Sherlock Scenario
A major incident has recently occurred at Forela. Approximately 20 GB of data were stolen from internal s3 buckets and the attackers are now extorting Forela. During the root cause analysis, an FTP server was suspected to be the source of the attack. It was found that this server was also compromised and some data was stolen, leading to further compromises throughout the environment. You are provided with a minimal PCAP file. Your goal is to find evidence of brute force and data exfiltration.
Task 1
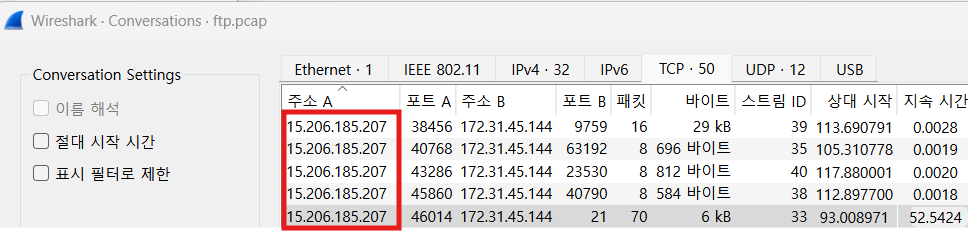
What is the attacker's IP address?
ANSWER:
15.206.185.207
Task 2
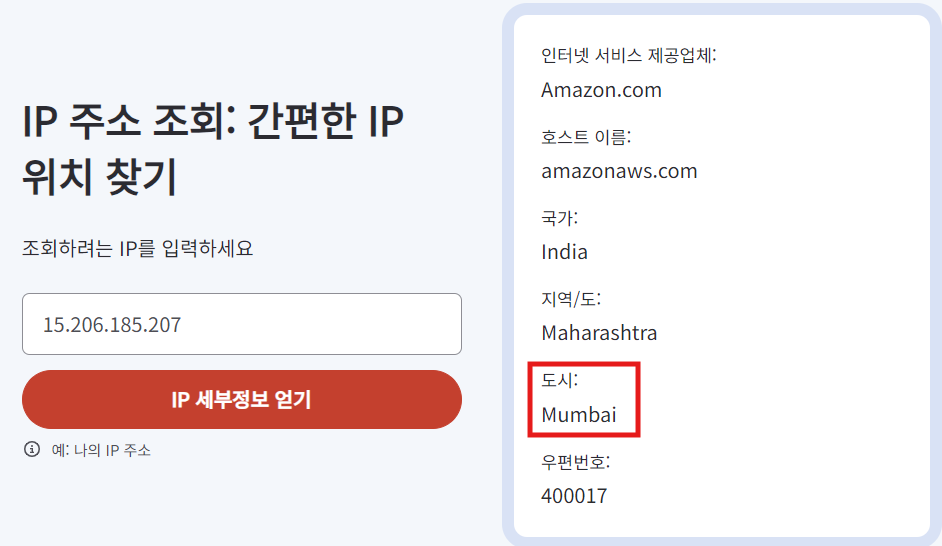
It's critical to get more knowledge about the attackers, even if it's low fidelity. Using the geolocation data of the IP address used by the attackers, what city do they belong to?
