc_id = aws_vpc.new_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.new_igw.id
}
tags = {
Name = "NEW-PUBLIC-RTB"
}
}
resource "aws_route_table_association" "new_public_subnet_2a_association" {
subnet_id = aws_subnet.new_public_subnet_2a.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2b_association" {
subnet_id = aws_subnet.new_public_subnet_2b.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2c_association" {
subnet_id = aws_subnet.new_public_subnet_2c.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2d_association" {
subnet_id = aws_subnet.new_public_subnet_2d.id
route_table_id = aws_route_table.new_public_rtb.id
}
variable "security_group_name" {
description = "The name of the security group"
type = string
default = "NEW-SG-ALB"
}
resource "aws_security_group" "new_sg_alb" {
name = var.security_group_name
vpc_id = aws_vpc.new_vpc.id
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "NEW-SG-ALB"
}
}
resource "aws_lb" "frontend" {
name = "alb-example"
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.new_sg_alb.id]
subnets = [
aws_subnet.new_public_subnet_2a.id,
aws_subnet.new_public_subnet_2c.id
]
tags = {
Name = "NEW-ALB"
}
lifecycle { create_before_destroy = true }
}
resource "aws_instance" "alb_vm_01" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
subnet_id = aws_subnet.new_public_subnet_2a.id
vpc_security_group_ids = [aws_security_group.new_sg_alb.id]
key_name = "new-key"
user_data = <<-EOF
#! /bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello, Terraform01" > /var/www/html/index.html
EOF
tags = {
Name = "ALB01"
}
}
resource "aws_instance" "alb_vm_02" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
subnet_id = aws_subnet.new_public_subnet_2c.id
vpc_security_group_ids = [aws_security_group.new_sg_alb.id]
key_name = "new-key"
user_data = <<-EOF
#! /bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello, Terraform02" > /var/www/html/index.html
EOF
tags = {
Name = "ALB02"
}
}
resource "aws_lb_target_group" "tg" {
name = "TargetGroup"
port = 80
target_type = "instance"
protocol = "HTTP"
vpc_id = aws_vpc.new_vpc.id
health_check {
path = "/"
protocol = "HTTP"
matcher = "200"
interval = 15
timeout = 3
healthy_threshold = 2
unhealthy_threshold = 2
}
}
resource "aws_alb_target_group_attachment" "tgattachment01" {
target_group_arn = aws_lb_target_group.tg.arn
target_id = aws_instance.alb_vm_01.id
port = 80
}
resource "aws_alb_target_group_attachment" "tgattachment02" {
target_group_arn = aws_lb_target_group.tg.arn
target_id = aws_instance.alb_vm_02.id
port = 80
}
resource "aws_lb_listener" "front_end" {
load_balancer_arn = aws_lb.frontend.arn
port = "80"
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.tg.arn
}
}
output "lb_dns_name" {
description = "The DNS name of the load balancer."
value = aws_lb.frontend.dns_name
}
📙 변수 활용
[root@localhost aws]# cd ~
[root@localhost ~]# mkdir test && cd $_
# vi variables.tf
variable "security_group_name" {
description = "The name of the security group"
type = string
default = "terraform-example-instance"
}
variable "http_port" {
description = "The port the server will use for HTTP requests"
type = number
default = 80
}
variable "ssh_port" {
description = "The port the server will use for SSH requests"
type = number
default = 22
}
# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_instance" "example" {
ami = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
vpc_security_group_ids = [aws_security_group.instance.id]
key_name = "aws-key"
user_data = <<-EOF
#! /bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello, Terraform" > /var/www/html/index.html
EOF
tags = {
Name = "terraform-example"
}
}
resource "aws_security_group" "instance" {
name = var.security_group_name
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = var.ssh_port
to_port = var.ssh_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "terraform-sg"
}
}
# vi outputs.tf
output "public_ip" {
value = aws_instance.example.public_ip
description = "The public IP of the Instance"
}
output "public_dns" {
value = aws_instance.example.public_dns
description = "The Public dns of the Instance"
}
output "private_ip" {
value = aws_instance.example.private_ip
description = "The Private_ip of the Instance"
}
# terraform init
# terraform validate
# terraform plan
# terraform apply
# terraform output public_ip
# terraform destroy
📙✔️✏️📢⭐️📌
📌 기타
⭐️ 명령어
✔️ !Ref ; Reference : 참조
✔️ DependsOn : 해당 작업이 끝난 후에 진행하라.
⭐️ terraform healthcheck path

healthcheck폴더 지정 가능. 폴더 안에 index.html있어야함.
⭐️ arn
amazon resource number
⭐️ 보안그룹 ID가져올 때 대괄호'[]' 해주기
vpc_security_group_ids = [aws_security_group.new_sg_alb.id]
⭐️ create_before_destroy
만들고 지워라.

⭐️ launch configuration
launch configuration ; 이미지
