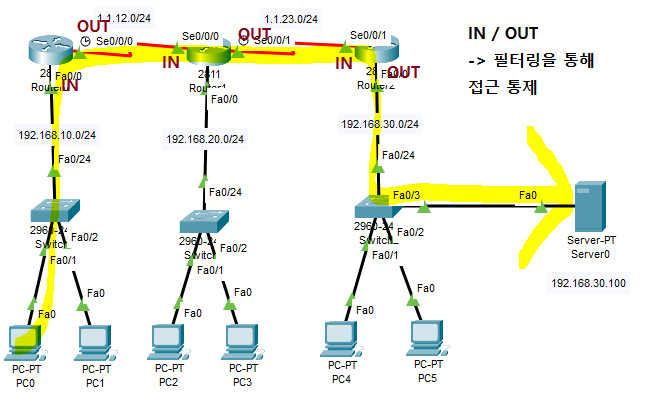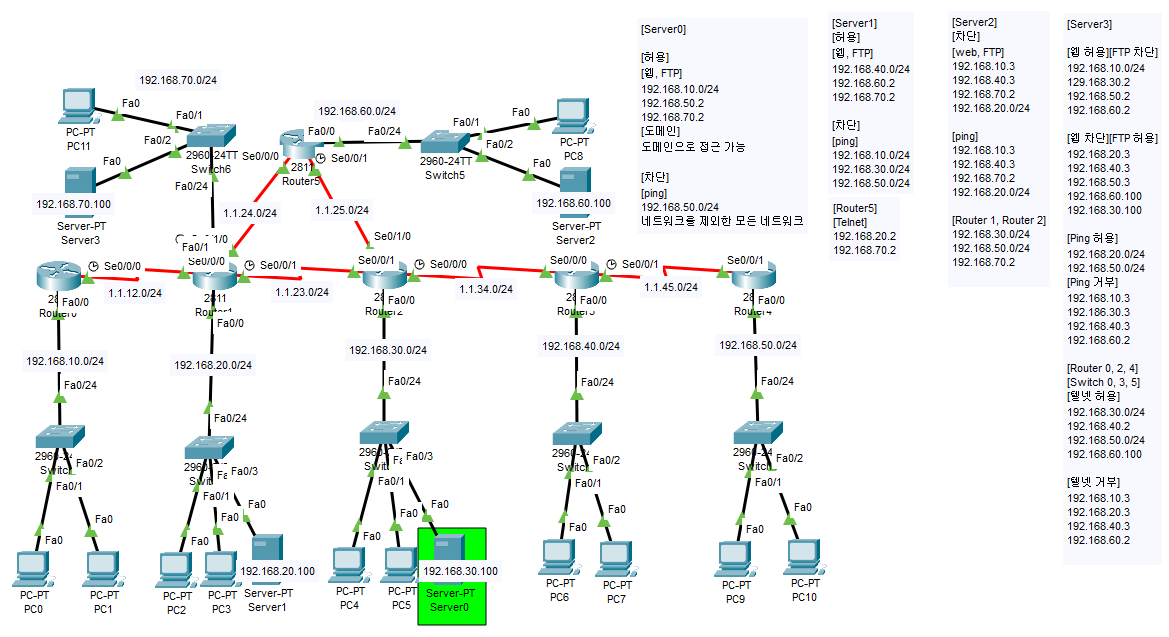
ACL
-
3/4계층 방화벽
-
라우터에 설정
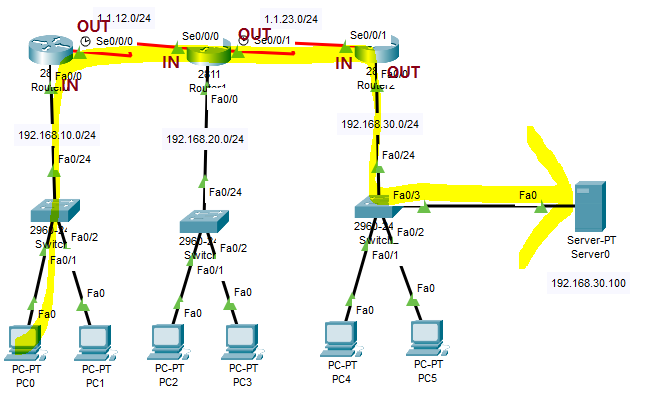
=> 라우터를 기준으로 패킷이 어떻게 흐르는지 봐야함 -
PAT와 IPsec에서 access-list 풀 생성
-
하나의 인터페이스에는 하나의 정책(IN, OUT)밖에 적용 못함
Standard ACL
- 오로지 출발지 네트워크만 참조 / ip만 참조 (목적지는 참조X)
- ACL 번호 1 ~ 99
- 라우터에 ACL이 적용됐다면?
