SSL/TLS
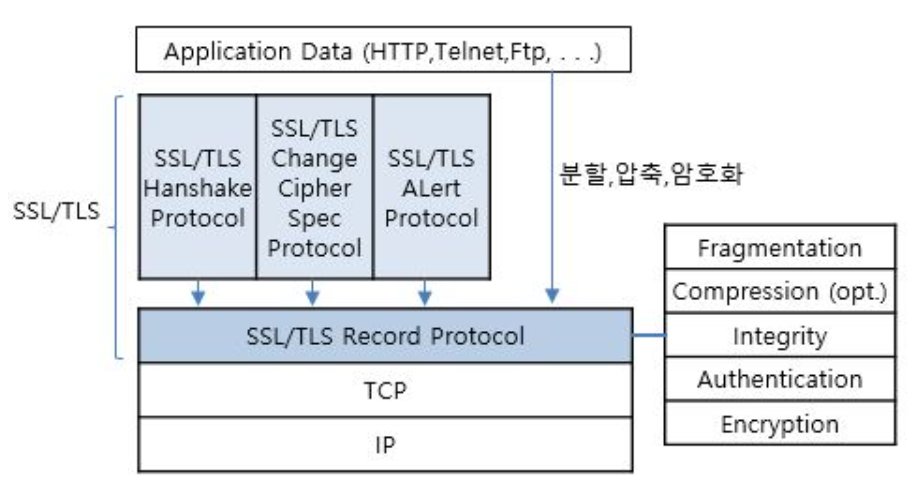
Secure Sockets Layer/Transport Layer Security (SSL/TLS) is a cryptographic protocol in the Transport Layer designed to encrypt data in the Application Layer for secure transmission.
Its functionality encompasses HMAC for integrity, RSA certificates for Authentication, encryption mechanisms for confidentiality, and more.
Handshake
Before communicating between hosts, SSL/TLS must take a handshake procedure to negotiate security parameters.
