System Security
1.Overview of Operating System(1)
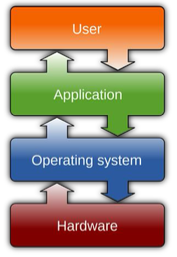
UNIX: Free BSD, AIX, HP-UX, System V, Solaris LINUX: a variant of UNIX Windows 7, 10, 11, Windows Server 2019Android Marshmallow, Nought, 8, 9, ... ma
2.Overview of Operating System(2)
핵심 서비스가 존재하는 커널 안에 protection and security라는 영역이 존재한다. Authentication, ownership, restriced access Loggin and Security regulations보안이 매우 중요한 시스템에서는 모든
3.Linux Security Basics(1)
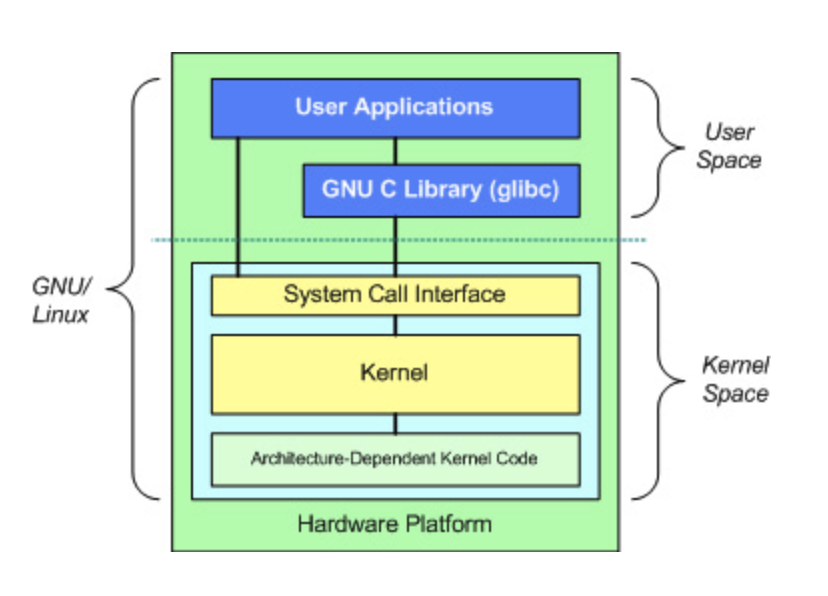
1. Linux OS Linux OS OS provides interfaces between H/W and Users & Apps Standards utility programs and Standard library include library's header Uti
4.Linux Security Basics(2)

system에 존재하는 모든 사용자 계정 정보를 저장하는 텍스트 파일 file format, layout, field의 의미 확인 사용자가 자신의 비밀번호를 변경할 때 사용하는 실행 파일 In Linux, each user is assigned a unique user
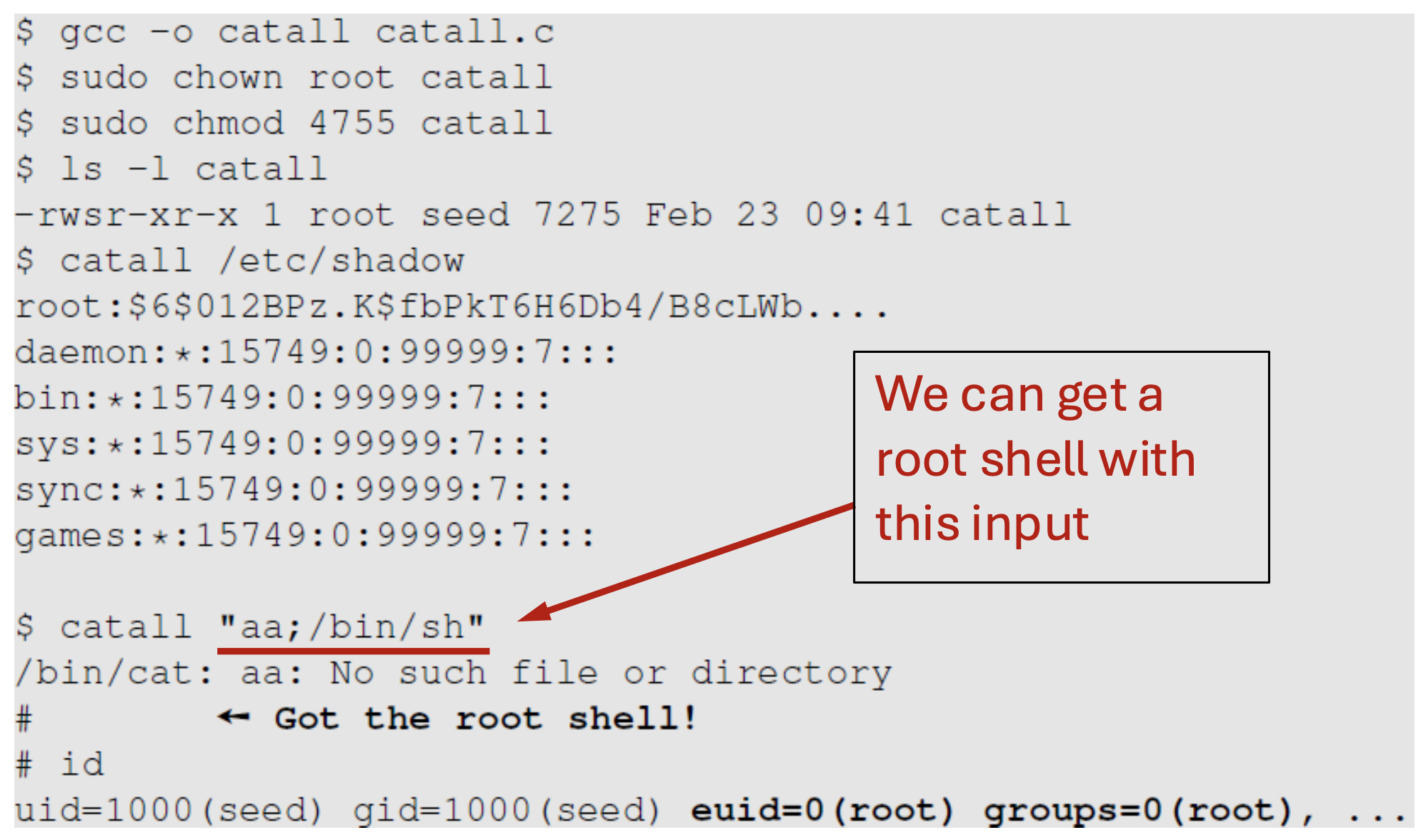
5.Set-UID Privileged Programs(1)