ANSWER:
Mumbai
Task 3
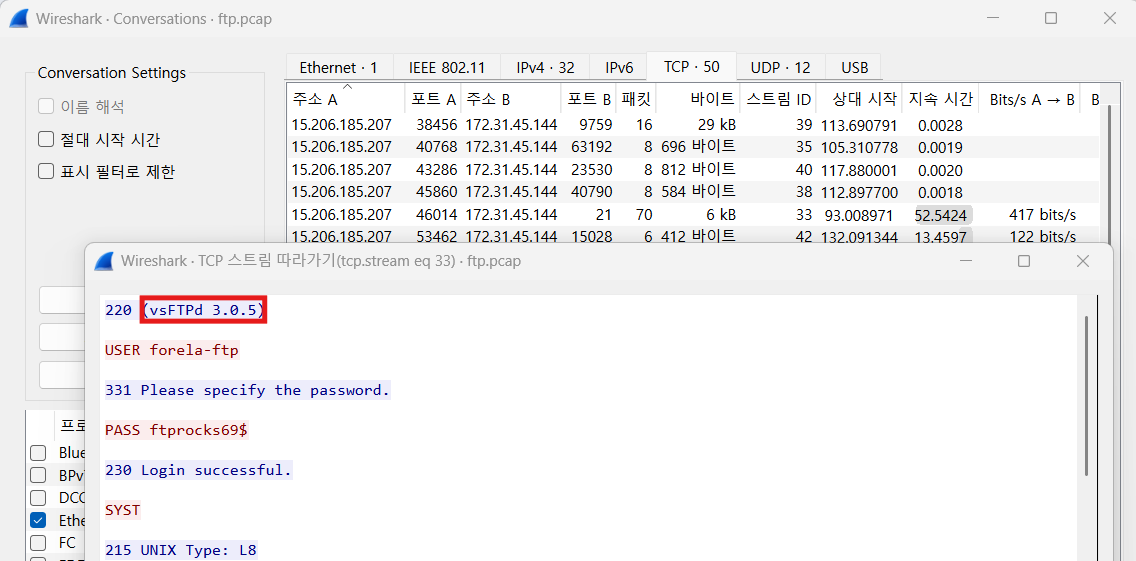
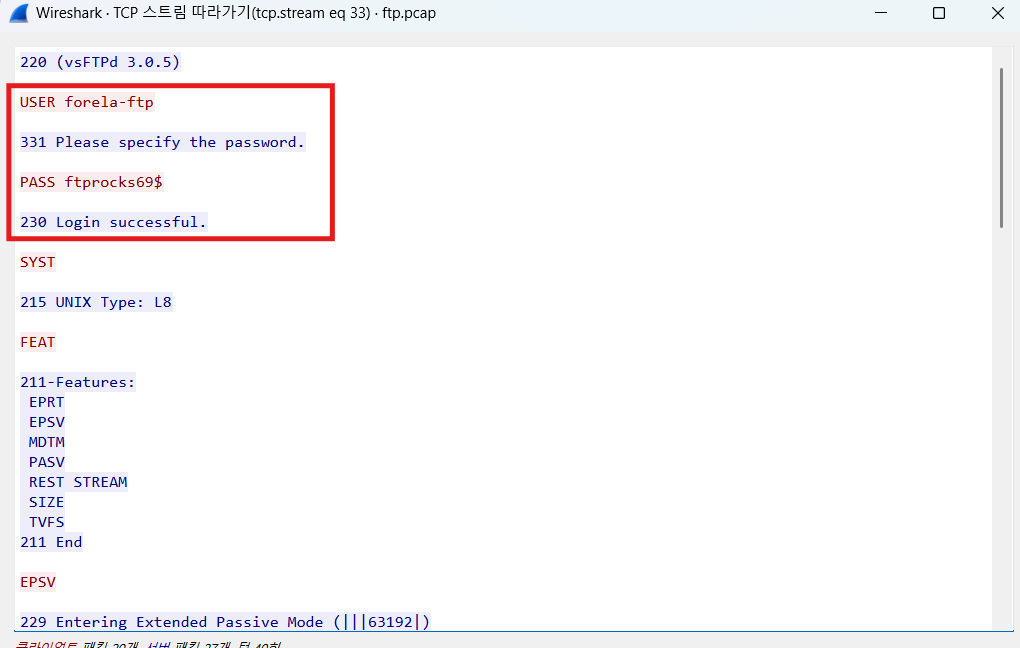
Which FTP application was used by the backup server? Enter the full name and version. (Format: Name Version)
ANSWER:
vsFTPd 3.0.5
Task 4
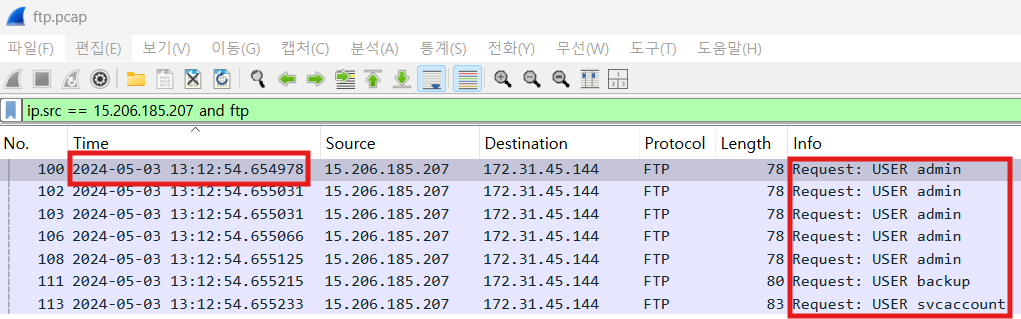
The attacker has started a brute force attack on the server. When did this attack start?
AWSWER:
2024-05-03 04:12:54
분명히 잘 입력했는데 안되어서 뭐가 문제인가 했더니, 한국은 UTC+9라서 와이어샤크에 나타난 시간-9 를 해주었더니 정답으로 나왔다.
Task 5
What are the correct credentials that gave the attacker access? (Format username:password)
Task 6
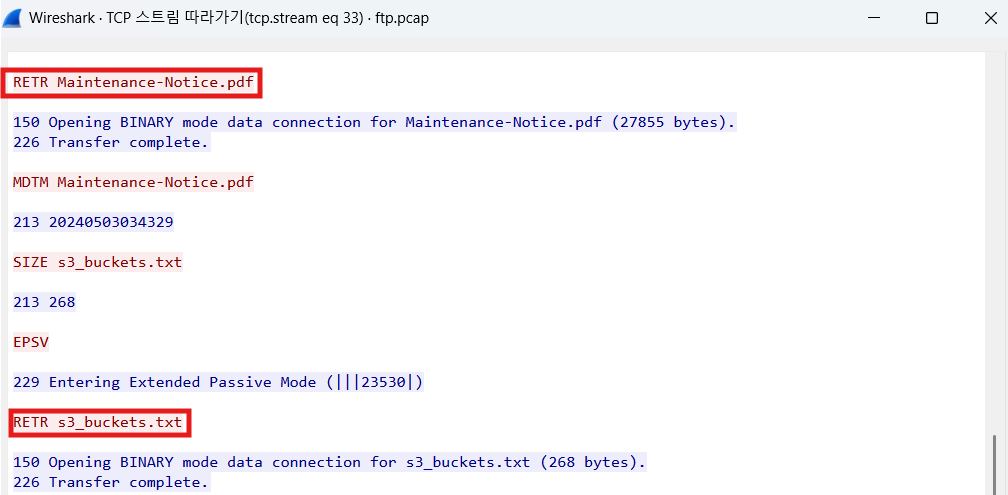
The attacker has exfiltrated files from the server. What is the FTP command used to download the remote files?
ANSWER:
RETR
- RETR : 원격지의 파일을 가져오기
- MDTM : 파일의 수정 시간 확인
- NLST : 원격 디렉토리 목록
- STOR : 원격지 파일 저장
- SIZE : 파일 사이즈 리턴
Task 7
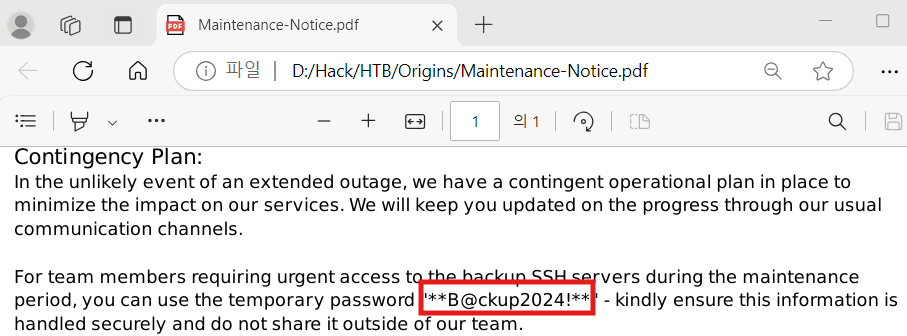
Attackers were able to compromise the credentials of a backup SSH server. What is the password for this SSH server?
