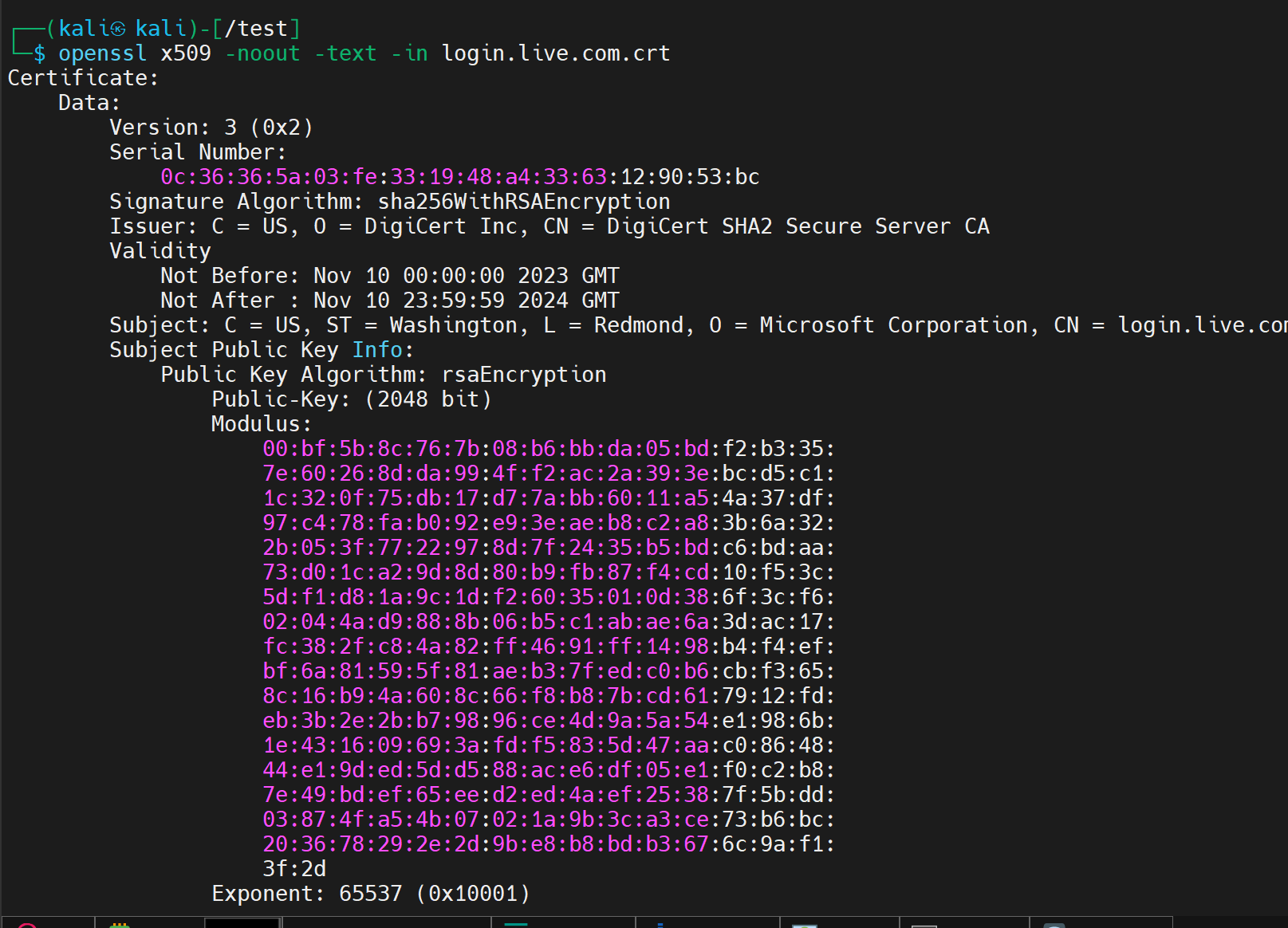
X.509
X.509 is a standard format for defining certificates used in Public Key Infrastructure (PKI).
At present, X.509 can be regarded interchangeably with a public key-based certificate.
An X.509 certificate contains identities of an issuer and a subject (a hostname, or an organization, or an individual) and a public key of a subject (RSA, DSA, ECDSA, etc.) for data encryption, as well as its signature signed by a higher CA.