The handshake procedure varies depending on the TLS version. TLS 1.2 is a widely known standard. TLS 1.3 is a more streamlined version.
The aim of this post is to understand the handshake procedure, so let's go through each step of the TLS 1.2 handshake process.
Three-way Handshake
Because SSL/TLS is a TCP protocol, it must undergo this process initially to establish a session:
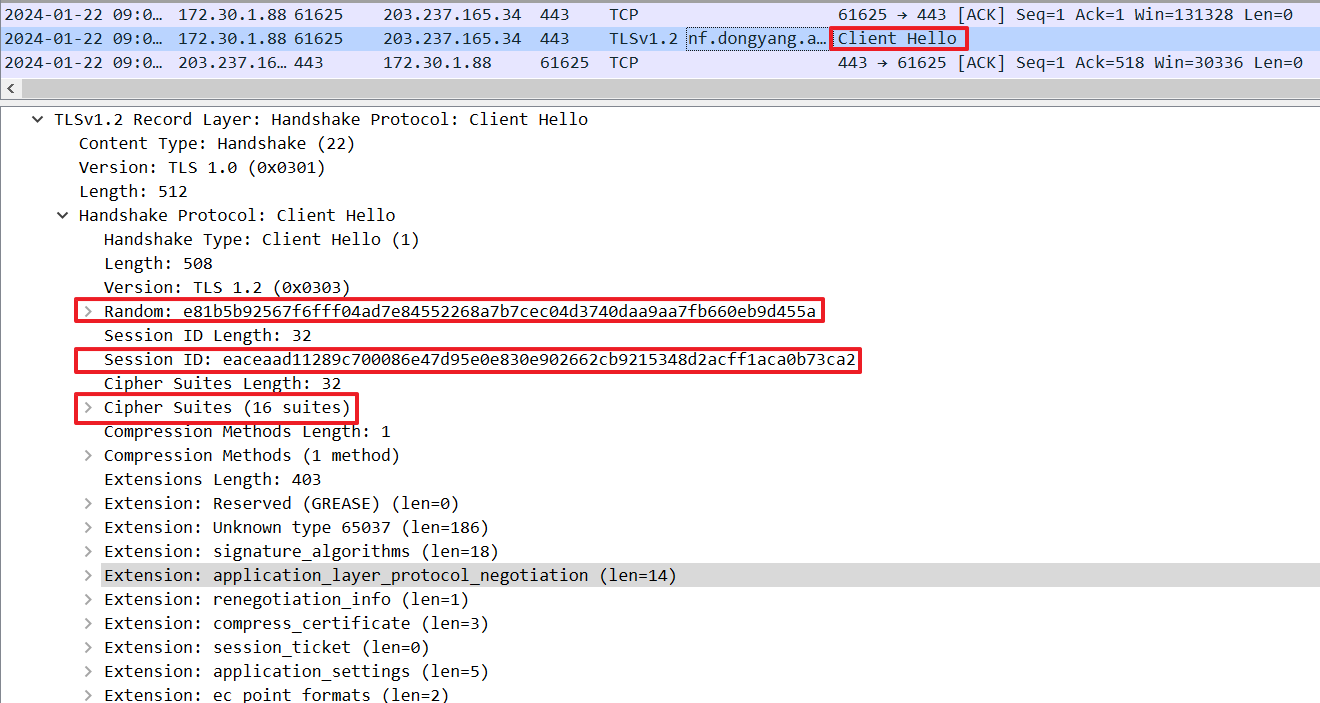
Client Hello
For specifying security parameters, a client sends available security options to a server, including a random value for creating a master secret later, Cipher