Need for Privileged Programs Password Dilemma Permissions of /etc/shadow File How would normal users change their password? 대부분의 리눅스 시스템에서 '/etc/sha
6.Set-UID Privileged Programs(2)
Invoking Programs Invoking external commands from inside a program External command is chosen by the Set-UID program Users are not supposed to provi
7.Shellshock
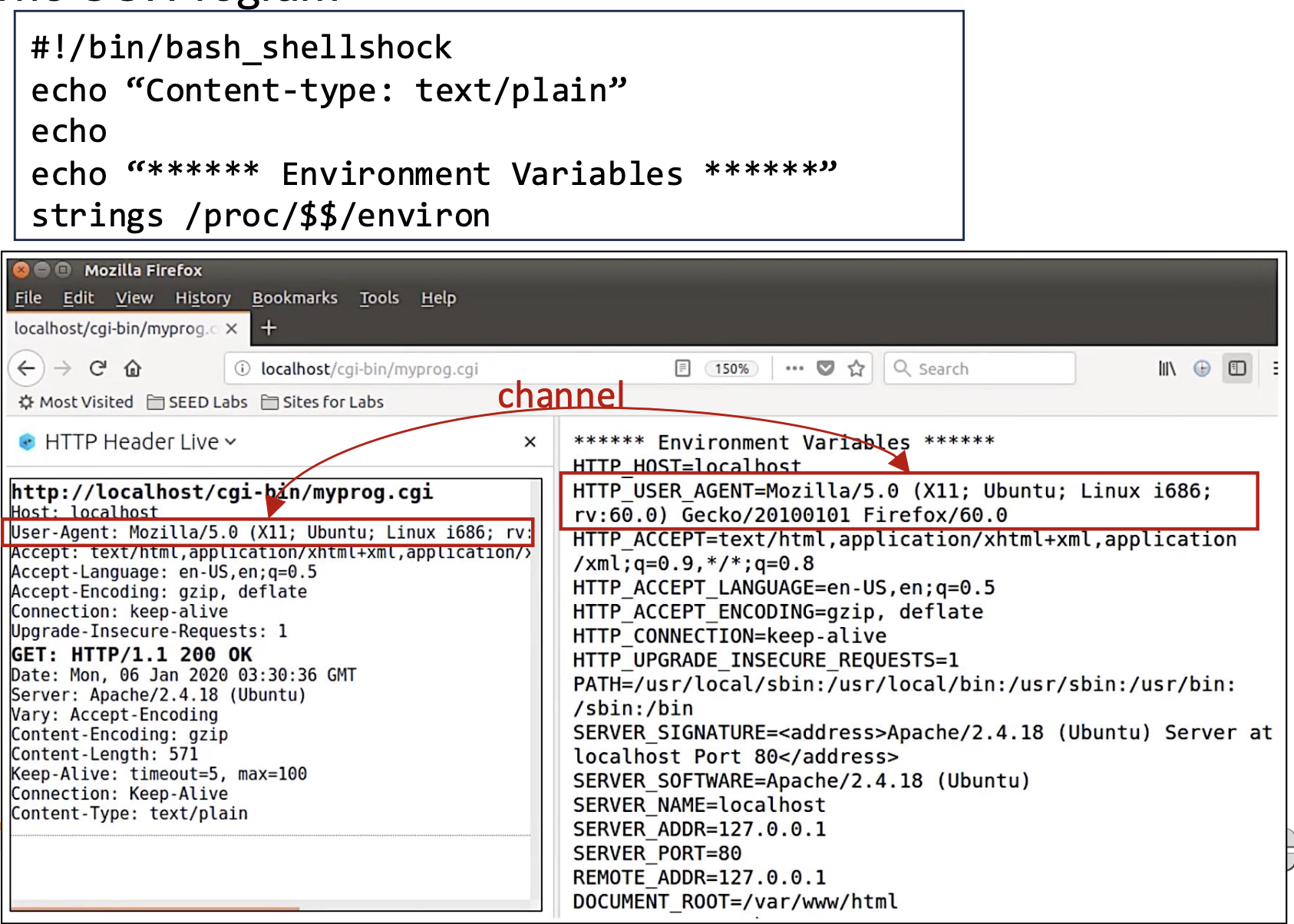
Shellshock: Introduction September 24, 2014 Vulnerability in Bash Related to Environment variable CGI(Common Gateway Interface) and Web Defining
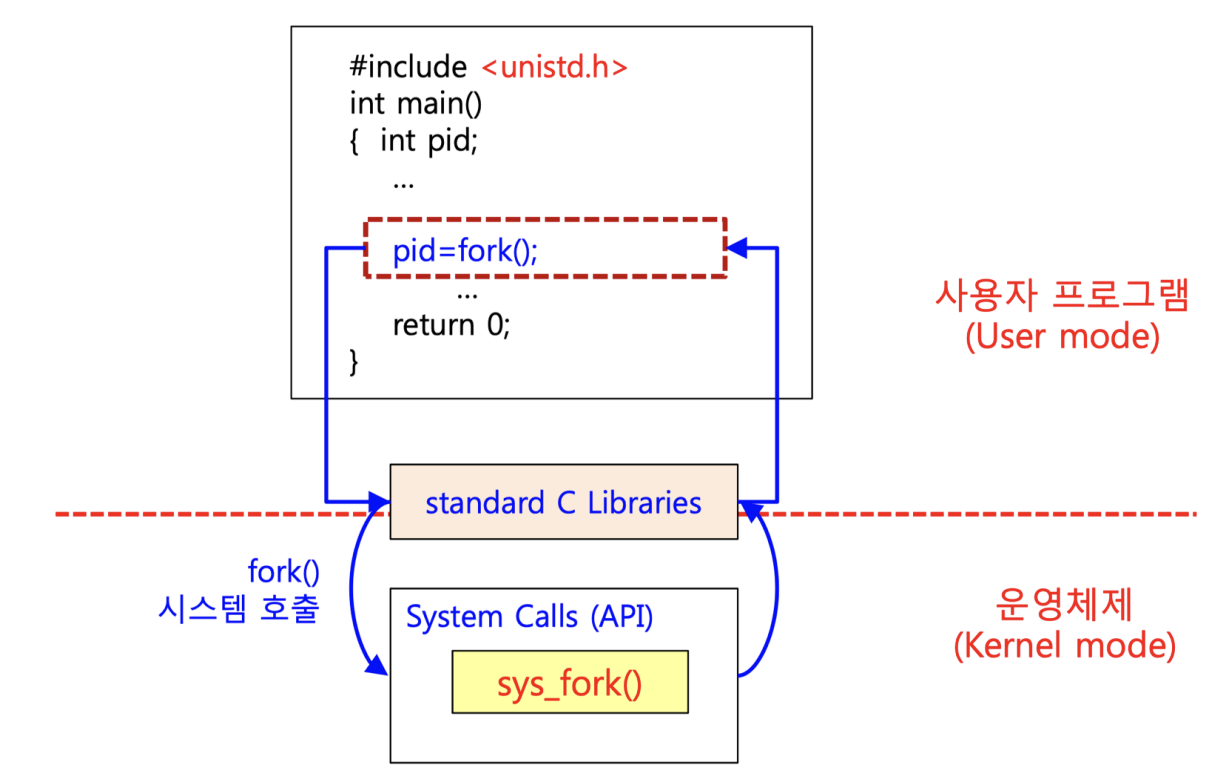
8.Assembly Language Basic

80x86 system's CPU & Register 80386 이전 세대에 비해 크게 확장된 수치인 4GB 물리 메모리 사용 32-bit register Computer system architecture 저장 장치의 크기 순 HDD RAM Register In
9.Shellcode
Ubuntu 20.04 vscode, gcc, gdb ATT: 앞에서 뒤로 대입 Assembly basic analysis push %ebp 최초의 ebp 값을 스택에 저장 ebp 바로 전에 ret 저장, 함수 종료 시 점프할 주소인 이전 eip 저장 ebp는 함
10.Buffer Overflow Attacks(1)

Virtual address vs. physical address 32-bit OS는 각 프로세스마다 4GB의 가상 메모리 공간이 할당되고, OS는 실제 물리 메모리와 매핑하는 정보를 테이블로 관리한다. .exe 파일은 windows에서 사용하는 실행 파일 형식 P
11.Buffer Overflow Stacks(2)

New address in return address Considerations The new address in the return address of function stack should not contain zero in any of its byte, or th
12.Control Hijacking Attacks (1)

Control hijacking attacks Control flow Order in which individual statements, instructions of function calls of a program are executed or evaluated Con
13.Control Hijacking Attacks (2)

Return-to-libc의 overwrite 상황을 가정하면, 기존 frame의 ret(pop eip), call(push eip)가 무시되고 원하는 함수의 prologue로 넘어간다. ret(pop eip): esp가 한 칸 증가, ebp는 유지함수 B(system
14.Control Hijacking Attacks (3)

빨간 박스는 라이브러리 함수인 'printf'의 일부 disassemble 결과 함수 시작에는 push ebp & mov ebp, esp와 같은 prologue가 등장하는데, 여기서는 그런 코드 없이 바로 'get_pc_thunk'가 실행되어 전통적인 스택 프레임 패턴
15.Access Control

Discretionary는 '자유 재량의'라는 뜻으로, DAC는 파일 소유자가 다른 사용자들에게 어떤 권한을 줄지 직접 결정하는 방식이다. 리눅스에서는 이러한 권한이 'rwx'로 표현되고 user, group, others에 대해 각각 별도로 설정된다. Subject,
16.Network Security Basics

IP Address: the Original Scheme Calssful Addressing Scheme (1981 - 1993) IPv4 주소는 32비트 CIDR Scheme: Classless Inter-Domain Rounting 1993 ~ IP주소/접두사길