These details can be displayed through the openssl command:
Signature Validation
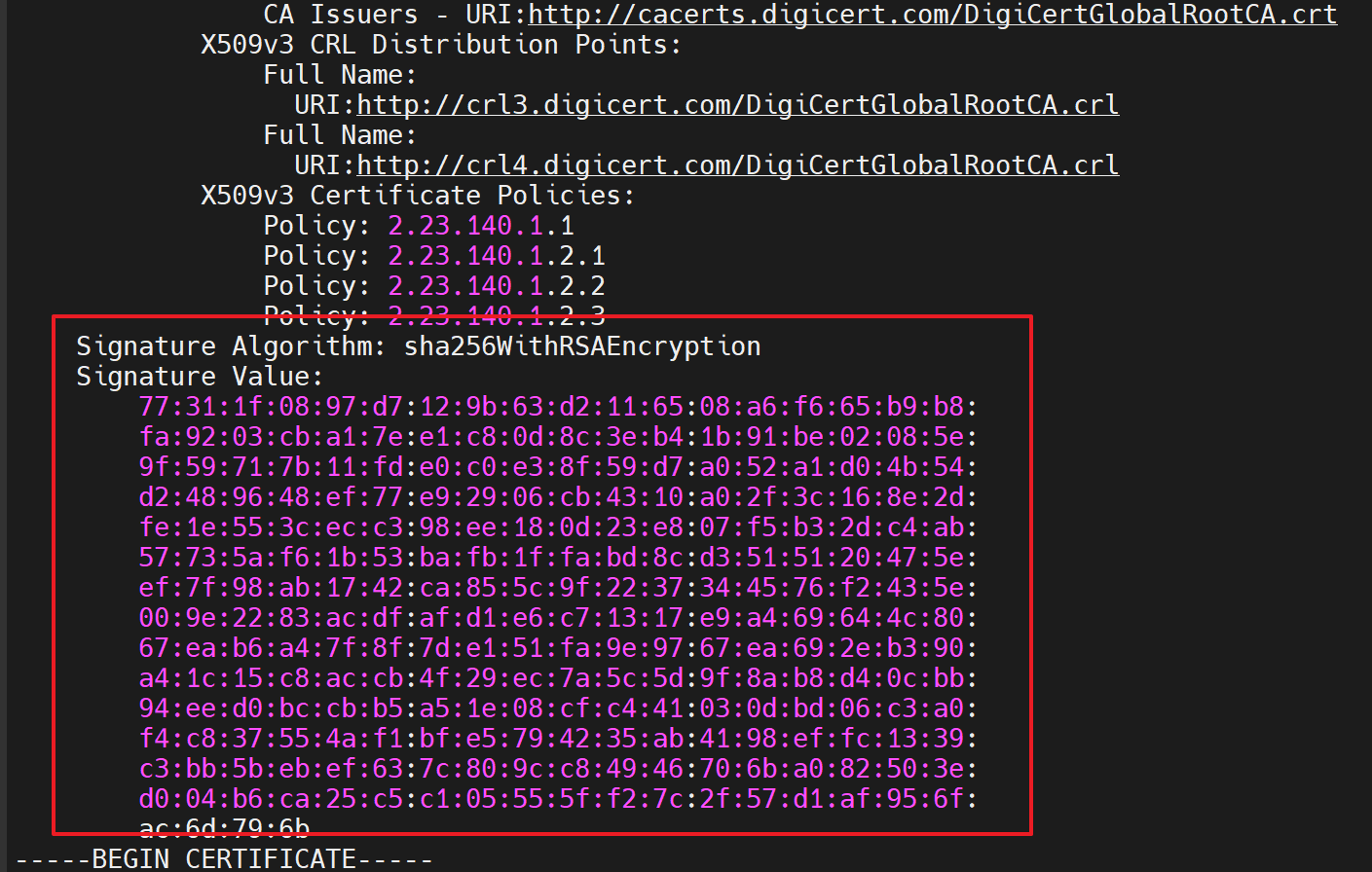
The signature of a certificate is the result of hashing and encrypting its identities with a private key of the higher-level Certificate Authority (CA).
Therefore, signature validation is simply to decrypt the signature value with the public key of the higher-level CA.
The signature value can be verified using the previously mentioned command:
File Extensions
An X.509 certificate presents various formats based on extentions.