Suites for key exchanges and authentication, Session ID for identifying clients by a server, and so on:
Server Hello
A server sends back Server Hello to the client.
Server Hello involves the server's random value, which is also needed to create the master secret, and the Cipher Suite chosen by the server from among the client-available cipher methods:
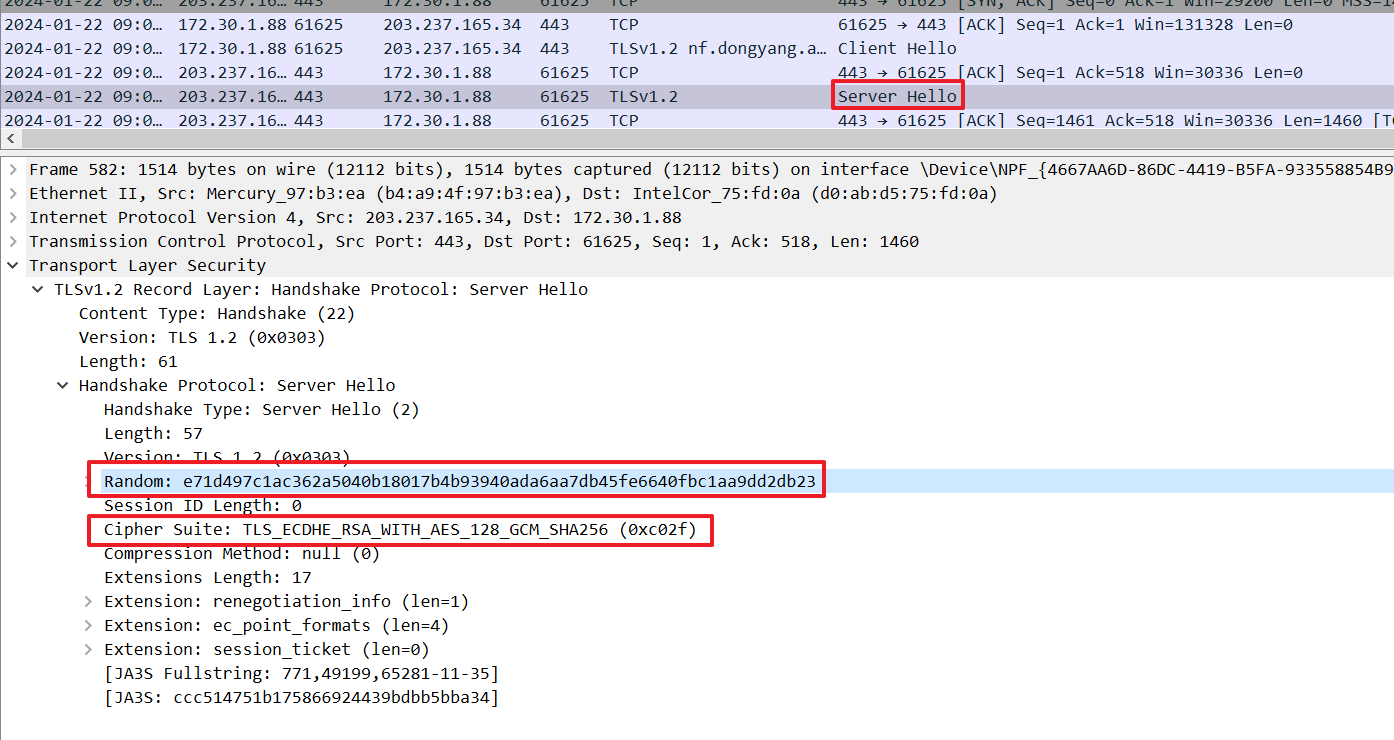
The value of the server-chosen method is TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384.
