22 정보보호
1.Security
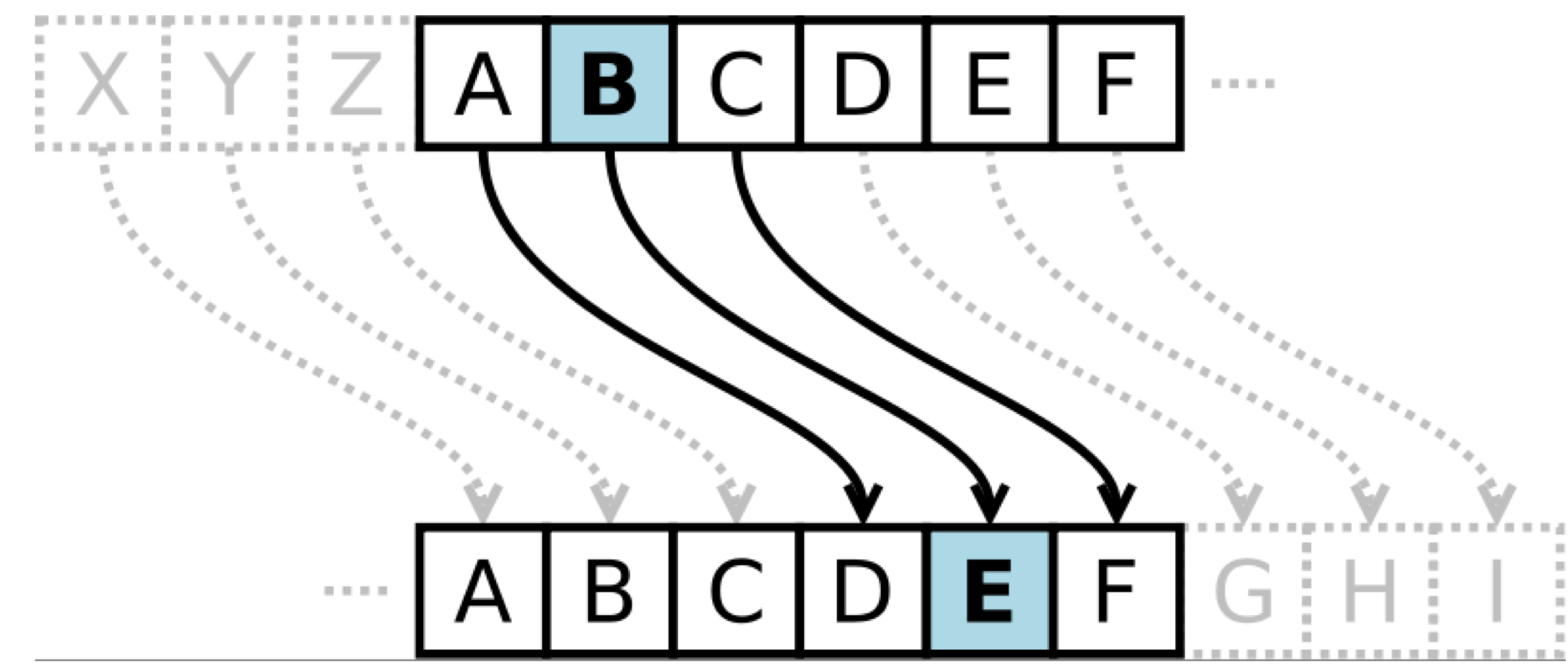
C.I.A./ A.A.A./ 대칭키 암호/비대칭키 암호/ MAC/ CA
2022년 10월 14일
2.Symmetric key cryptography
