3.3.2 Dat phase signals.
There are several AHB data phase signals. For signals from bus masters to slaves
| Signals | Descriptions |
|---|---|
| HWDATA[n-1:0] | Write data. Data bus with "n" is typically 32, but can also be 64-bit. |
| HWUSER[x-1:0] | This is user-defined data phase signal introduced in AHB5 connecting from the bus master to bus slaves. Potentially this can be used for write data |
Table 3.16 : Additional AHB data phase signals from bus masters to bus slaves.
| Signals | Descriptions |
|---|---|
| HRDATA[n-1:0] | Read data. Data bus width "n" is typically 32,but can also be 64-bit |
| HRUSER[x-1:0] | This is a user-defined data phase signal introduced in AHB 5 connect from bus slaves to bus masters, Potentially this can be used for : |
| HRESP/HRESP[1:0] | Bus response type. In AHB Lite and AHB 5, this signal is single bit. In AMBA 2 AHB, this is two bits |
| HREADY/HREADYOUT | HREADYOUT signals are generated from bus slaves. After the AHB slave multiplexer merges the resposes from bus slaves, the result HREADY is returned to all the bus slaves in the same AHB segment to indicate the end of the current bus phase. |
| HEXOKAY | Exclusive access is okay. This was introduced in AHB5. If the bus tansfer is indicated as exclusive access. |
-> AHB 슬레이브 멀티플렉서는 모든 버스 슬레이브들의 응답을 병합하여 단일 HREADY 신호를 생성하여 현재 버스 단계가 종료되었으며 트랜잭션이 완료되었음을 나타냅니다.
HRDATA and HWDATA
Data bused on AHB systems are usually 32-bit or 64-bit. For Cortex-M processors with AHB interface, the data connections on the AHB are 32-bit only. Aside from word transfers, AHB also allows transfers of byte and half-word data. The position of the data on the bus depends on the transfer size as well as the address. For example, for byte transfer, the data position on the bus is
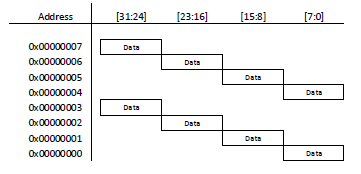
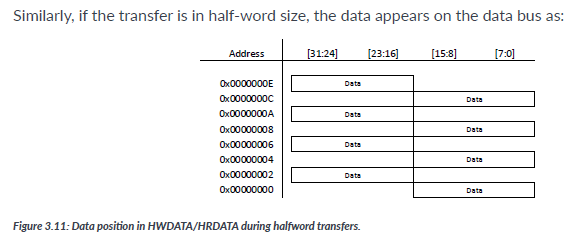
For word transfers, the whole 32-bit is used.
AMBA 2 AHB, AHB LITE and AHB 5 support aligned transfers only. Unaligned transfers are not supported.
Aligned transfers have address values which are a multiple of the transfer size. For example, word transfer addresses have address values that are multiples of 4, and half-word transfers have address values that are multiples of 2. Byte transfers are always aligned.
HRESP
The HRESP signals are responses from the AHB slaves. In AHB for AMBA 2, these can be OKAY, ERROR, RETRY, or SPLIT. Hence the HRESP is two-bit wide. For AHB-LITE and AHB5, they can only be OKAY or ERROR and are one bit wide.
When an AHB slave receive a transfer, it should carry out the transfer as requeseted by the AHB master. If needed, it can insert wait states during the data phase. In normal circumstance, an AHB slave shoul generate an OKAY resoinse status, indicated by zeros in HRESP[1:0].
| HRESP[1:0] | Response | Description |
|---|---|---|
| 00 | OKAY | Transfer carried out successfully |
| 01 | ERROR | An error occurred |
| 10 | RETRY | The AHB slave cannot carry out the transfer immediately. The AHB master should rety the transfer. |
| 11 | SPLIT | The AHB slave cannot carry out the transfer immediately. The AHB master can drop bus ownership, and when the AHB is ready, it can request bus ownership to complete the transfer. |
The OKAY response can be a signle-cycle(no wait state is needed), but other responses are two cycles, with the possibility of additional wait states before the response is asserted. For a simple case of an AHB slave read, followed by a write, and then idle, it can look like:
Note that the AHB slave should not start to process a transfer on the AHB until it sees that HREADY is high. In the Figure 3.12, the AHB slave does not start to process the transfer request of a second transfer until HREADY is high(fourth cycle), and stats the data phase of the second transfer from the fifth cycle.
HEXOKAY
HEXOKAY is designed to support exclusive access oprations. it was introduced in AMBA 5 AHB and is generated by a global exclusive access monitor in the bus system. Exclusive access sequences contain an exclusive load and an exclusive store of the same data. The exclusive access monitor detects if the same data might have been modified by another bus master between load and store. If there is a potential access conflict, the monitor blocks the store operation and returns an exclusive fail status using HEXOKAY.
When an exclusive store occurs, HEXOKAY is asserted at the same cycle as HREADY if the global exclusive access monitor does not detect an access conflict. Otherwise , the HEXOKAY remains low(an exclusive access conflict might result if the bus slave does not support exclusive accesses).
HEXOKAY must not be asserted in the same cycle as HRESP is asserted(i.e., ERROR response).
3.3.3 Legacy arbiter handshake signals.
If using AMBA 2 AHB with multiple AHB masters, you might need to deal with the legacy arbiter handshaking signals(
3.5 AHB5 TrustZone support
TrustZone support is one of the key new features of AMBA 5 AHB. The HNONSEC signal is and address phase signal that indicates the security attribute of the transfer:
-
If HNONSEC is 1 (Non-secure), the bus interconnect must block the transfer if the address of the transfer is pointing to a Secure location.
-
If HNONSEFC is 0 (Secure), the bus master has Secure access privilge.
Please note that in Armv8-M, when a processor is in Secure state, access to Non-secure address is sindicated as Non-secure(HNONSEC == 1).
A TrustZone capable Cortex-M23/M33 processor system should have :
**_secure and Non-secure program spaces.
secure and Non-secure RAM spaces.
secure and Non-secure Peripherals_**
The definitions of Secure and Non-secure address ranges are handled by a Security Attribution Unit inside the processor and Implementation defined Attribution Unit (IDAU) which is tightly coupled to the processor(s). SAU is programmable, and IDAU is system-specific, in some cases, even the IDAU could be programmable.
To enable a high level of flexibili
Memory Protection Controller(MPC) : for the partitioning of a memory block into Secure and Non-Secure address spaces.
Peripheral Protection Controller(PPC) : for assigning bus peripaherals into Secure and Non-secure domains.
Master securiy controller : An AHB5 bus wrapper for legacy bus masters that do not support TrustZone.This handles the blocking of Non-secure transfers to secure addresses and generation of correct HNONSEC signals.