The term ECDHE indicates that Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) will be used for key exchanges.
Certificate authentication will be via RSA, and AES256 in GCM block mode will be employed for data encryption. Hash-based Message Authentication Code (HMAC) will utilize the SHA384 algorithm.
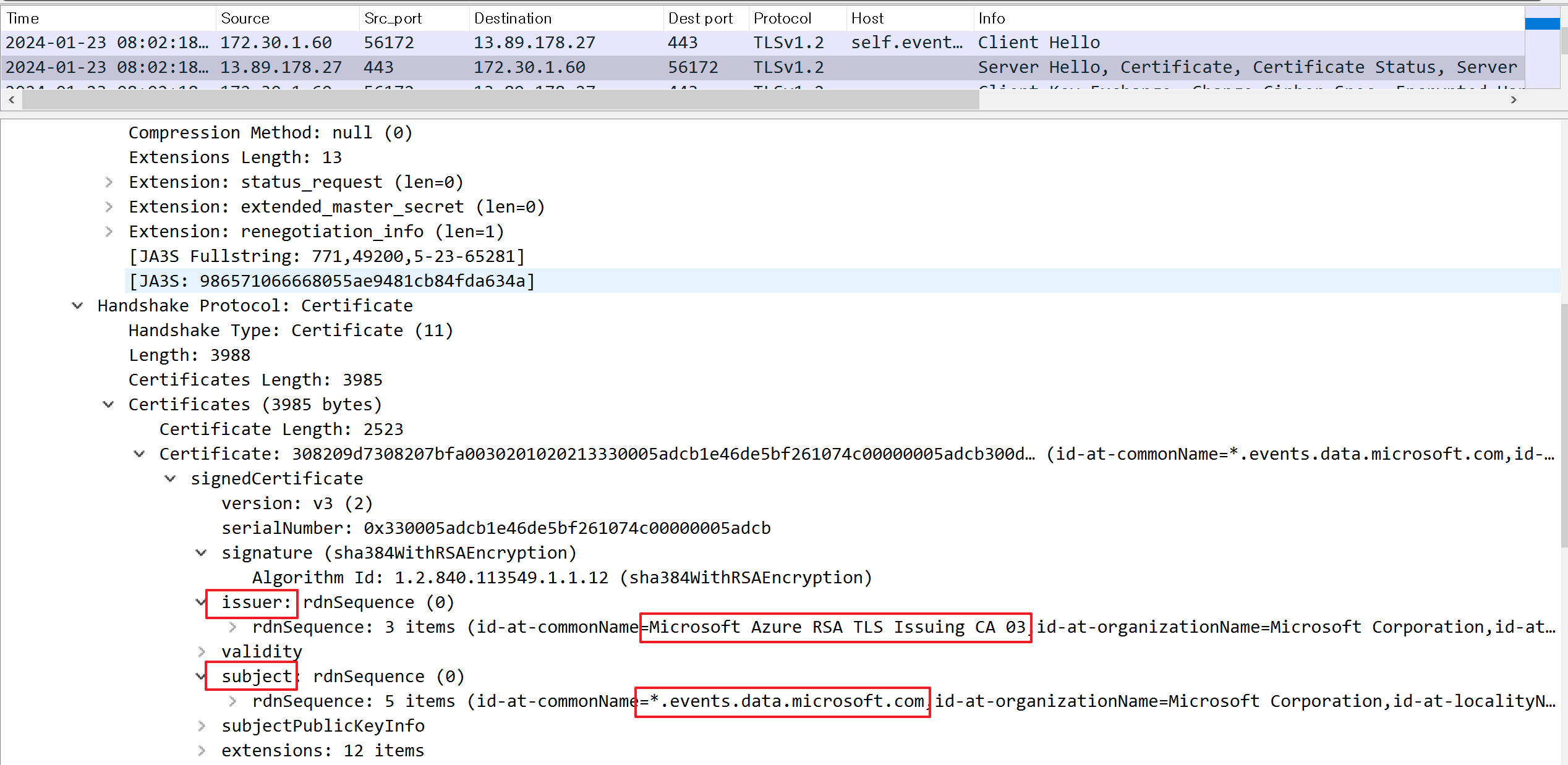
Certificate
The server then sends the certificates for authentication itself. The transmitted list includes both the server's certificate and the certificates of the higher authorities that have issued the server's certificate:
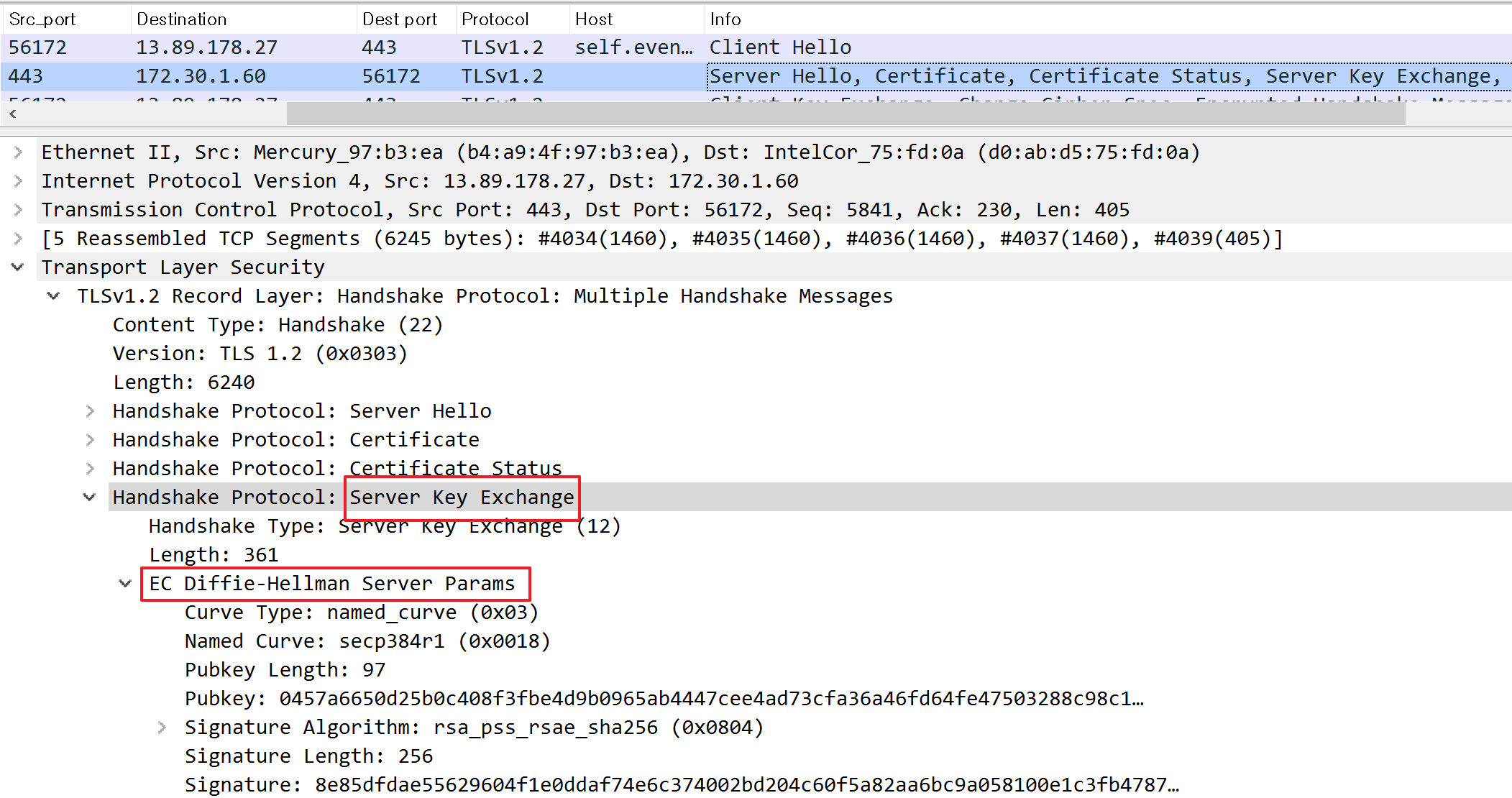
Server Key Exchange
The server also transmits parameters for the key exchange process when either Diffie-Hellman or ECDHE is employed as the key exchange algorithm. If not, this step is not carried out:
Server Hello Done
To inform the client that the server has transimitted all security parameters, the server sends this message to the client.
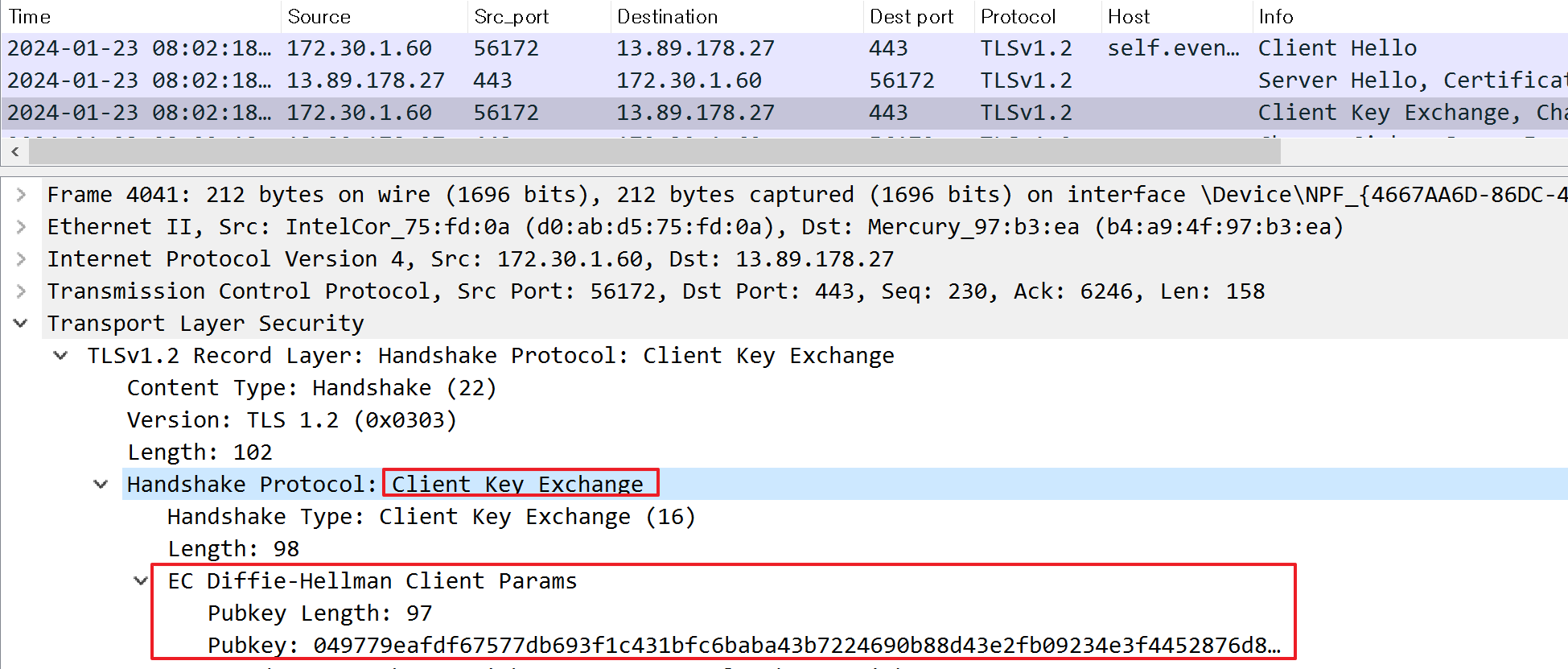
Client Key Exchange
The client creates a premaster secret used for creating a master secret later, then sends it in this procedure.