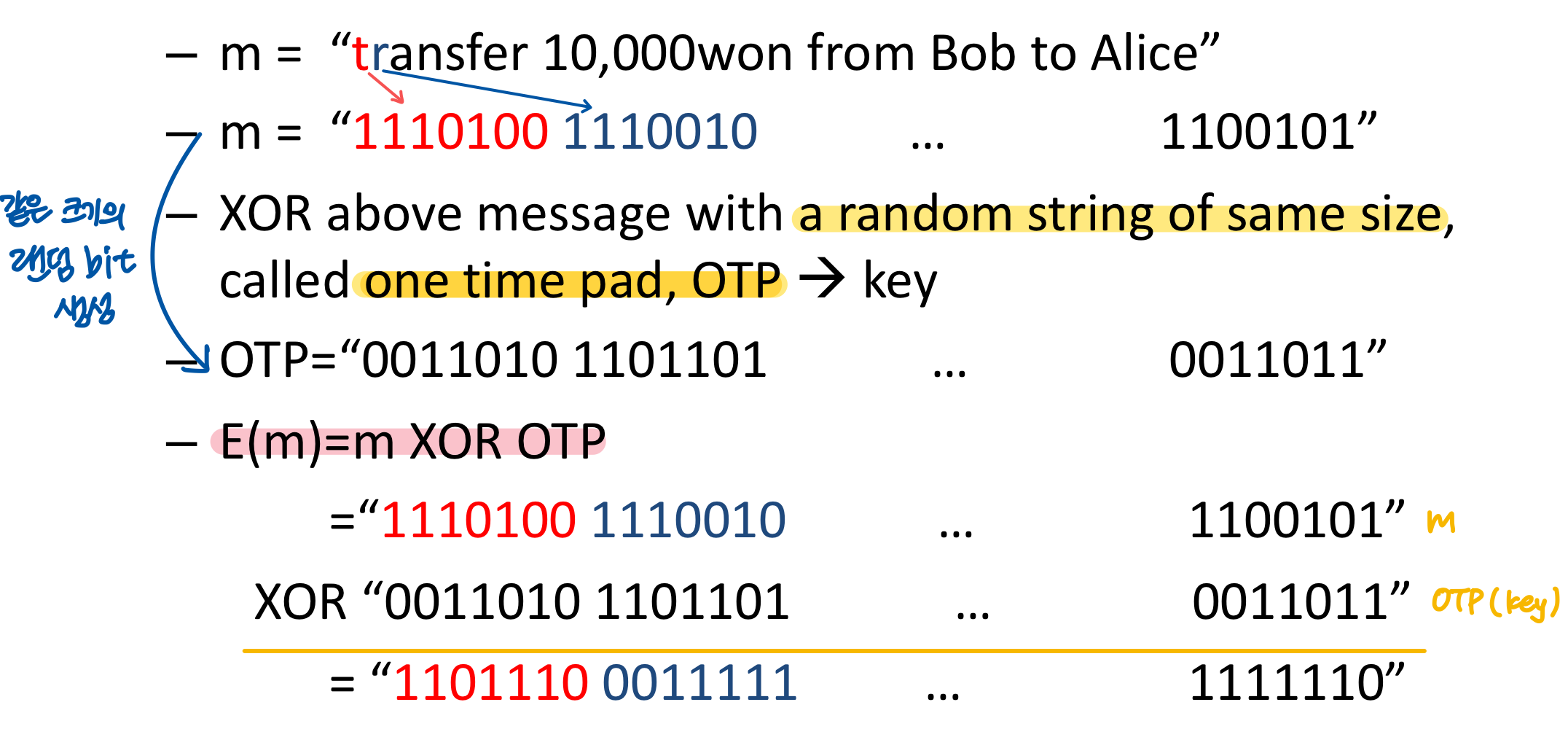
대칭키 알고리즘
2022년 10월 15일
3.Asymmetric key cryptography
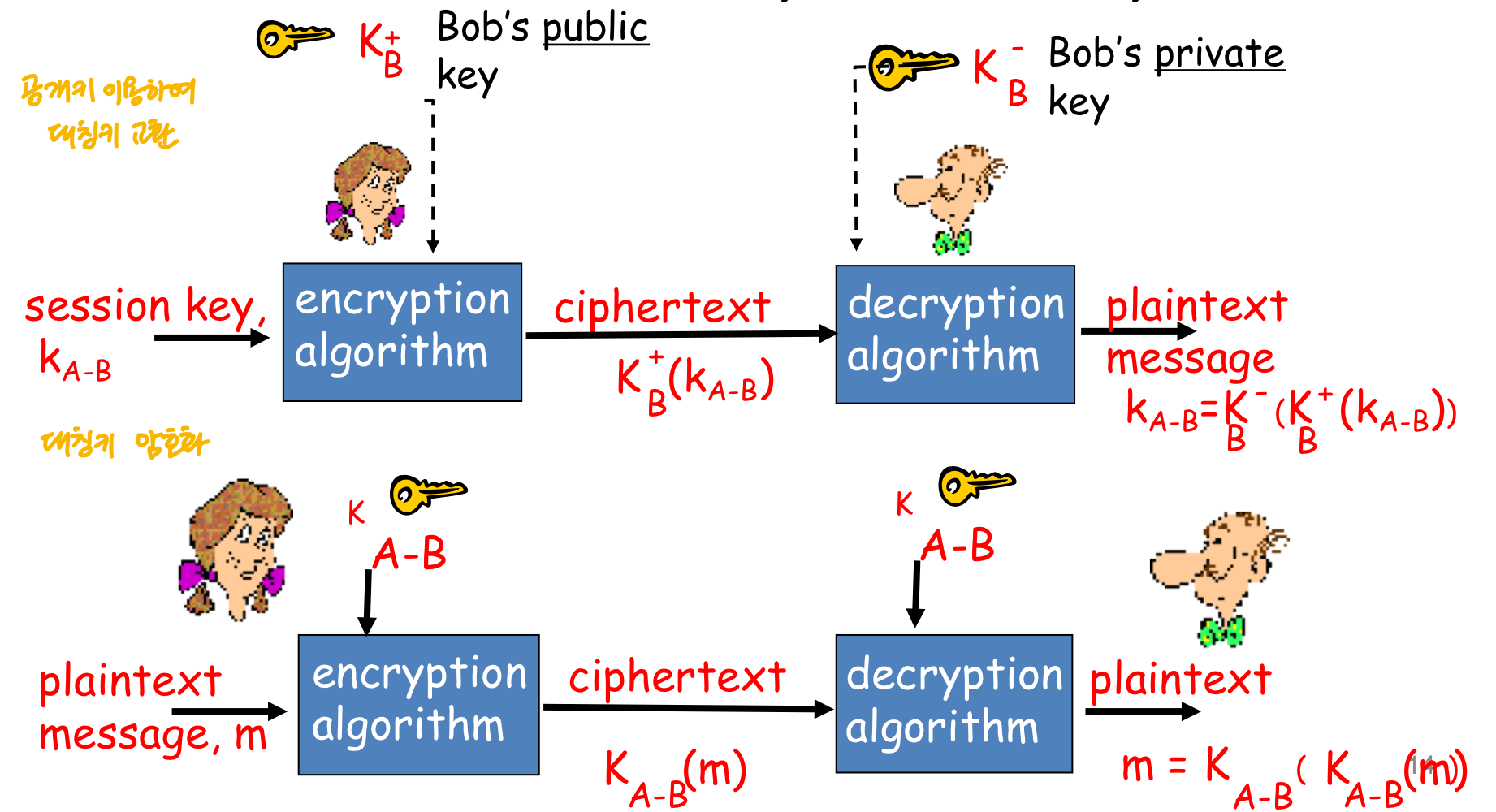
비대칭키(=공개키) 알고리즘
2022년 10월 16일
4.Hash function

메세지 요약. 속도 빠름
2022년 10월 16일
5.Applied cryptography
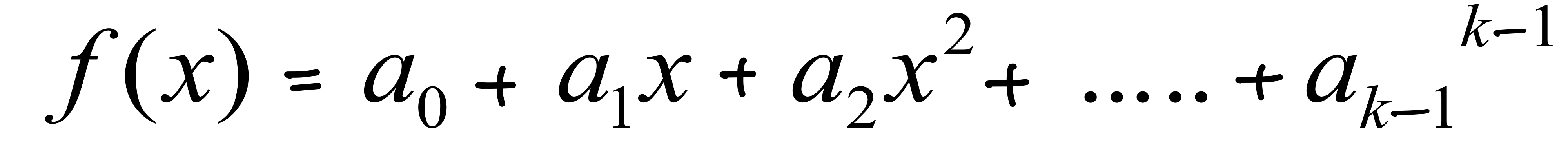
secret sharing algorithms/ blind signatures / kerberos
2022년 10월 16일
6.Security Protocol
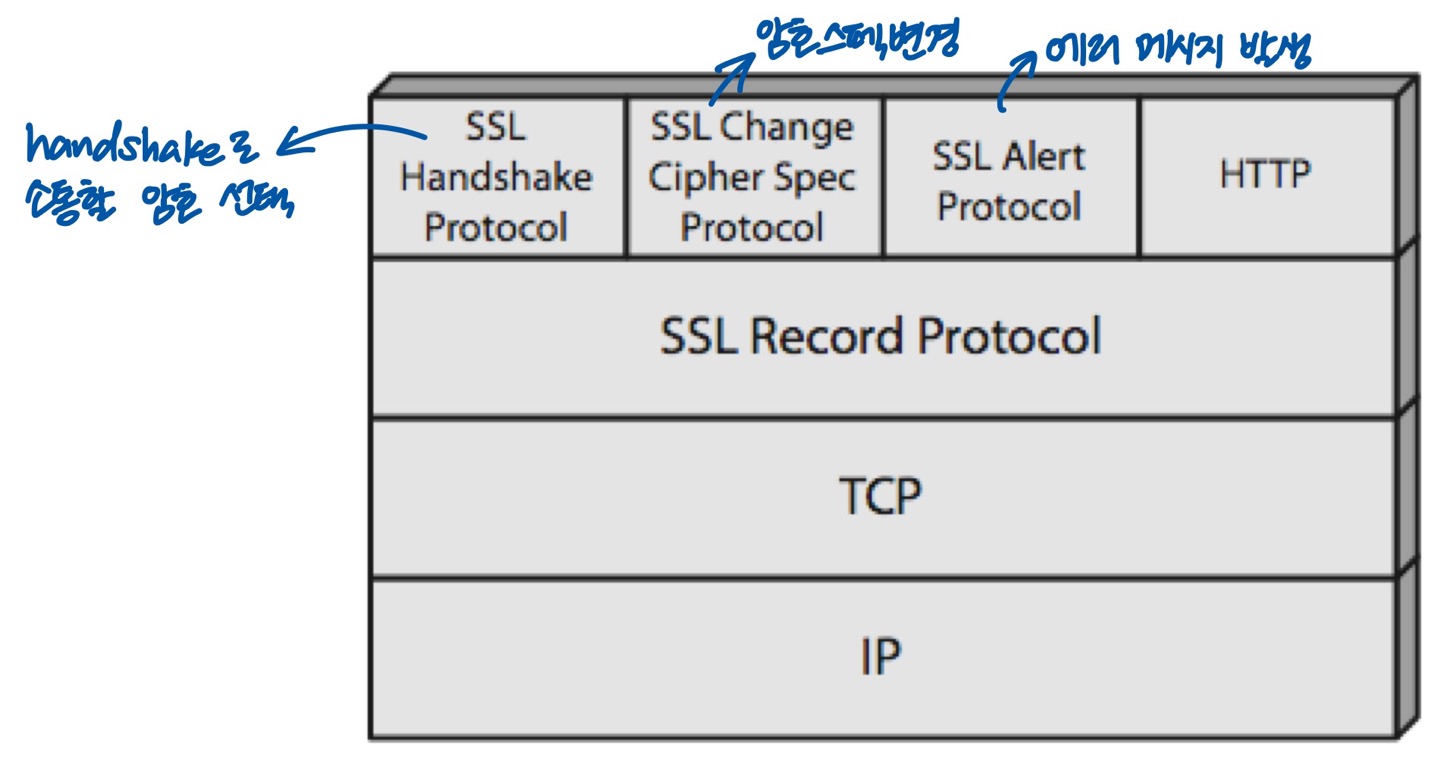
Transport Layer Security(TLS)
2022년 10월 17일
7.Certificate Authority
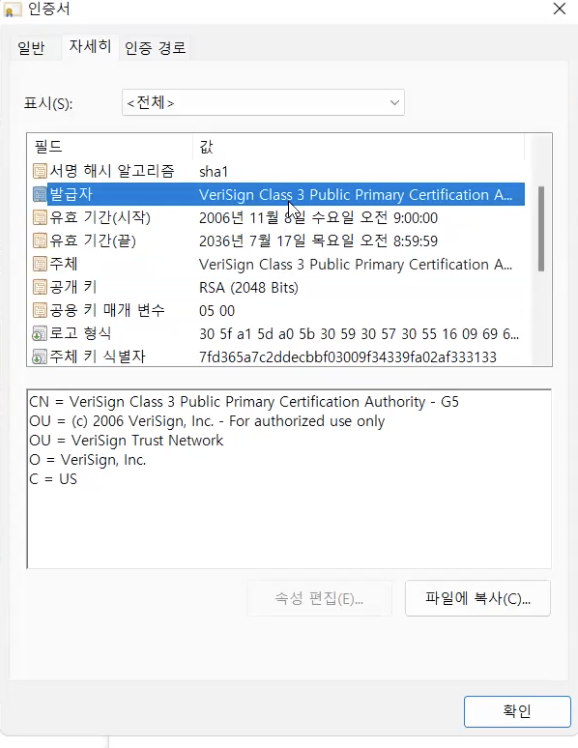
키 인증 기관
2022년 10월 17일
8.Network Security
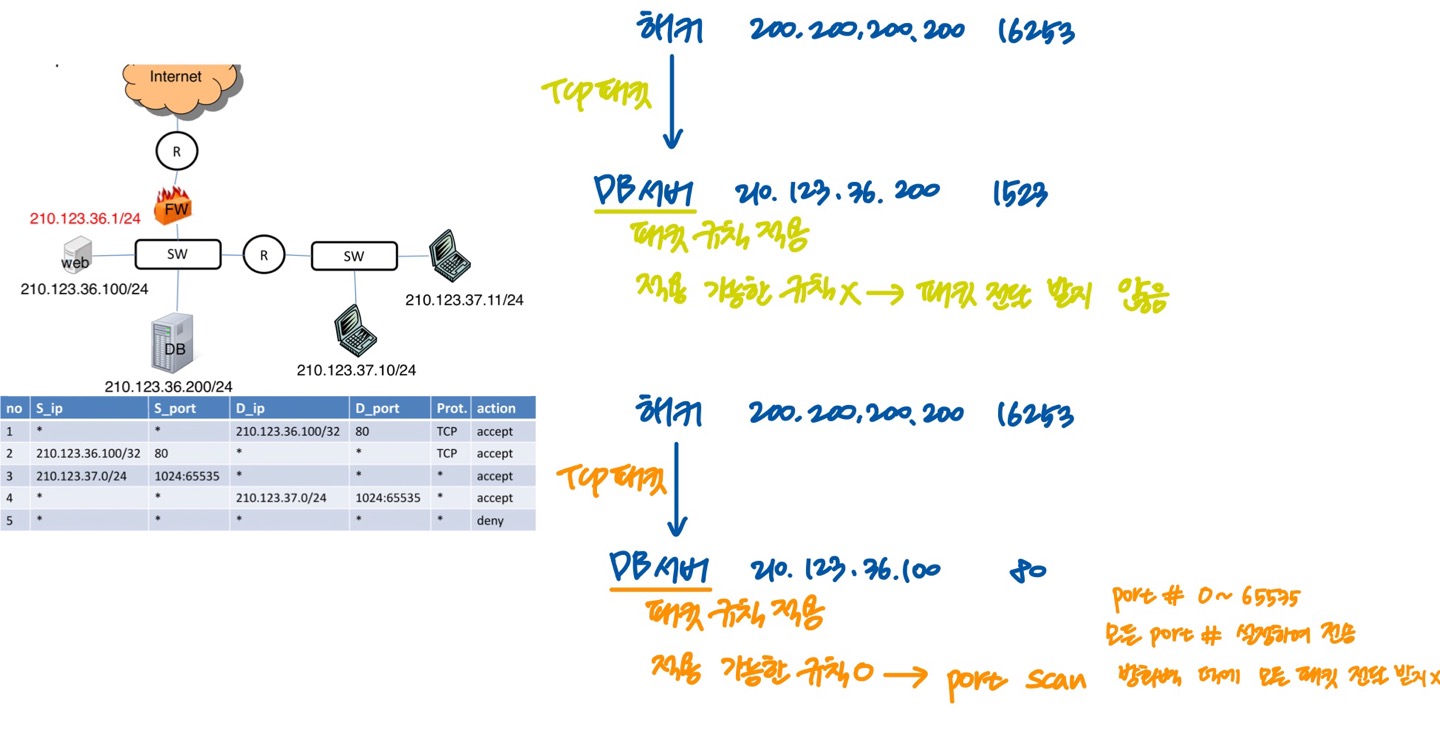
ARP spoofing/ IP spoofing/ firewall
2022년 10월 17일