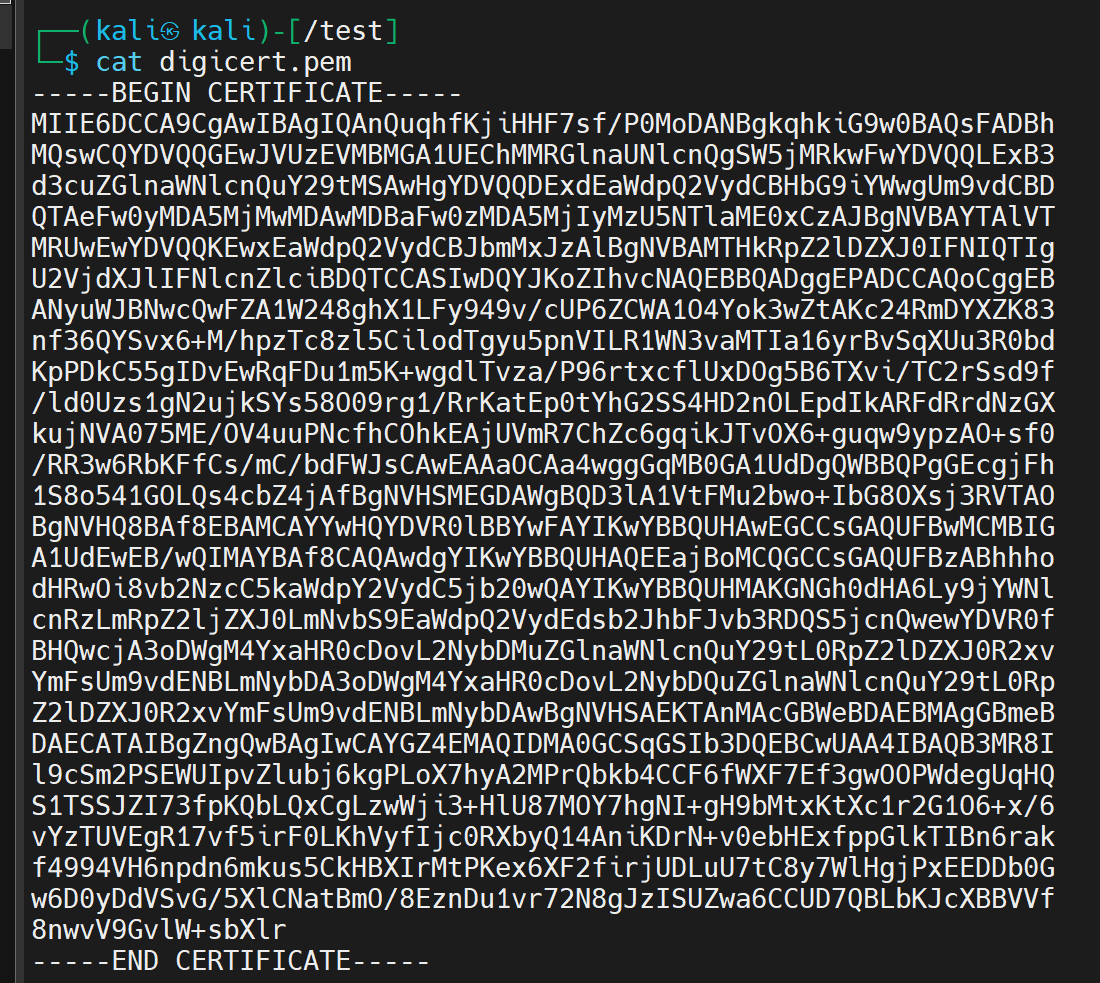
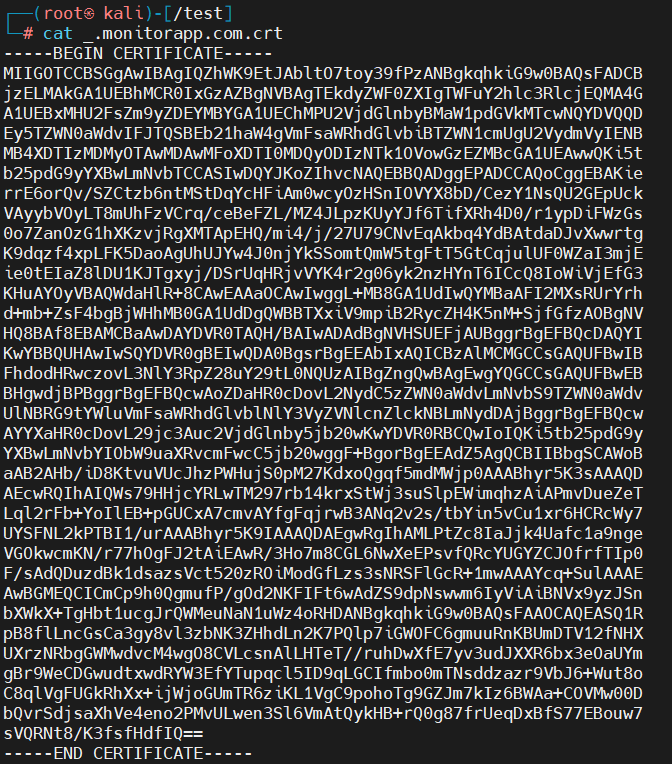
.pem is a commonly used extension containing base64-encoded ASCII text about the certificate's content:
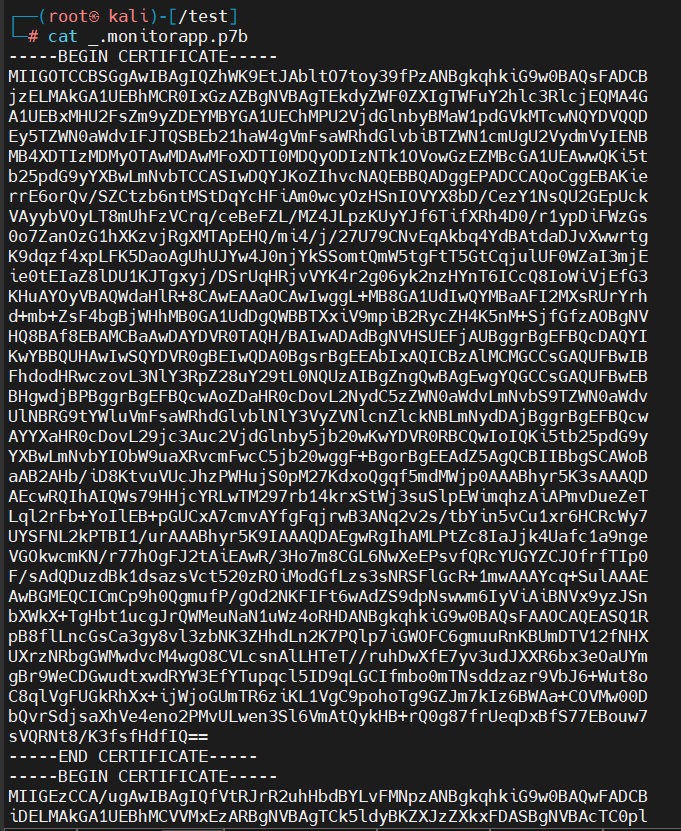
.p7b contains all certificates in a certificate chain while .crt only indicates one specific certificate:
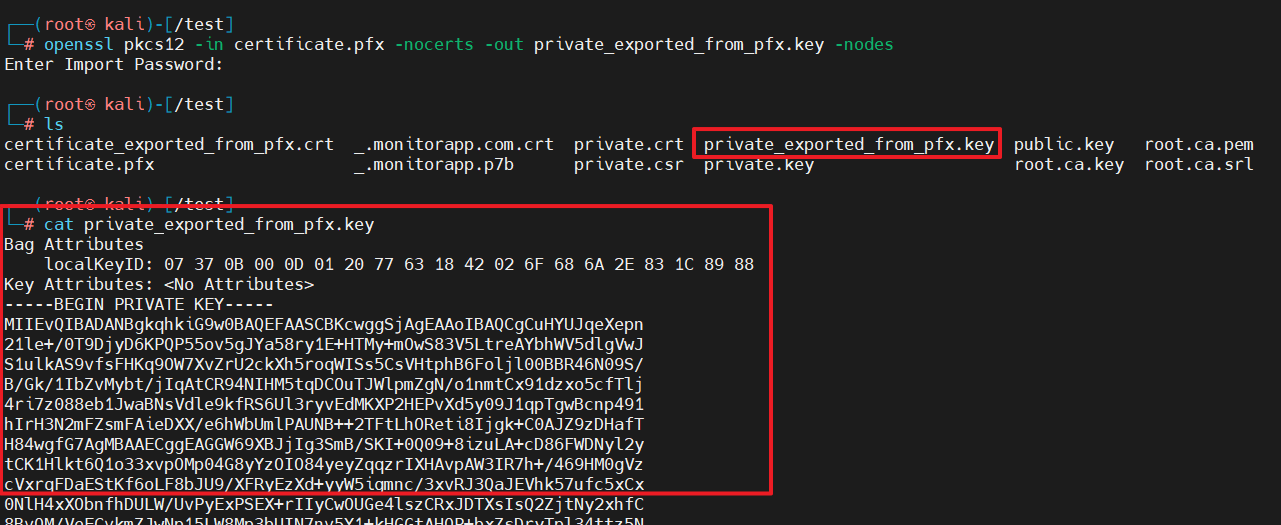
.pfx includes the private key of a certificate, so it is possible to export the private key from the .pfx certificate as follows:
All file extensions are used for various purposes, according to specific needs, each of which is encoded in a separate manner and can be converted to the others, as in the following command:
openssl pkcs7 –inform DER –in www.monitorapp.com.p7b –print_certs –text –out www.monitorapp.com.pemFor more details, please refer to the following link:
https://www.sslcert.co.kr/guides/kb/54
Certificate Chain
Certificate chains are used to check that the public key and data in a target certificate effectively belong to its subject. In order to ascertain this, the signature on the target certificate is verified by using the public key contained in the following certificate, whose signature is also verified using that certificate, and so on until the last certificate in the chain is reached.
The certificate chain consists of three types of members : an end-entity certificate, intermediate certificates, and a root certificate. To check end-entity certificate, validation is repeated through the certificate chain until the root certificate is verified.