If the key exchange algorithm is RSA, the client generates a random value as the premaster secret:
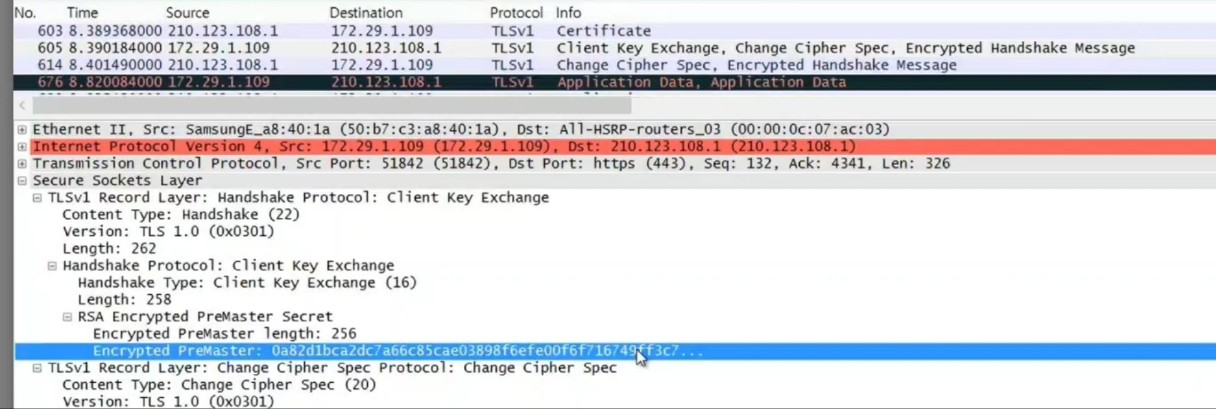
If the key exchange algorithm is either Diffie-Hellman or ECDHE, the client sends key parameters.
Afterward, each the server and client creates the premaster secret individually through calculations based on key exchange algorithms:
Change Cipher Spec, Finished (Encrypted Handshake Message in Wireshark)
These messages inform the counterpart that its SSL/TLS configuration has been completed: