Introduction
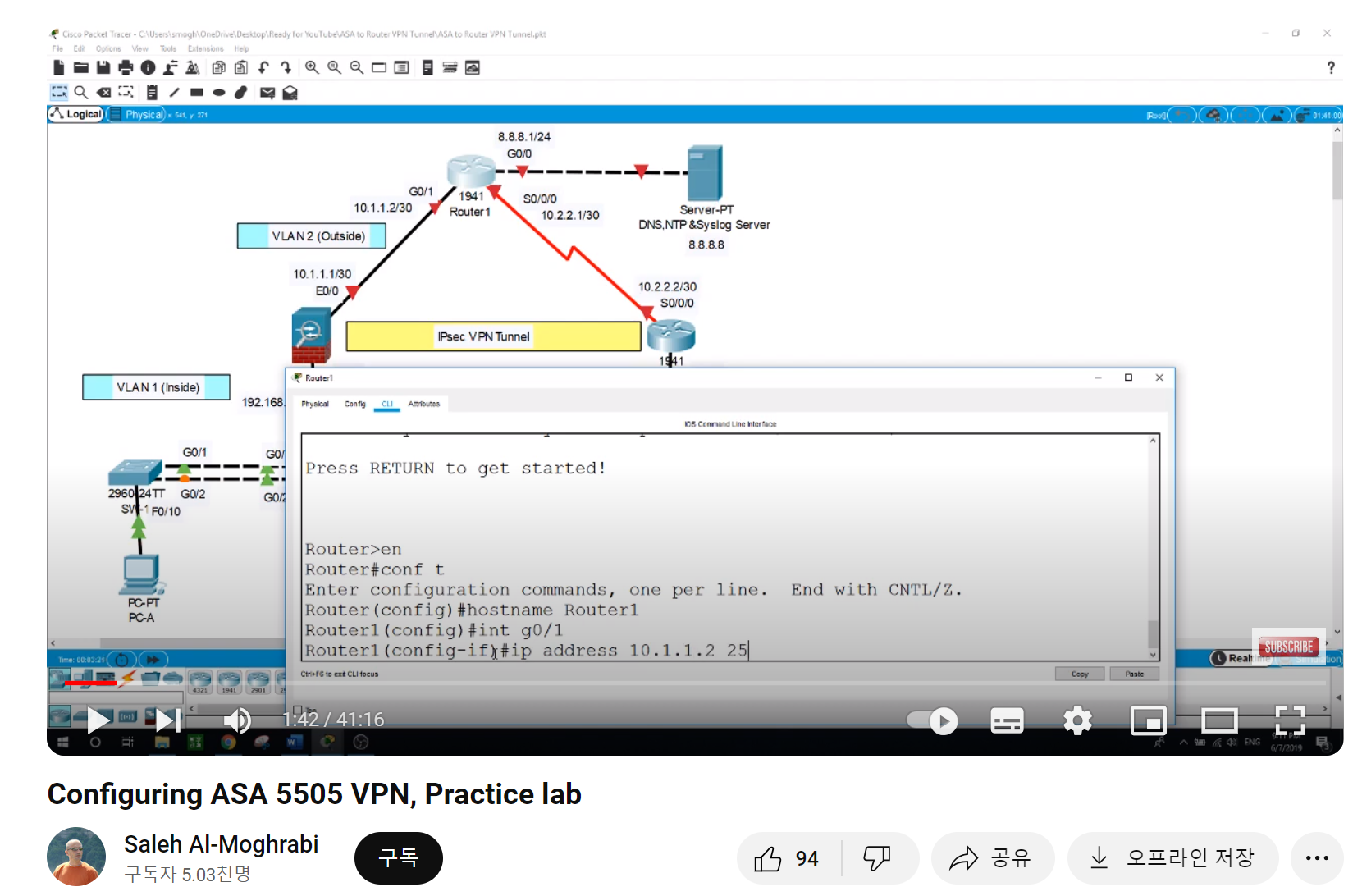
Through a Google search, I could find the following lab, which helps me understand VPN Tunnel with Cisco ASA:
It provides the .pkts and .docx files for practice.
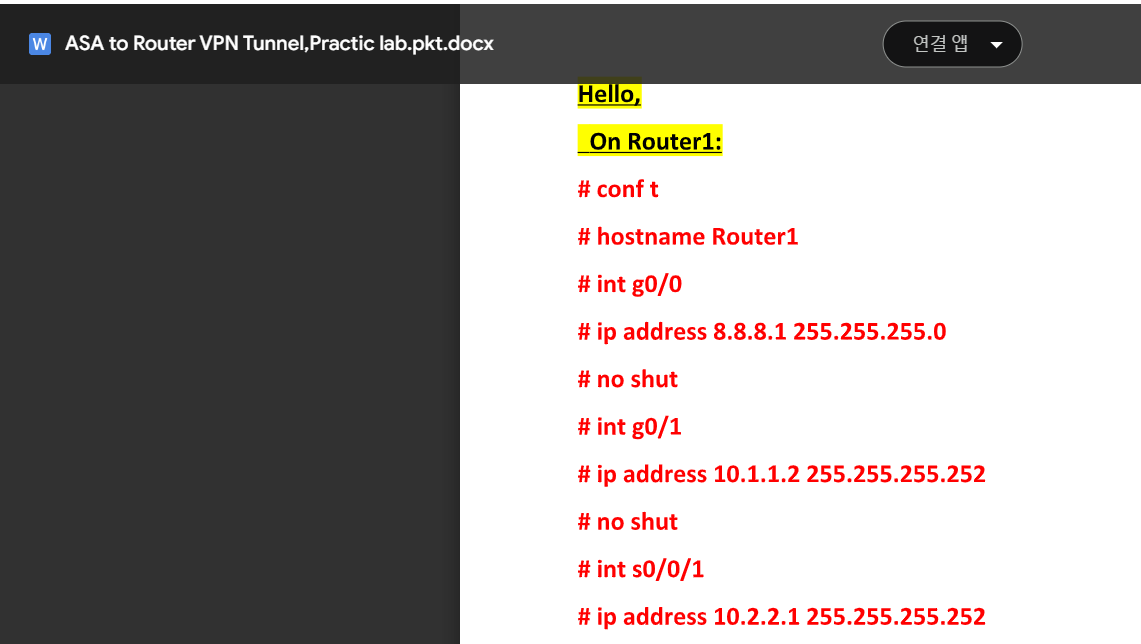
In the .docs file, it guides how to configure VPN Tunnel with detailed commands:
I will just follow the steps described therein, focusing on understanding each command in depth.
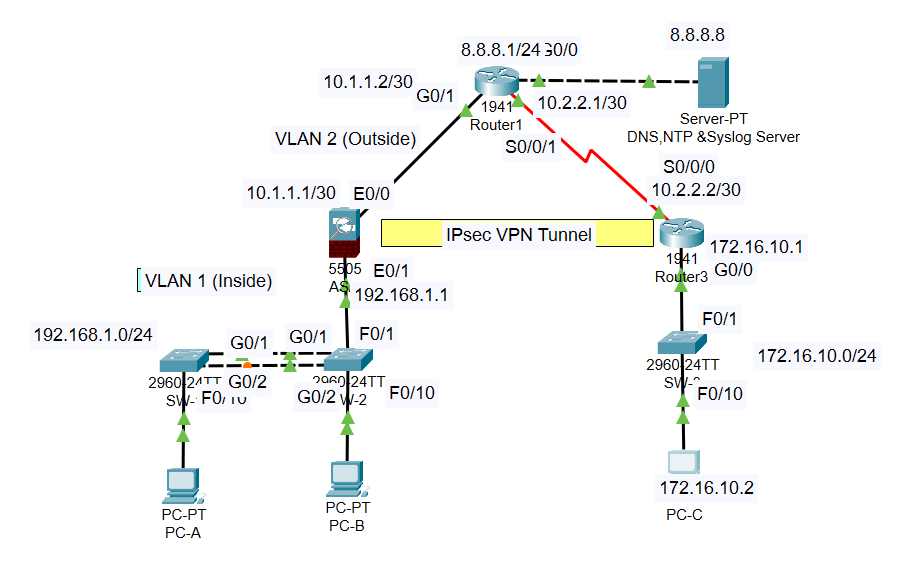
Network Topology
Step-by-Step Configuration
Basic Network Setup
I will skip the explanation for this process.
SSH Setup On Router3
# ip domain-name ccnasecurity.com
# crypto key generate rsa
# yes
# 1024
# ip ssh version 2
# username Admin1 secret Admin1
// Configure AAA for authentication
# aaa new-model
// Use the local database as the default setting for authentication
# aaa authentication login default local
# line vty 0 15
# logging synchronous
# login authentication default
# transport input sshSyslog and NTP Setup On Router3
//Enable syslog on the server, the server will act as DNS, NTP and Syslog server.
# exit
# logging host 8.8.8.8
//On the server, make sure to enable authentication for NTP , the key is 1 and the password is “ cisco”
//On Router3:
# ntp authenticate
# ntp authentication-key 1 md5 cisco
# ntp trusted-key 1
# ntp server 8.8.8.8 key 1
# ntp update-calendar // Apply NTP synchronization value to the device's hardware clock rateDHCP and SSH Setup On ASA
# hostname ASA
//Configure the domain name ccnasecurity.com
# domain-name ccnasecurity.com
# enable password cisco
//Next, configure AAA to use the local database for SSH user authentication for console access.
# aaa authentication ssh console LOCAL
//Next, add a user to the local database for administrator console access
# username Admin1 password Admin1
//Next, we will configure ASA to accept SSH connections from hosts on the inside LAN
# ssh 192.168.1.0 255.255.255.0 inside
//Next, I will configure the ASA interfaces:
# int vlan 1
# nameif inside
# security-level 0
# ip address 192.168.1.1 255.255.255.0
# no shut
# int e0/1
# switchport access vlan 1
# no shut
# int vlan 2
# nameif outside
# security-level 0
# ip address 10.1.1.1 255.255.255.252
# no shut
# int e0/0
# switchport access vlan 2
# no shutdown
# exit
//Next, I will configure a default route on the ASA
# route outside 0.0.0.0 0.0.0.0 10.1.1.2
//Next, we will generate RSA key pair to support the SSH connection
# crypto key generate rsa modulus 1024
//Next, we will configure the ASA as a DHCP server
dhcpd address 192.168.1.10-192.168.1.20 inside
# dhcpd dns 8.8.8.8
# dhcpd option 3 ip 192.168.1.1
# dhcpd enable insideConfigure trunk mode between SW1 and SW2
vlan 10
name Native
int range g0/1-2
switchport mode trunk
switchport trunk native vlan 10 ; Assign traffic which has no VLAN tag into VLAN 10 Assignment of SPF Priority
//On SW-1:
conf t
spanning-tree vlan 1 root primary
//On SW-2:
conf t
spanning-tree vlan 1 root secondarySetting Port Security for End Devices
int f0/10
switchport mode access
switchport access vlan 1
switchport port-security
switchport port-security maximum 1
switchport port-security mac-address sticky
switchport port-security violation shutdown
spanning-tree portfast
spanning-tree bpduguard enable