Feature Summary
The Port Security remembers the MAC address of the device connected to the switch edge port and allows only that MAC address to be active on that port. If any other MAC address is detected on that port, port security feature shutdown the switch port.
The switch can be configured to send a SNMP trap to a network monitoring solution to alert that a port is disabled for security reasons.
The Port Security mechanism consists of three modes. Here are the details:
protect
초과된 트래픽을 무시하고 드롭합니다.
다른 유효한 트래픽은 허용됩니다.
해당 포트는 계속 활성 상태로 유지됩니다.
restrict
초과된 트래픽을 무시하고 드롭합니다.
해당 포트는 에러 상태로 변경되어, 관리자에게 경고를 줍니다.
허용된 MAC 주소를 가진 장치만 통과됩니다.
shutdown
초과된 트래픽이 감지되면 포트가 자동으로 비활성화되어, 해당 포트를 사용할 수 없게 합니다.
포트를 다시 활성화하려면 관리자의 개입이 필요합니다.
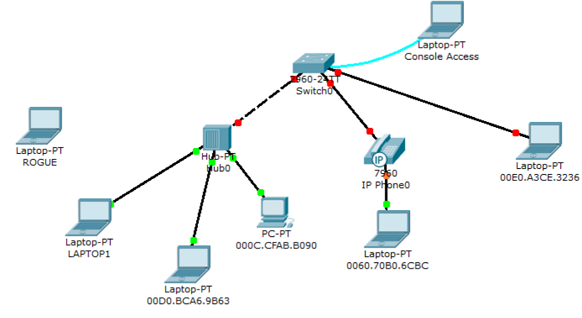
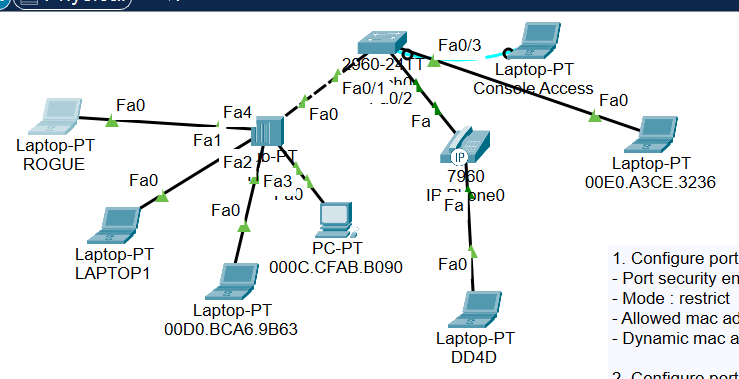
Network Diagram
Lab Instructions
There are three instructions related to the FastEthernet 0/1 through FastEthernet 0/3.
However, I think that configuring each Port Security mode in the single port FastEthernet 0/1 will be more helpful for you to understand the differences of each mode.
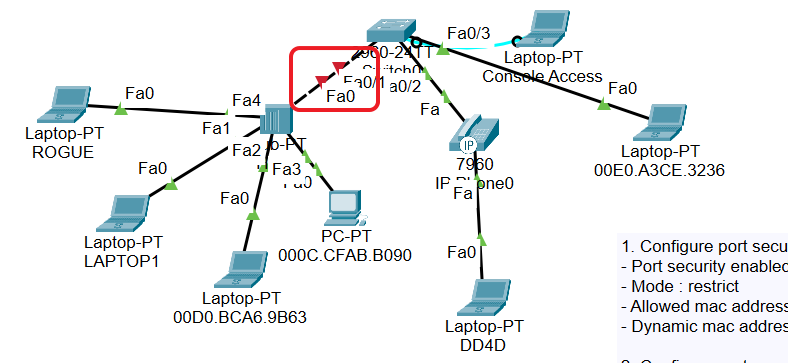
1. Configure port security on interface Fa 0/1 of the switch with the following settings :
-
Port security enabled
-
Mode : restrict
-
Allowed mac addresses : 3
-
Dynamic mac address learning.
2. Configure port security on interface Fa 0/2 of the switch with the following settings :
-
Port security enabled
-
Mode : shutdown
-
Allowed mac addresses : 3
-
Dynamic mac address learning.
3. Configure port security on interface Fa 0/3 of the switch with the following settings :
-
Port security enabled
-
Mode : protect
-
Static mac address entry : 00E0.A3CE.3236
Configuration & Verification
First, to communicate among hosts, you should turn all interfaces to 'up' status with the no shutdown command.
Shutdown Mode
For now, let's apply the shutdown mode to FastEthernet 0/1:
Switch(config)#int fastEthernet 0/1
Switch(config-if)#switchport mode access
Switch(config-if)#switchport port-security
Switch(config-if)#switchport port-security maximum 3
Switch(config-if)#switchport port-security mac-address sticky For your information, setting sticky means Port Security learns MAC addresses dynamically, and the MAC address table remains even when rebooting.
After populating the MAC address table to its maximum value of 3, connect the new laptop namedROGUE to the Hub-PT.
Then, you can see that the FastEthernet 0/1 is turned down as follows:
Protect Mode
Restore the configuration on FastEthernet 0/1.
Now, the ROGUE laptop can send ICMP traffic to the 192.168.1.4 connected to FastEthernet 0/2:
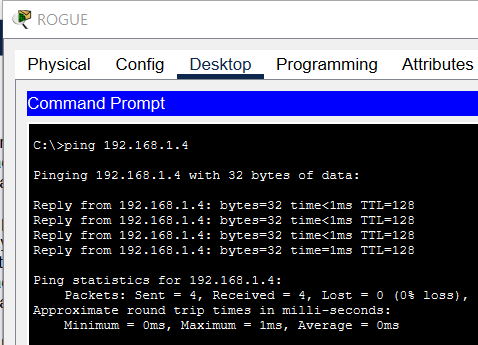
Apply the protect mode to FastEthernet 0/1:
Switch(config-if)#switchport port-security violation protectTry sending ICMP traffic from theROGUE laptop to 192.168.1.4 again now, it will be blocked by Port Security:
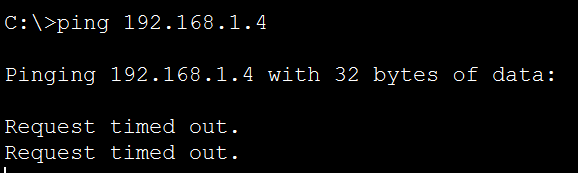
The FastEthernet 0/1 is also not turned down:
Restrict Mode
Its functionality is basically the same as the protect mode.
Additionally, it can alert an administrator about any violations.