a. 일반 패킷이 들어오면 IN 인터페이스 참조
b. 패킷과 ACL을 대조
c. ACL과 대조 후 이상 없으면 라우팅 테이블 참조
d. 위 과정이 이상이 없어도 다음 경로로 갈때는 OUT 인터페이스 참조
- ACL은 여태까지 PING만 때려서 돌아는것만 생각하는 것이 아닌 효율성을 따져야하는 정책
설정
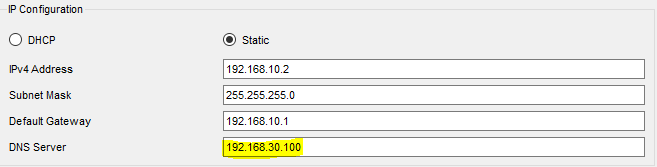
- 서버의 DNS 설정 추가.
- PC의 DNS 주소 추가
- 적용할 라우터에 명령어 추가
Router(config)#access-list 1 deny 192.168.10.0 0.0.0.255
Router(config)#access-list (ACL 번호) (허용/거부) (출발지 네트워크/호스트) (와일드마스크)
Router(config)#in fa0/0
Router(config-if)#ip access-group 1 out
cf)
ACL을 설정하면 자동으로 전체 차단이 된다.
여기서 Permit을 하면 그 외 전체 차단이 되니까 상관이 없지만
Deny를 하게 되면 Deny차단+전체 차단이 되어버리니
Router(config)#access-list 1 permit any=> any 명령어로 전체 차단을 풀어주어야함.
특정 호스트만 차단
<ACL 설정>
Router(config)#access-list 2 deny host 192.168.10.2
Router(config)#access-list 2 permit any
<정책 설정>
Router(config)#in fa0/0
Router(config-if)#ip access-group 2 out다수의 네트워크 차단
(10번대, 20번대 차단)
Router(config)#access-list 3 deny 192.168.10.0 0.0.0.255
Router(config)#access-list 3 deny 192.168.20.0 0.0.0.255
Router(config)#access-list 3 permit any
Router(config)#in fa0/0
Router(config-if)#ip access-group 3 out다수 네트워크 + 특정 호스트 차단
(10번대, 20번대 왼쪽 PC 차단)
Router(config)#access-list 4 deny 192.168.10.0 0.0.0.255
Router(config)#access-list 4 deny host 192.168.20.2
Router(config)#access-list 4 permit any
Router(config)#in fa0/0
Router(config-if)#ip access-group 4 outcf)
ACL 적용 시좁은 대역 -> 넓은 대역/C class -> B class순으로 설정하기
-> 순차적으로 대역을 읽기 때문에 명령어를 꼬아서 받아들일 수 있다.
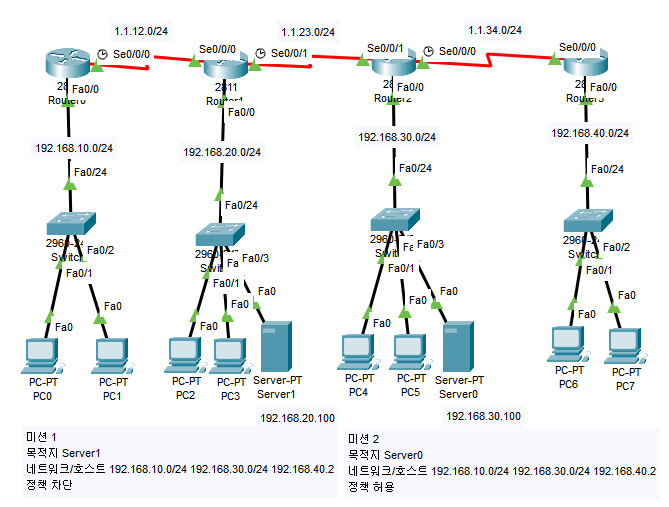
미션
Extended ACL
-
출발지/목적지 네트워크/호스트, 프로토콜 제어, 서비스(포트)를 참조 및 제어
-
ACL 번호 100 ~ 199
-
[적용할 라우터에 명령어 추가]
<ACL 설정>
Router(config)#access-list 100 deny ip 192.168.10.0 0.0.0.255 192.168.30.0 0.0.0.255
Router(config)#access-list 100 deny (프로토콜) (출발지 네트워크/호스트) (목적지 네트워크/호스트)
Router(config)#access-list 100 permit ip any any
Router(config)#access-list 100 permit (프로토콜) (출발지) (목적지)
<정책 설정>
Router(config)#in fa0/0
Router(config-if)#ip access-group 100 out[출발지에서의 IP 차단]
Router(config)#access-list 101 deny ip 192.168.10.0 0.0.0.255 host 192.168.30.100
Router(config)#access-list 101 permit ip any any
Router(config)#in fa0/0
Router(config-if)#ip access-group 101 out[출발지에서의 Ping 차단]
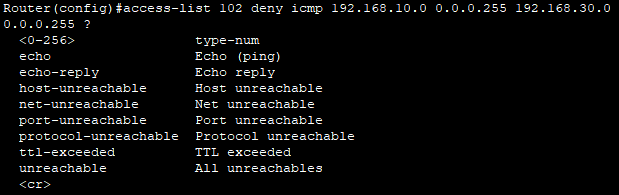
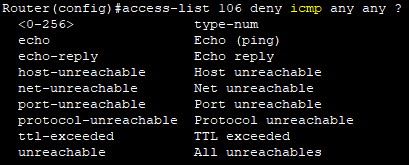
Router(config)#access-list 102 deny icmp 192.168.10.0 0.0.0.255 192.168.30.0 0.0.0.255 echo
Router(config)#access-list 102 permit ip any any
-> icmp의 echo(ping)은 차단 / ip는 허용
Router(config)#in fa0/0
Router(config-if)#ip access-group 102 out결과
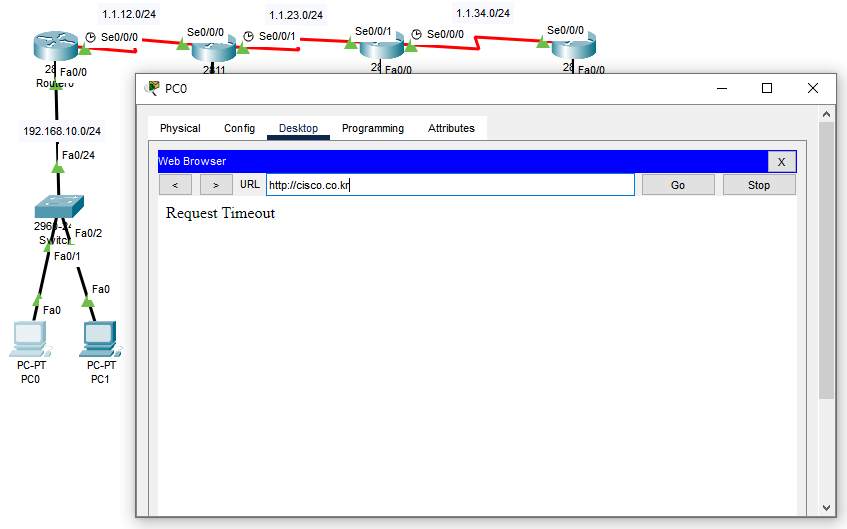
- 패킷트레이서의 ping기능은 작동하지 않지만 30번대 네트워크 서버까지 통신은 되는 모습)
- 해당 명령어 (echo = ping)
[출발지에서의 웹사이트 접속 차단]
