👀Overview
- points and types of attack
- network considerations
- implementation considerations (수행시 고려사항)
💥 Points of Attack
currently, attacker's job is getting easier
(all data types are digitalized and intergrated in internet)
types of attacks
Passive
- attacker just listen
Active
- not only listen, but may add / delete / modify / delay
👩🏻💻 Network Considerations
security can applied at various points(layers) in network
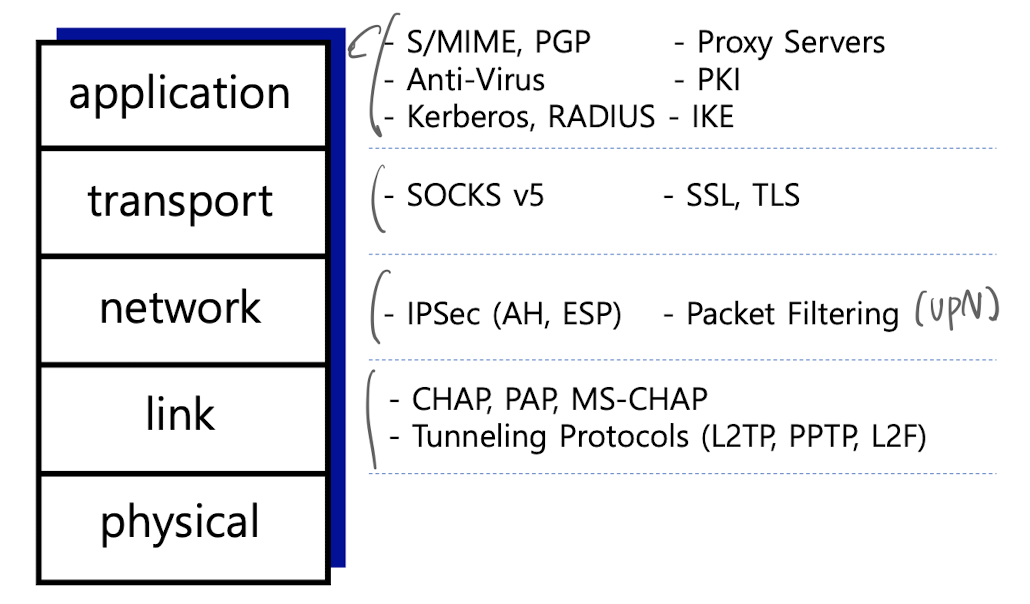
link-to-link layer
content, headers are encrypted
e.g.)wired : ethernet, wireless : WEP, 802.11i, 802.1x
network layer
all data from one node(one IP) to another are encryted
provides authentication, confidentiality, key management
e.g.) IPsec, VPNs
transport layer
- between TCP <-> application that use TCP
- confidentiality using symmetric encryption
- data intergrity using MAC(message authentication code)
includes protocol mechanisms to enable two TCP users to dtermine the security mechanisms and services they will use.
e.g) SSL(Secure Socket Layer), SSH(Secure Shell), HTTPS(HTTP on SSL)
🤔 Implement Consideration
| Software | Hardware | |
|---|---|---|
| Pros | cheap to reproduce and distribute | faster processing / temper-resistant(harder to break), 'token' can be carried by user |
| Cons | almost impossible to protect secret parameters(ex)encryption keys) if an attacker has access to the device | more expensive |
some level of approval can only be obtained with hardware!
