Everything in AWS is 100% API-driven
AWS Services API Endpoints
AWS services are terminated with a service API endpoint that accepts REST API requests and methods.
Each service API endpoints are terminated regionally. Even if the service is provided at a global reources, there are still regional endpoints to access.
Ways of Accessing Endpoints
Console
Require username and password.
All it's doing is invoking the forms that are filled out to the API endpoints.
Pros:
- Path of least resistance
- Always currently updated
- Combine actions
For example: to create an ELB using a CLI,
there are multiple steps required but
console can combine all the required actions into one step.
- Provide suggestions for the configCons:
- It cannot be automated
- Can't scale (if asked to create 100 VPCs on a console!?)
- Human error
- Frequent UI changesCLI
Used for centralizing and optimizing automation.
Basics
$ aws [options] <command> <subcommand> [parameters]
options: regions, outputformat, query filters, etc.
command: corresponds to a service API endpoints
subcommand: action to take
parameters: specific options for the command
How to Connet CLI with Session Manager on Amazon Linux
Click on the instance
Click connect and select session manager
Once the shell is opened, update the AWS CLI
Check AWS CLI version
$ aws --version
run bash
$ bash
go to root dir
$ sudo -s
$ cd /tmp
Run through the instructions in docs for linux
Update the old CLI with v2
cd /bin
mv aws aws.old
ln -s /usr/local/bin/aws /bin
aws --versionConfigure CLI
$ aws configure
Access Key & Secret Access Key: if the instance is using an IAM role, there's no need to configure this part
Region: select your region
Ouput: json
Check connection
$ aws ec2 describe-instances
SDK
Connect AWS Python SDK
Connect to CLI for permissions.
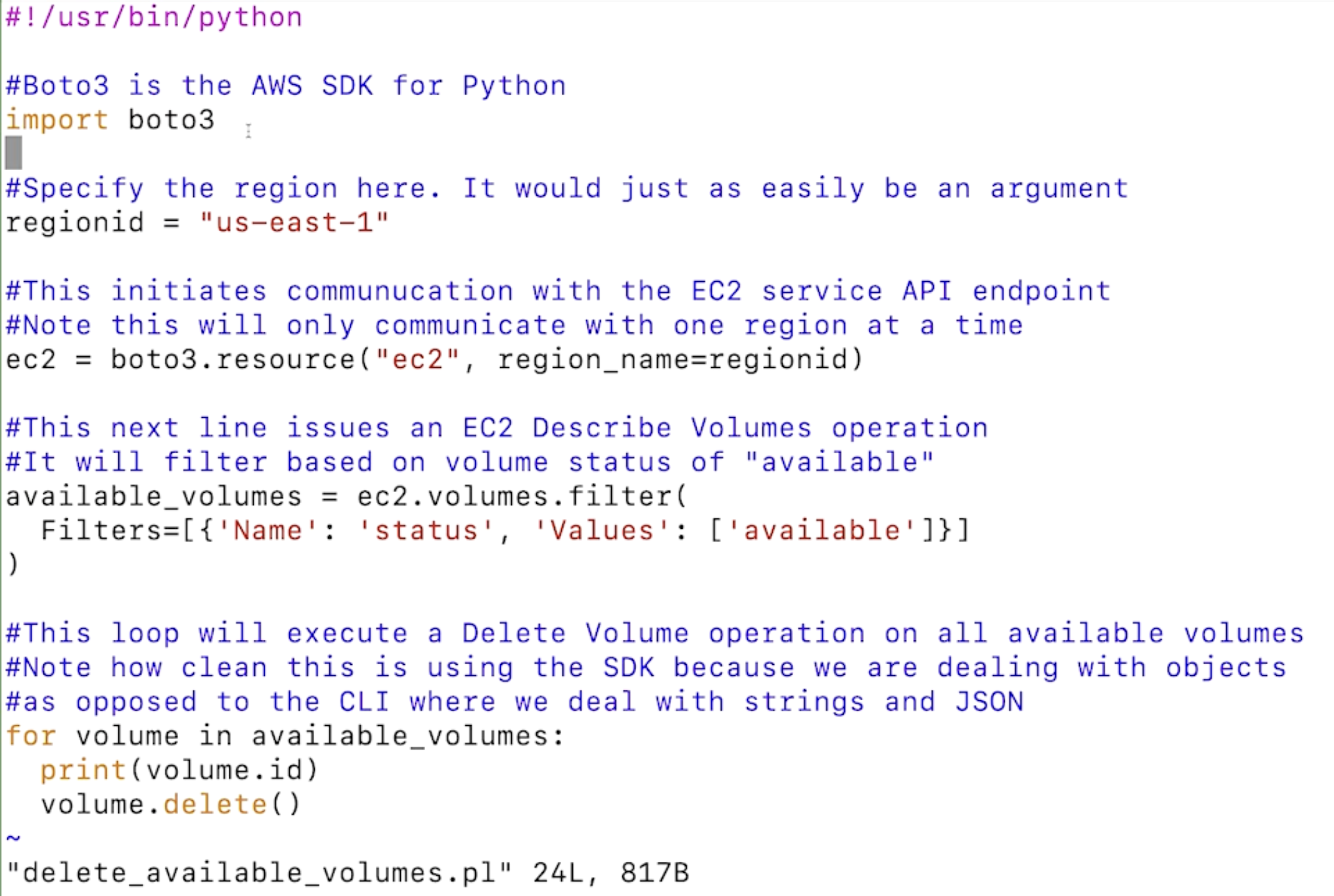
You can run the below code locally to destroy leftover volumes of an EC2 instance.
Create IAM Role
Click on Create Role.
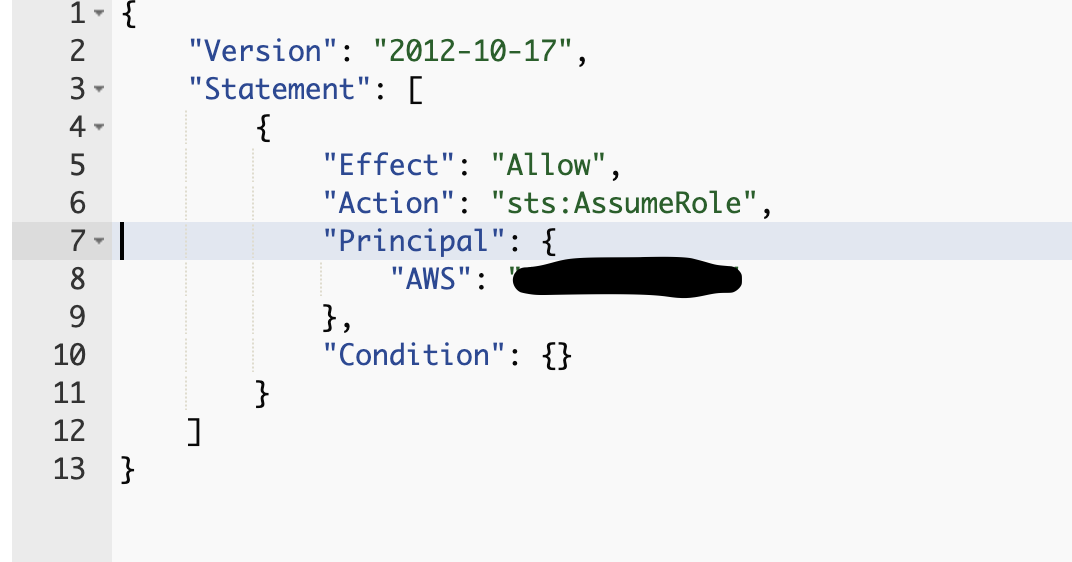
Since we want to create a Role for the AWS Account, select AWS Account
After selecting the above Permission that we've created, notice how the Principal is given the AWS account ID of the Root User.
Assume IAM Role with CLI
Copy the ARN for the Role created above.
We can attach this Role to an existing User via CLI.
assume_role_policy.json file
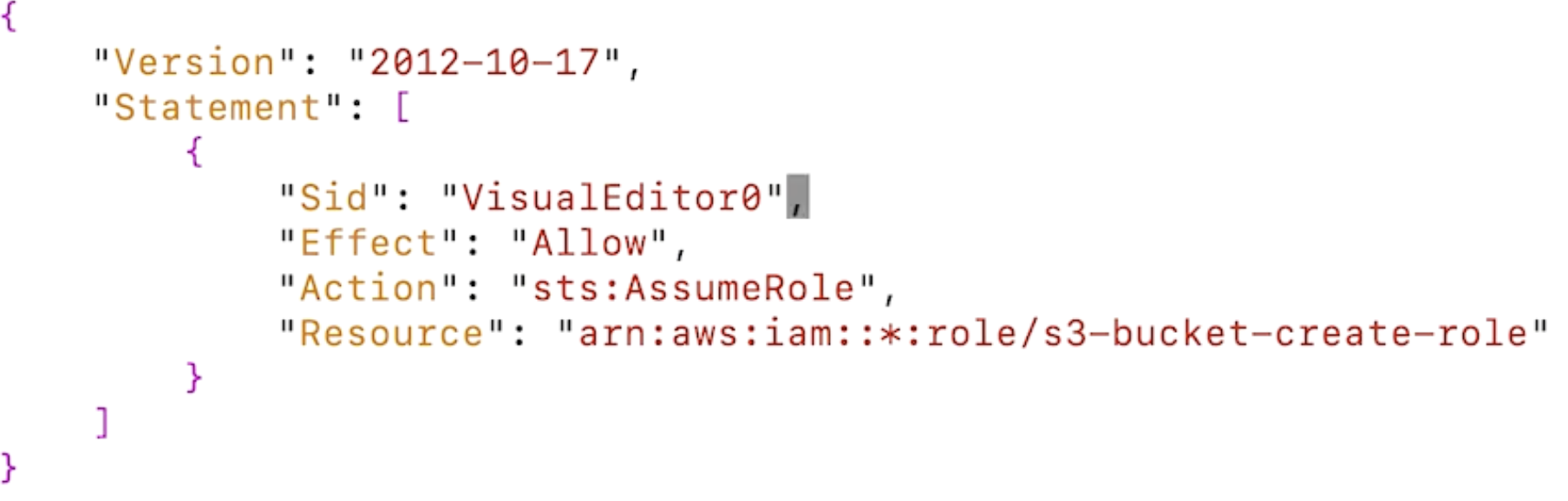
The asterisk can be more specific to match the corresponding ARN.
Input the above code in Create Policy as JSON with a name that will be attached to a User.
Go to Users tab, select the User and go to add permissions.
Select attach existing policy directly.
Go to the CLI and edit ~/.aws/config file. This file is generated when running aws configure
[profile PROFILE_NAME]
role_arn = YOUR_ARN
source_profile = deafult OR YOUR_DESIRED_PROFILECreate S3 Bucket Using this profile
After saving the config file run this command to create an S3 Bucket using CLI
$ aws --profile PROFILE_NAME s3api create-bucket --bucket BUCKETNAME --region REGION
Go to S3 console to verify that the bucket is created.
Disclaimer
This summary is made possible by Oreilly's AWS, 3rd Edition - Chad Smith.
If the above post violates any copyright permissions, please let me know!