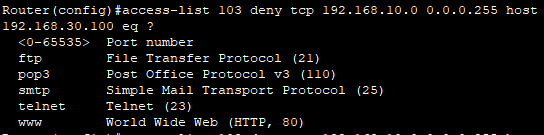
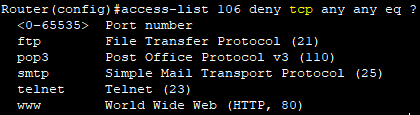
Router(config)#access-list 103 deny tcp 192.168.10.0 0.0.0.255 host 192.168.30.100 eq www
Router(config)#access-list 103 permit ip any any
Router(config)#in fa0/0
Router(config-if)#ip access-group 103 out결과
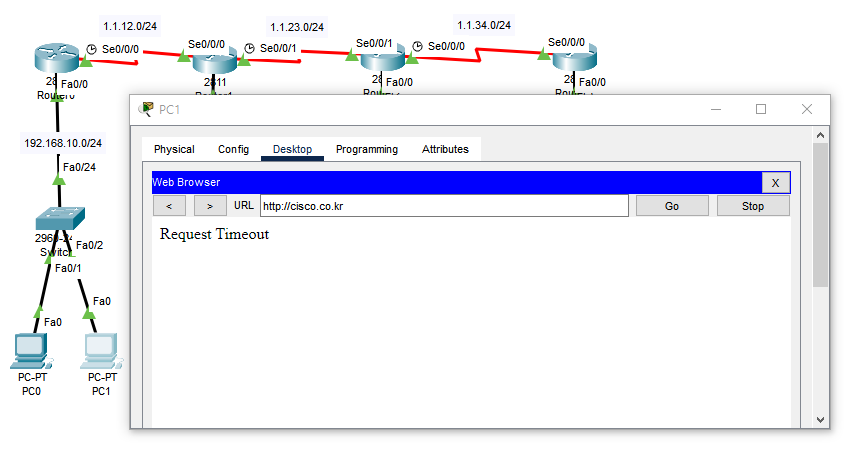
- Ping은 돌지만 30번대 네트워크 서버 웹사이트에는 접속을 못하는 상황
- tcp에서는 해당 포트를 지원한다.
[출발지에서의 Ping+웹사이트 접속 차단]
Router(config)#access-list 104 deny icmp 192.168.10.0 0.0.0.255 host 192.168.30.100 echo
Router(config)#access-list 104 deny tcp 192.168.10.0 0.0.0.255 host 192.168.30.100 eq www
Router(config)#access-list 104 permit ip any any
Router(config)#in fa0/0
Router(config-if)#ip access-group 104 out결과
- 패킷 트레이서의 Ping과 30번대 네트워크 서버로의 웹사이트 접속이 차단되어있다.
(가시적으로 확인하는 방법이 막혀서 그렇지 SSH나 Telnet같은 기능들은 사용 가능한 상태임)
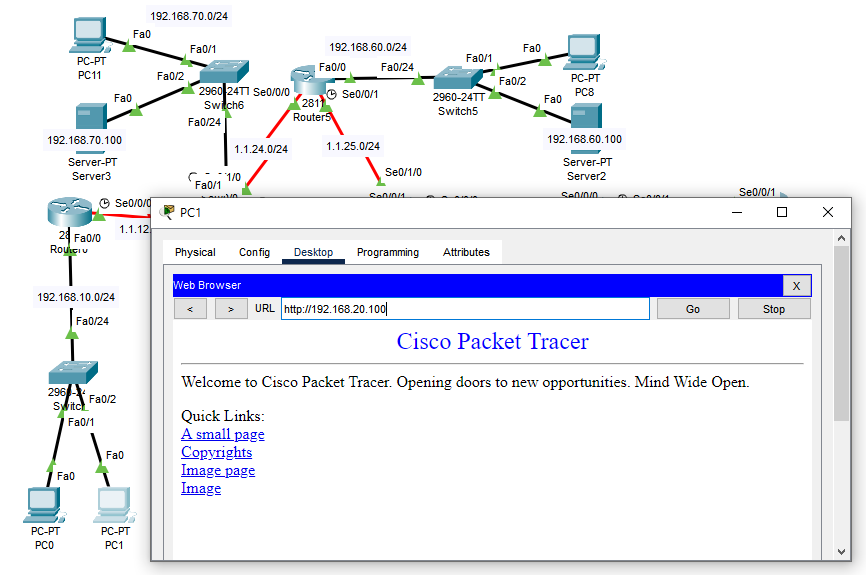
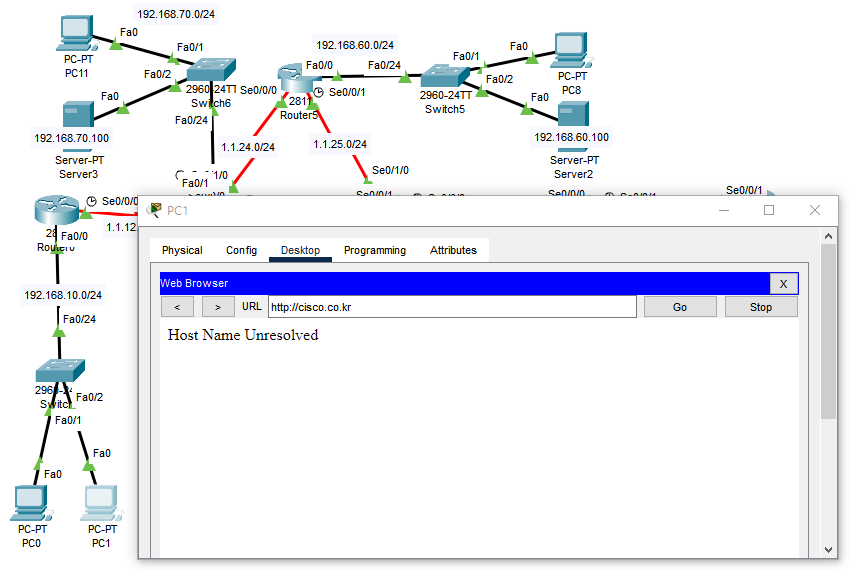
[출발지에서의 DNS차단]
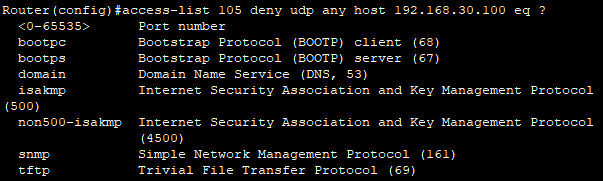
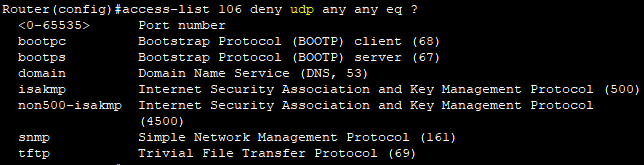
Router(config)#access-list 105 deny udp any host 192.168.30.100 eq domain
Router(config)#access-list 105 permit ip any any
Router(config)#in fa0/0
Router(config-if)#ip access-group 105 out결과
- DNS서버를 차단 하였다면 도메인으로 접속하는 건 불가능하고 도메인에 매칭된 주소로는 접근 가능하다.
- udp에서는 해당 포트를 지원한다.
Extended ACL 명령어 옵션
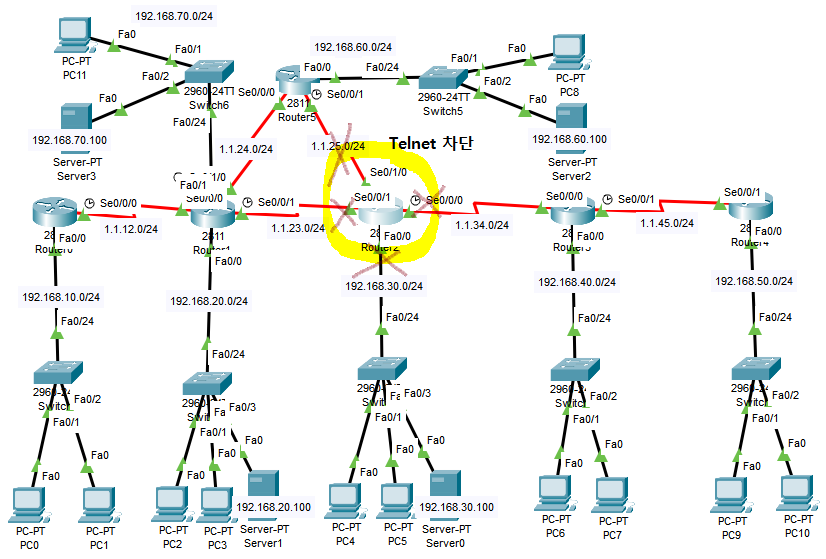
[출발지에서의 Telnet차단]
(수동 삽입)
Router(config)#access-list 109 deny tcp any host 192.168.30.1 eq telnet
Router(config)#access-list 109 deny tcp any host 1.1.23.2 eq telnet
Router(config)#access-list 109 deny tcp any host 1.1.34.1 eq telnet
Router(config)#access-list 109 deny tcp any host 1.1.25.2 eq telnet
Router(config)#access-list 109 permit ip any any
Router(config)#in se0/0/1
Router(config-if)#ip access-group 109 in
Router(config-if)#in se0/1/0
Router(config-if)#ip access-group 109 in
Router(config-if)#in se0/0/0
Router(config-if)#ip access-group 109 in
Router(config-if)#in fa0/0
Router(config-if)#ip access-group 109 in(간단하게 line 모드에 access-class 명령어 적용)
Router(config)#access-list 7 deny any
Router(config)#line vty 0 4
Router(config-line)#access-class 7 in결과
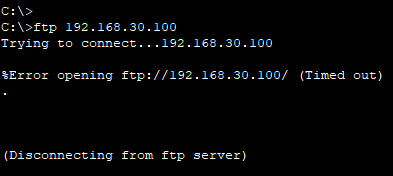
[출발지에서의 FTP차단]
Router(config)#access-list 110 deny tcp any host 192.168.30.100 eq f
Router(config)#access-list 110 permit ip any any
Router(config)#in fa0/0
Router(config-if)#ip access-group 110 out결과
- FTP 연결은 막히지만 그 외의 기능(ping, telnet, 웹사이트)들은 접속 가능하다.
[출발지에서의 TFTP차단]
Router(config)#access-list 111 permit udp 192.168.10.0 0.0.0.255 host 192.168.30.100 eq tftp
Router(config)#in fa0/0
Router(config-if)#no ip access-group 111 outcf)
FTP 종류
- FTP(ID/Password)
- Anonymous FTP(ID/Password)
- TFTP(무인증)
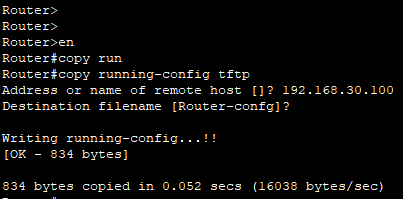
TFTP
- 포트번호 69번
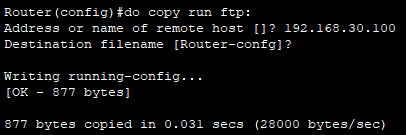
- 라우터에서 TFTP 서버로 running config 파일을 전송할 수 있다.
(하지만 TFTP는 인증 기능이 없어서 IP주소만 알면 보내거나 받을 수 있다.)
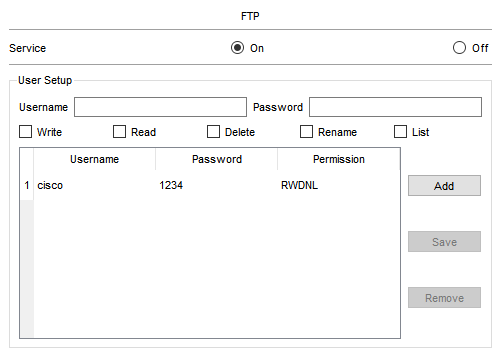
FTP
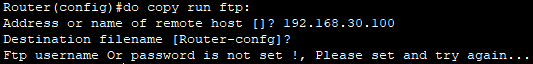
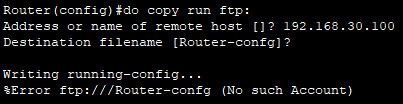
- FTP는 TFTP와 다르게 인증기능이 있다.
- FTP 유저네임과 패스워드를 생성하지않거나 FTP서버에서 유저네임 셋업을 하지않고
FTP로 파일을 전송시도 하면 해당 에러가 뜬다.
- FTP유저네임 생성 + FTP서버에 유저 셋업을 하고나면 정상적으로 FTP 서버로 running config 파일을 보낼 수 있다.
Router(config)#ip ftp username cisco Router(config)#ip ftp password 1234
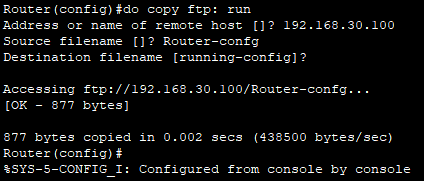
- 또한 FTP 서버로 보낸 config 파일을 다시 불러와 running config에 적용시킬수도 있다.