ANSWER:
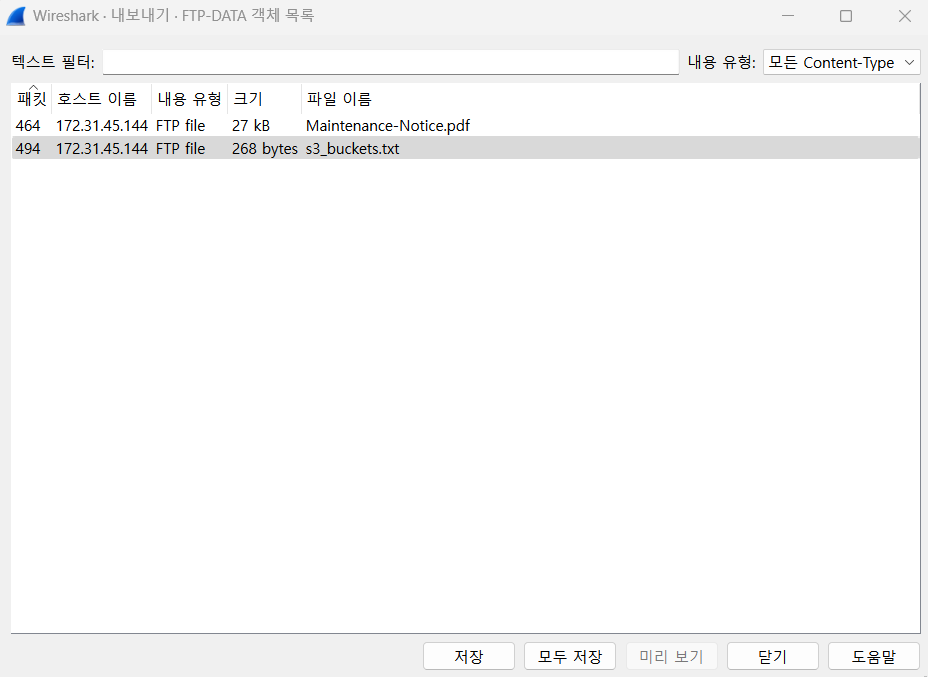
파일-내보내기-FTP-DATA 를 들어가게 되면 위와 같이 공격자가 다운로드한 파일들을 볼 수 있다. 모두 저장을 누르게 되면 아래와 같이 로컬PC로 다운받아 볼 수 있다.
Maintenace-Notice.pdf를 들어가게 되면 password를 확인할 수 있다.
Task 8
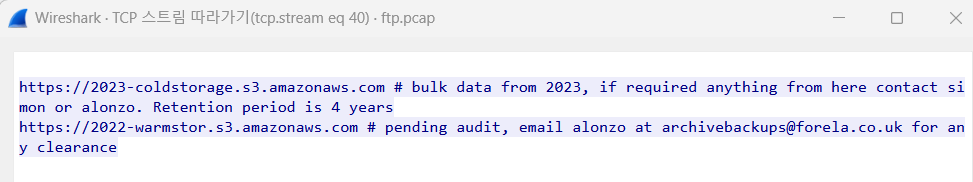
What is the s3 bucket URL for the data archive from 2023?
ANSWER :
https://2023-coldstorage.s3.amazonaws.com
스트림 따라가기로 보게 되면 아래의 내용을 확인해볼 수 있다.
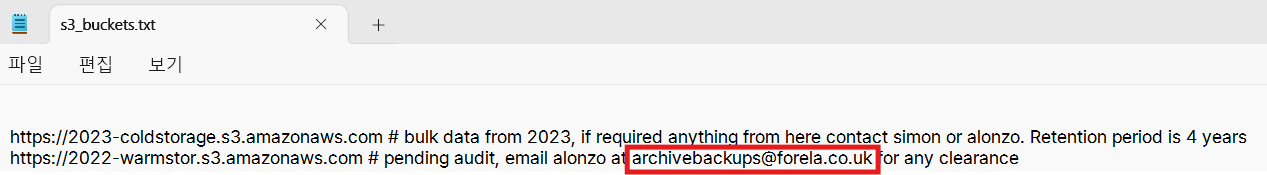
TASK7을 풀었다면 다운로드 받은 파일 중 s3_buckets.txt에서도 확인 가능하다.
Task 9
The scope of the incident is huge as Forela's s3 buckets were also compromised and several GB of data were stolen and leaked. It was also discovered that the attackers used social engineering to gain access to sensitive data and extort it. What is the internal email address used by the attacker in the phishing email to gain access to sensitive data stored on s3 buckets?
ANSWER:
archivebackups@forela.co.uk
이 문제에서 삽질파다가.. s3_buckets.txt 다시 확인하니 찾을 수 있었다ㅎㅎ..^^
재밌네