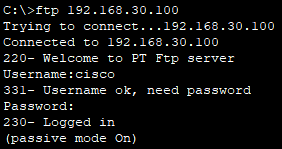
- 마지막으로 단말기 cmd창에서 FTP 서버로 접속 가능하다
미션
(Router 2-Server 0)
access-list 101 permit tcp host 192.168.50.2 host 192.168.30.100 eq www
access-list 101 permit tcp host 192.168.70.2 host 192.168.30.100 eq www
access-list 101 permit tcp 192.168.10.0 0.0.0.255 host 192.168.30.100 eq www
access-list 101 deny tcp any host 192.168.30.100 eq www
access-list 101 permit tcp host 192.168.50.2 host 192.168.30.100 eq ftp
access-list 101 permit tcp host 192.168.70.2 host 192.168.30.100 eq ftp
access-list 101 permit tcp 192.168.10.0 0.0.0.255 host 192.168.30.100 eq ftp
access-list 101 deny tcp any host 192.168.30.100 eq ftp
access-list 101 permit udp host 192.168.50.2 host 192.168.30.100 eq domain
access-list 101 permit udp host 192.168.70.2 host 192.168.30.100 eq domain
access-list 101 permit udp 192.168.10.0 0.0.0.255 host 192.168.30.100 eq domain
access-list 101 deny udp any host 192.168.30.100 eq domain
access-list 101 permit icmp 192.168.50.0 0.0.0.255 host 192.168.30.100 echo
access-list 101 deny icmp any host 192.168.30.100 echo
access-list 101 permit ip any any
in fa0/0
ip acc 101 out(Router 1-Server 1)
access-list 102 permit tcp host 192.168.60.2 host 192.168.20.100 eq www
access-list 102 permit tcp host 192.168.70.2 host 192.168.20.100 eq www
access-list 102 permit tcp 192.168.40.0 0.0.0.255 host 192.168.20.100 eq www
access-list 102 deny tcp any host 192.168.20.100 eq www
access-list 102 permit tcp host 192.168.60.2 host 192.168.20.100 eq ftp
access-list 102 permit tcp host 192.168.70.2 host 192.168.20.100 eq ftp
access-list 102 permit tcp 192.168.40.0 0.0.0.255 host 192.168.20.100 eq ftp
access-list 102 deny tcp any host 192.168.20.100 eq ftp
access-list 102 deny icmp 192.168.10.0 0.0.0.255 host 192.168.20.100 echo
access-list 102 deny icmp 192.168.30.0 0.0.0.255 host 192.168.20.100 echo
access-list 102 deny icmp 192.168.50.0 0.0.0.255 host 192.168.20.100 echo
access-list 102 permit icmp any host 192.168.20.100 echo
access-list 102 permit ip any any
in fa0/0
ip acc 102 out(Router 5-Telnet)
acc 1 per host 192.168.70.2
acc 1 per host 192.168.20.2
line vty 0 4
acce 1 in(Router 5-Server 2)
access-list 101 deny tcp host 192.168.10.3 host 192.168.60.100 eq www
access-list 101 deny tcp host 192.168.40.3 host 192.168.60.100 eq www
access-list 101 deny tcp host 192.168.70.2 host 192.168.60.100 eq www
access-list 101 deny tcp 192.168.20.0 0.0.0.255 host 192.168.60.100 eq www
access-list 101 permit tcp any host 192.168.60.100 eq www
access-list 101 deny tcp host 192.168.10.3 host 192.168.60.100 eq ftp
access-list 101 deny tcp host 192.168.40.3 host 192.168.60.100 eq ftp
access-list 101 deny tcp host 192.168.70.2 host 192.168.60.100 eq ftp
access-list 101 deny tcp 192.168.20.0 0.0.0.255 host 192.168.60.100 eq ftp
access-list 101 permit tcp any host 192.168.60.100 eq ftp
access-list 101 deny icmp host 192.168.10.3 host 192.168.60.100 echo
access-list 101 deny icmp host 192.168.40.3 host 192.168.60.100 echo
access-list 101 deny icmp host 192.168.70.2 host 192.168.60.100 echo
access-list 101 deny icmp 192.168.20.0 0.0.0.255 host 192.168.60.100 echo
access-list 101 permit icmp any host 192.168.60.100 echo
access-list 101 permit ip any any
in fa0/0
ip acc 101 out(Router 1, 2-Telnet)
access-list 1 deny 192.168.30.0 0.0.0.255
access-list 1 deny 192.168.50.0 0.0.0.255
access-list 1 deny host 192.168.70.2
access-list 1 permit any
line vty 0 4
pass 1234
login
access-class 1 in(Router 1-Server 3)
access-list 103 permit tcp host 192.168.30.2 host 192.168.70.100 eq www
access-list 103 permit tcp host 192.168.50.2 host 192.168.70.100 eq www
access-list 103 permit tcp host 192.168.60.2 host 192.168.70.100 eq www
access-list 103 permit tcp 192.168.10.0 0.0.0.255 host 192.168.70.100 eq www
access-list 103 deny tcp host 192.168.20.3 host 192.168.70.100 eq www
access-list 103 deny tcp host 192.168.40.3 host 192.168.70.100 eq www
access-list 103 deny tcp host 192.168.50.3 host 192.168.70.100 eq www
access-list 103 deny tcp host 192.168.30.100 host 192.168.70.100 eq www
access-list 103 deny tcp host 192.168.60.100 host 192.168.70.100 eq www
access-list 103 permit tcp any host 192.168.70.100 eq www
access-list 103 permit tcp host 192.168.20.3 host 192.168.70.100 eq ftp
access-list 103 permit tcp host 192.168.40.3 host 192.168.70.100 eq ftp
access-list 103 permit tcp host 192.168.50.3 host 192.168.70.100 eq ftp
access-list 103 permit tcp host 192.168.30.100 host 192.168.70.100 eq ftp
access-list 103 permit tcp host 192.168.60.100 host 192.168.70.100 eq ftp
access-list 103 deny tcp host 192.168.30.2 host 192.168.70.100 eq ftp
access-list 103 deny tcp host 192.168.50.2 host 192.168.70.100 eq ftp
access-list 103 deny tcp host 192.168.60.2 host 192.168.70.100 eq ftp
access-list 103 deny tcp 192.168.10.0 0.0.0.255 host 192.168.70.100 eq ftp
access-list 103 permit tcp any host 192.168.70.100 eq ftp
access-list 103 permit icmp 192.168.20.0 0.0.0.255 host 192.168.70.100 echo
access-list 103 permit icmp 192.168.50.0 0.0.0.255 host 192.168.70.100 echo
access-list 103 deny icmp host 192.168.10.3 host 192.168.70.100 echo
access-list 103 deny icmp host 192.168.30.3 host 192.168.70.100 echo
access-list 103 deny icmp host 192.168.40.3 host 192.168.70.100 echo
access-list 103 deny icmp host 192.168.60.2 host 192.168.70.100 echo
access-list 103 permit icmp any host 192.168.70.100 echo
access-list 103 permit ip any any
in fa0/1
ip acc 103 out(Router 0, 2, 4-Telnet)
access-list 5 permit host 192.168.40.2
access-list 5 permit host 192.168.60.100
access-list 5 permit 192.168.30.0 0.0.0.255
access-list 5 permit 192.168.50.0 0.0.0.255
access-list 5 deny host 192.168.10.3
access-list 5 deny host 192.168.20.3
access-list 5 deny host 192.168.40.3
access-list 5 deny host 192.168.60.2
access-list 5 permit any
line vty 0 4
access-class 5 in
password 1234
login(Switch 0, 3, 5-Telnet)
interface Vlan1
ip address 192.168.10.50 255.255.255.0
ip default-gateway 192.168.10.1
access-list 5 permit host 192.168.40.2
access-list 5 permit host 192.168.60.100
access-list 5 permit 192.168.30.0 0.0.0.255
access-list 5 permit 192.168.50.0 0.0.0.255
access-list 5 deny host 192.168.10.3
access-list 5 deny host 192.168.20.3
access-list 5 deny host 192.168.40.3
access-list 5 deny host 192.168.60.2
access-list 5 permit any
line vty 0 4
access-class 5 in
password 1234
login미션 정리)
이전까지는 Deny, Permit을 하고나서Permit any 선언을 한줄로 해결하려고 했다.
그래서 되야할 기능은 안되고 되면 안될 기능이 되는 현상이 발생하였는데
서비스(tcp-www, ftp, telnet / udp-domain / icmp-echo)별로 해주어야 할 Permit과 Deny를 선언 한 뒤access-list (넘버) permit (서비스) any host (주소) (프로토콜)를 붙여준다면 필터링의 조건을 확실히 설정할 수 있으며permit any any에서도 설정한 서비스 필터링에 영향이 안가도록 조건을 확실히 걸어줄수 있다.